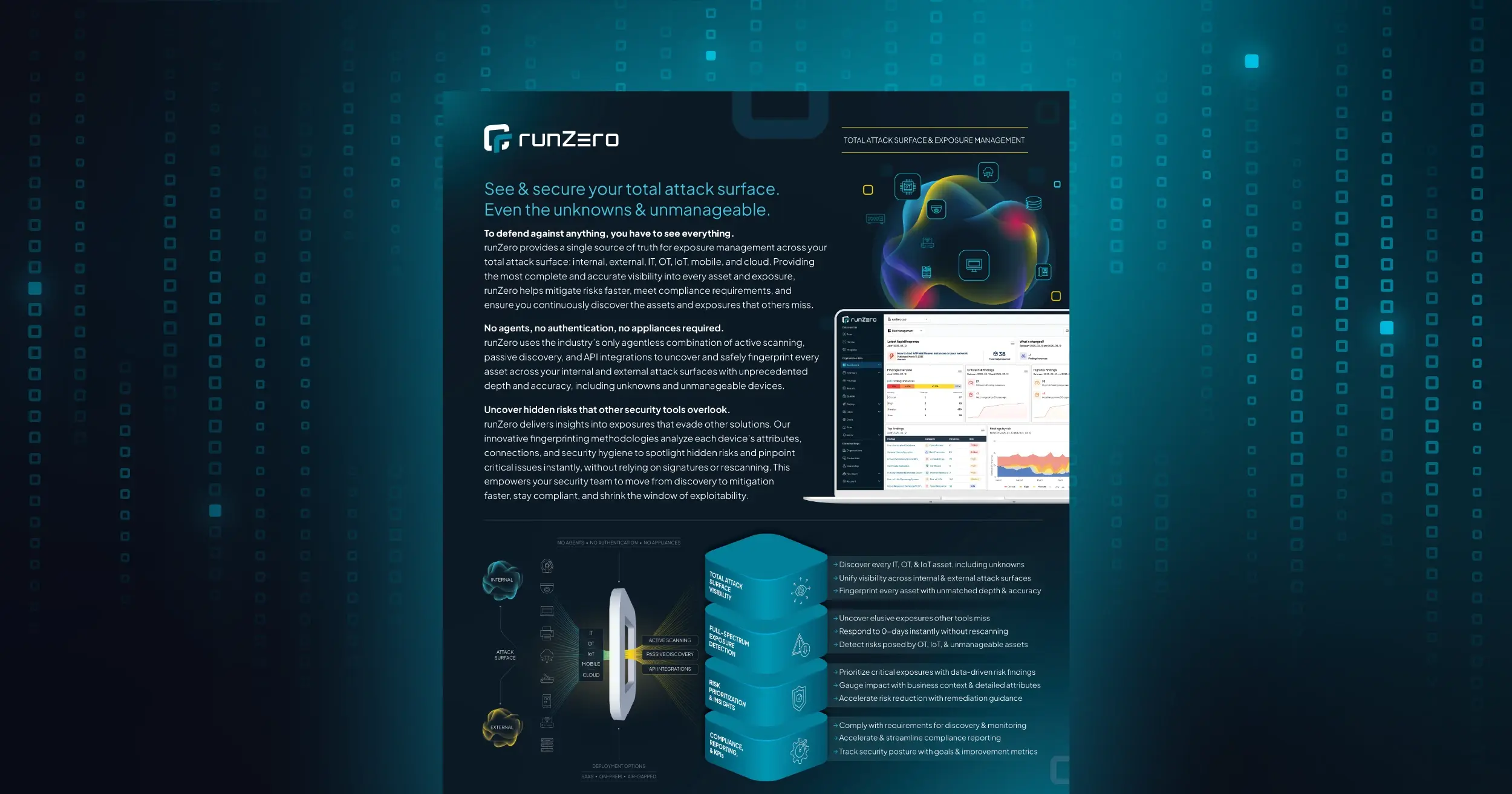
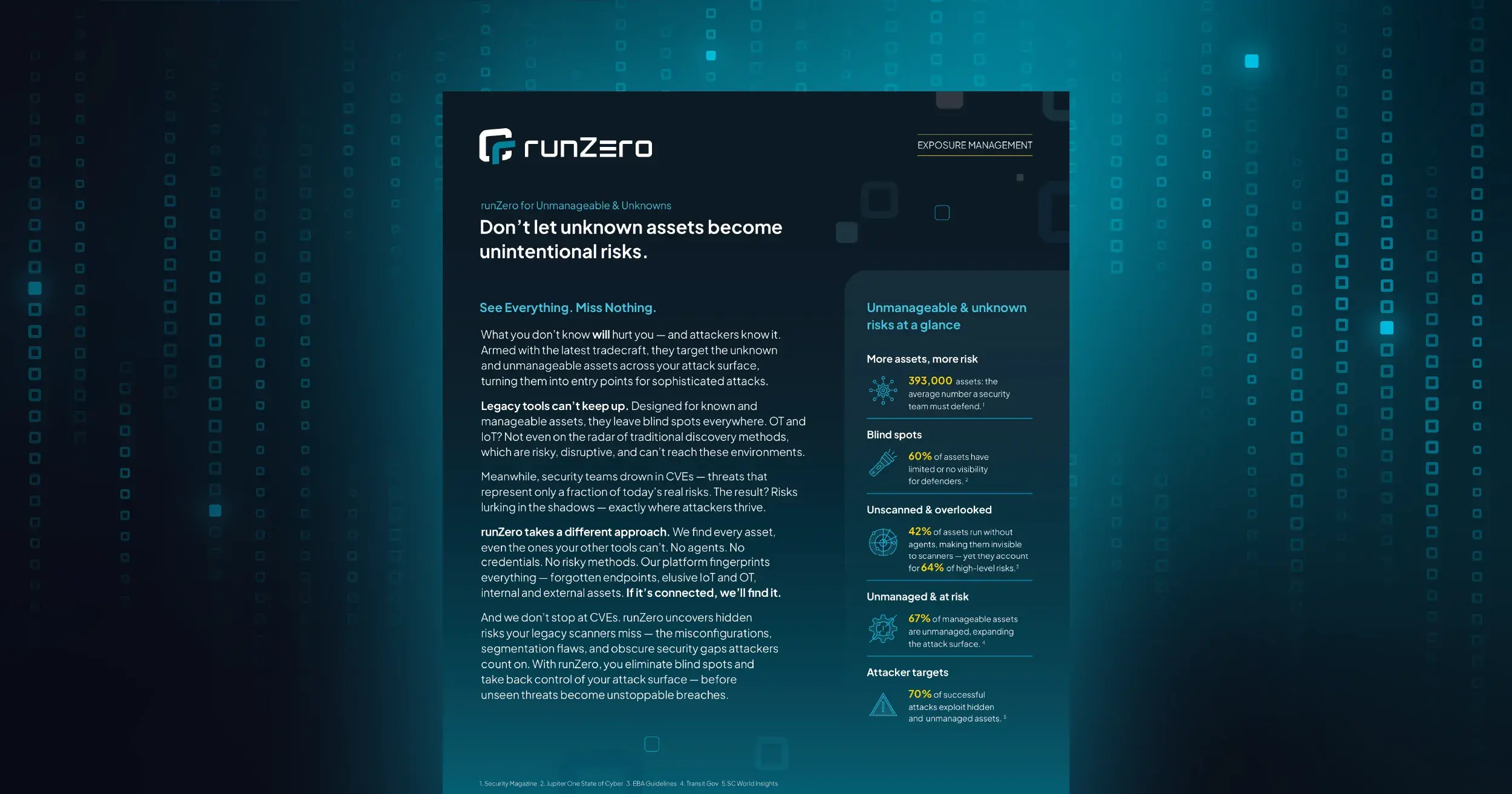
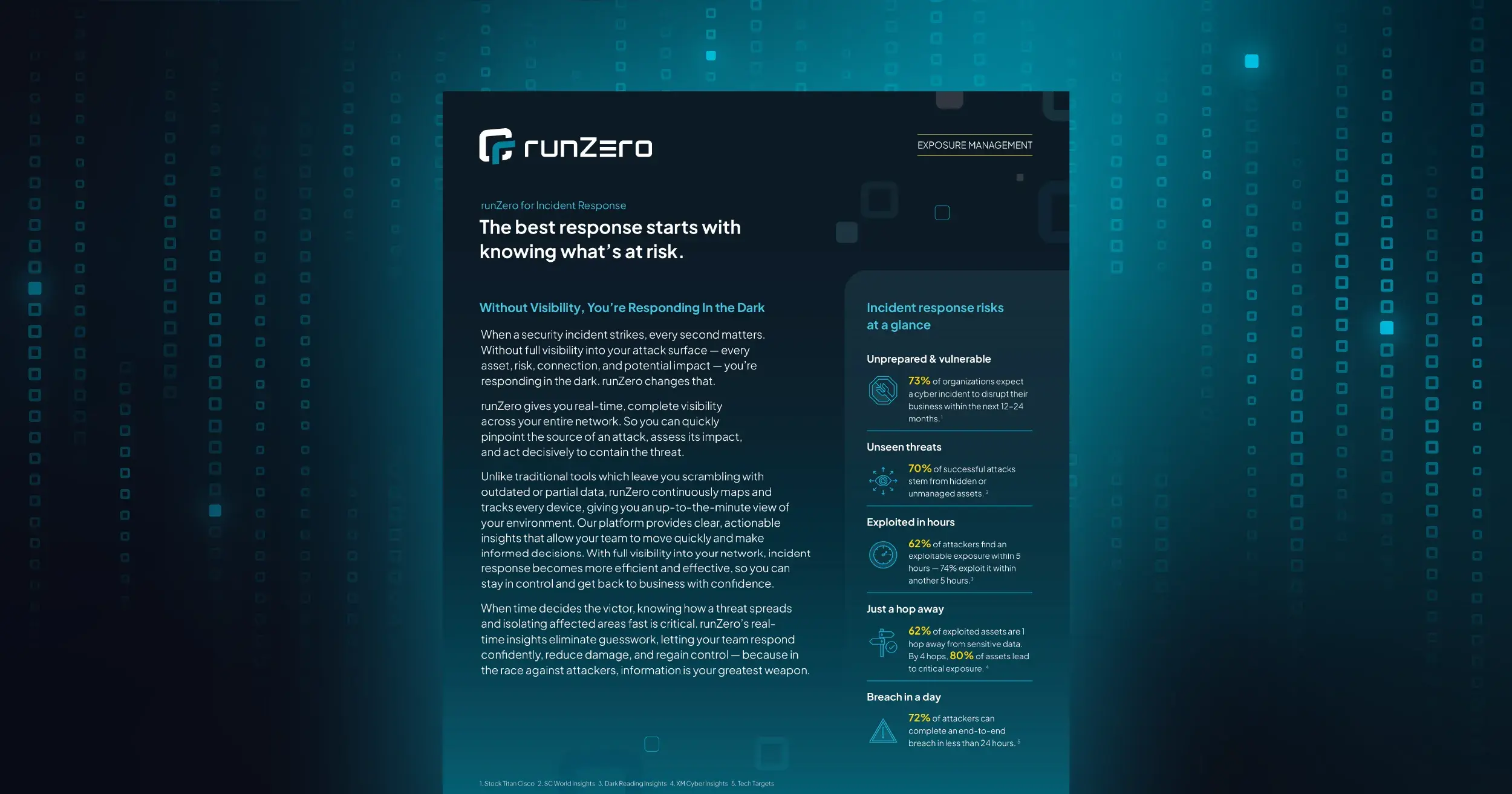
The recent zero trust-related executive orders are an acknowledgment that the threats to public sector infrastructure have never been greater. But agencies can’t fulfill the zero trust challenge without seeing and securing 100% of their connected assets.
Implementation of a strong zero trust security architecture now requires that you also apply zero trust principles to the multitudes of managed and unmanaged IT, OT, IoT, mobile, and cloud assets that pervade the modern enterprise. Additionally, subsets of these assets don’t support security agents, don’t produce logs, and aren’t easily patched. To realize the full promise of zero trust, you need specialized capabilities that deliver comprehensive visibility into every asset. And those capabilities must integrate with your existing zero trust tools and processes.
Download our solution brief to learn more.