

The State of Asset Security:
Uncovering Alarming Gaps & Unexpected Exposures
As a leading exposure management platform, runZero has a unique, insider’s perspective on the state of asset security. Our research team analyzed hundreds of enterprise networks, including internal infrastructure, internet-facing assets, and cloud environments.
We wanted to better understand today’s attack surfaces, exposure patterns, and emerging threats. Our research reveals alarming gaps and unexpected trends, including the decay of network segmentation, persistent challenges in attack surface management, and an increasing volume of dark matter on modern networks.
Download the report for full details.


Highlighted Findings
Deciphering today's security challenges.
The security landscape is morphing at an unprecedented pace, while attack surfaces expand exponentially. Here are some trends we uncovered to help security teams focus their limited resources in the right places:

Be Wary Of Unusual Assets.
Outlier devices are often the most at-risk devices.
The runZero outlier score, defined as how unique an asset is within the context of its neighbors, strongly correlates with the risk ranking reported by leading vulnerability scanners. This correlation works both ways, with low outlier scores consistently mapping to lower overall risk. Defenders can leverage outlier analysis to quickly identify the most vulnerable systems within their environments.

(Almost) Everything Is A Router.
Printers and network-attached storage devices frequently break network segmentation controls.
We found that printers and network-attached storage devices often allow traffic forwarding between networks, breaking network segmentation controls. runZero identified unexpected IP-forwarding behavior across dozens of device types, ranging from smart TVs to robotic vacuum cleaners.
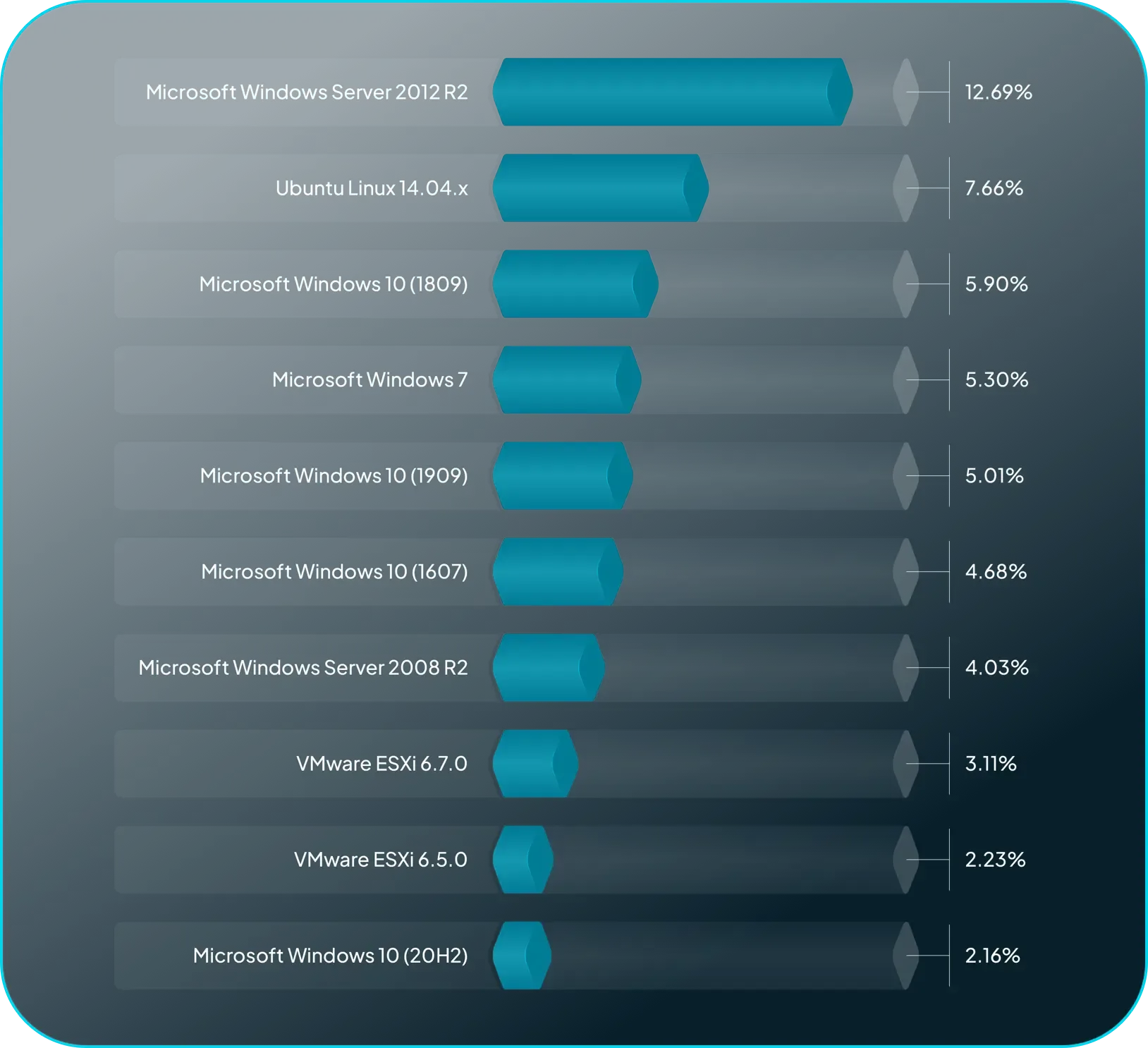
Outdated Systems Add Unnecessary Risk.
End-of-Life hardware & operating systems continue to drag down security postures.
Operating systems (OS) typically have iterative phases of vendor support that provide updates and patches. While vendor support has an expiration date known as end-of-life (EOL), this is not the end if an OS is left lurking on the attack surface. Although Windows 2012 R2 and Ubuntu 14.04 are the most common EOL operating systems observed, obsolete versions of VMware ESXi and out-of-support network devices are serious concerns.
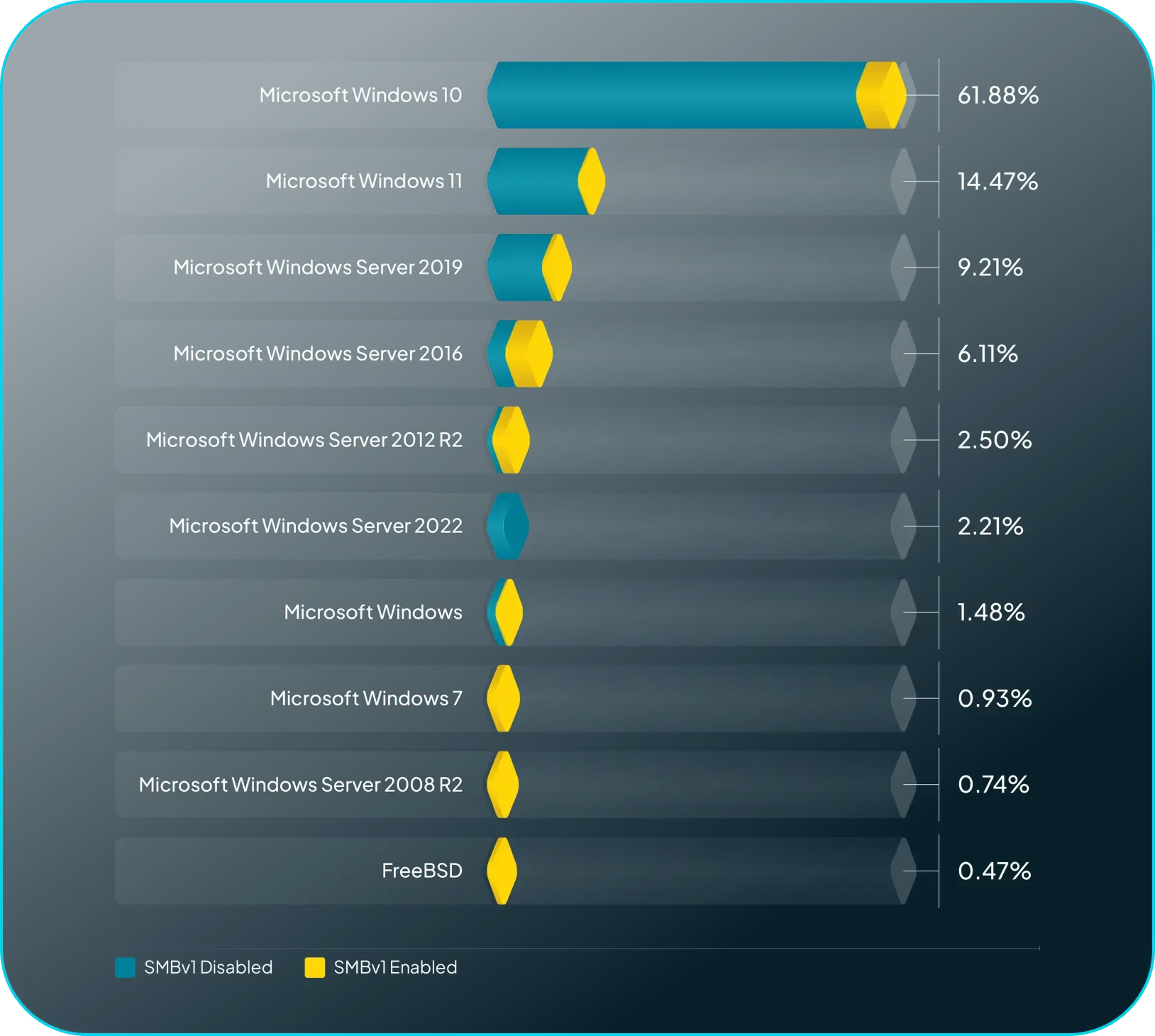
Fingerprinting Uncovers Old, Sketchy Protocols.
Server Message Block (SMB) v1 is still enabled on 12% of Windows systems.
The SMB protocol is a security dinosaur stretching back to 1983. The protocol has evolved greatly over the years with more secure versions, but SMBv1 continues to dot the threat landscape, riddled with security risks. While SMBv1 enabled services are in decline (likely due to Microsoft’s choice to disable the protocol by default), there are potentially still millions of legacy systems using this outdated protocol.
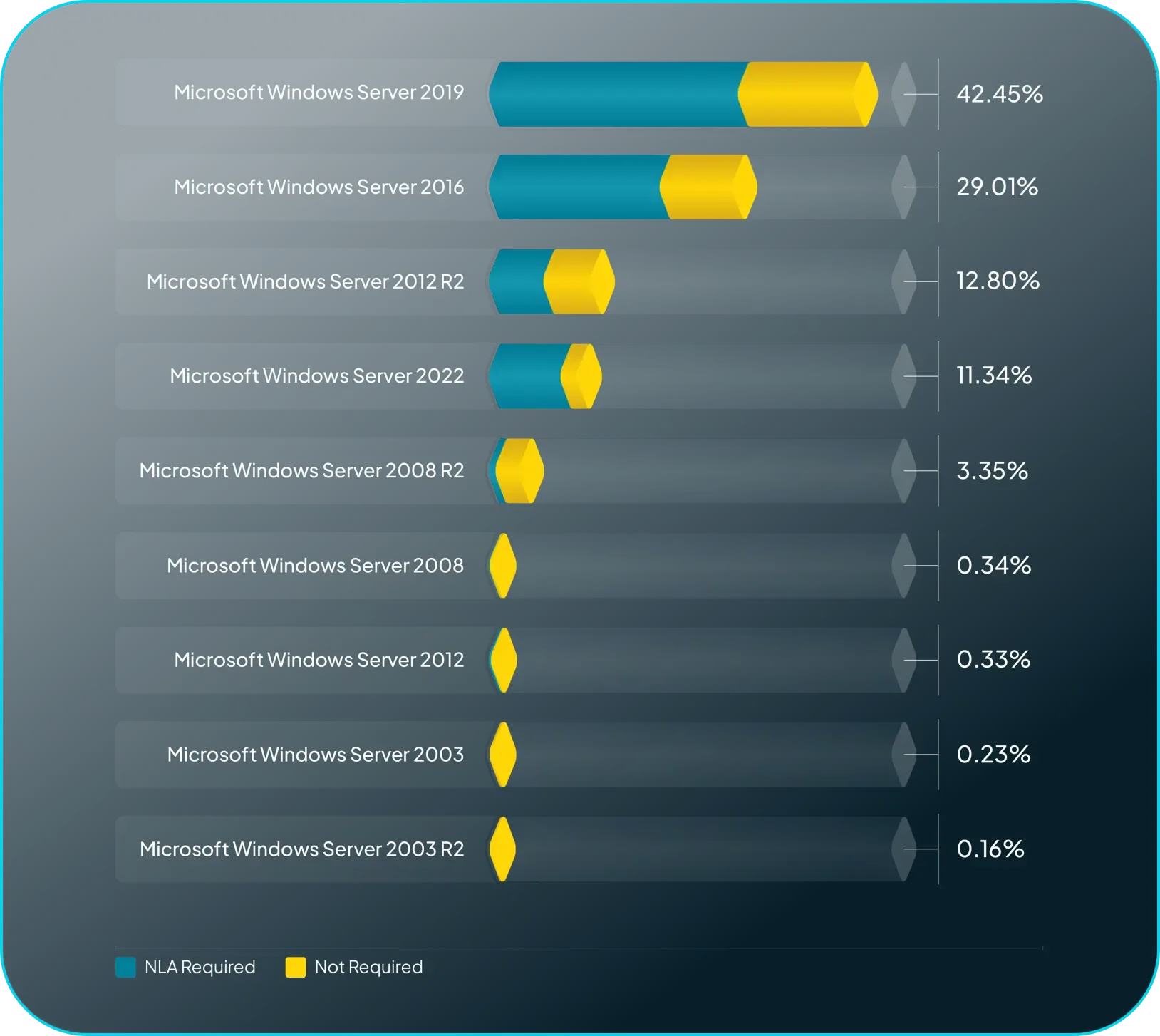
Verifying Security Default Enforcement.
Remote Desktop Protocol (RDP) security has improved on Windows with the introduction of NLA support.
Starting with Windows 2012, Network Level Authentication (NLA) was required by default when configuring Remote Desktop Services (RDS). runZero fingerprinting verified the majority of Remote Desktop services on Windows Server versions where NLA is required by default do actually require NLA, indicating that secure defaults can positively impact security.



Meet The Research Team
HD Moore is the founder and CEO of runZero. Previously, he founded the Metasploit Project and served as the main developer of the Metasploit Framework, which is the world's most widely used penetration testing framework.
Rob King is the Director of Security Research at runZero. Over his career Rob has served as a senior researcher with KoreLogic, the architect for TippingPoint DVLabs, and helped get several startups off the ground. Rob helped...
Tom Sellers is a Principal Research Engineer at runZero. In his 25 years in IT and Security he has built, broken, and defended networks for companies in the finance, service provider, and security software industries. He has...
More From The Research Team
Stay in the know
Get the latest discoveries from the runZero team in your inbox










