We’re thrilled to announce that new Risk Findings, Risk Prioritization Dashboards, and Risk Visualizations are now live in the runZero Platform!
Today's launch marks a new era in exposure management. You can read more about that here. Our goal is to more effectively manage the risk lifecycle, enabling you to find, prioritize, and remediate broad classes of exposures across internal and external attack surfaces, including those that evade traditional vulnerability scanners and external attack surface management solutions. By accelerating the detection and prioritization of the exposures that are most likely to be exploited, we can deliver better outcomes for you, our valued community.
These new capabilities cover the entire risk lifecycle, empowering you with clarity and context to prioritize critical issues and accelerate remediation like never before.
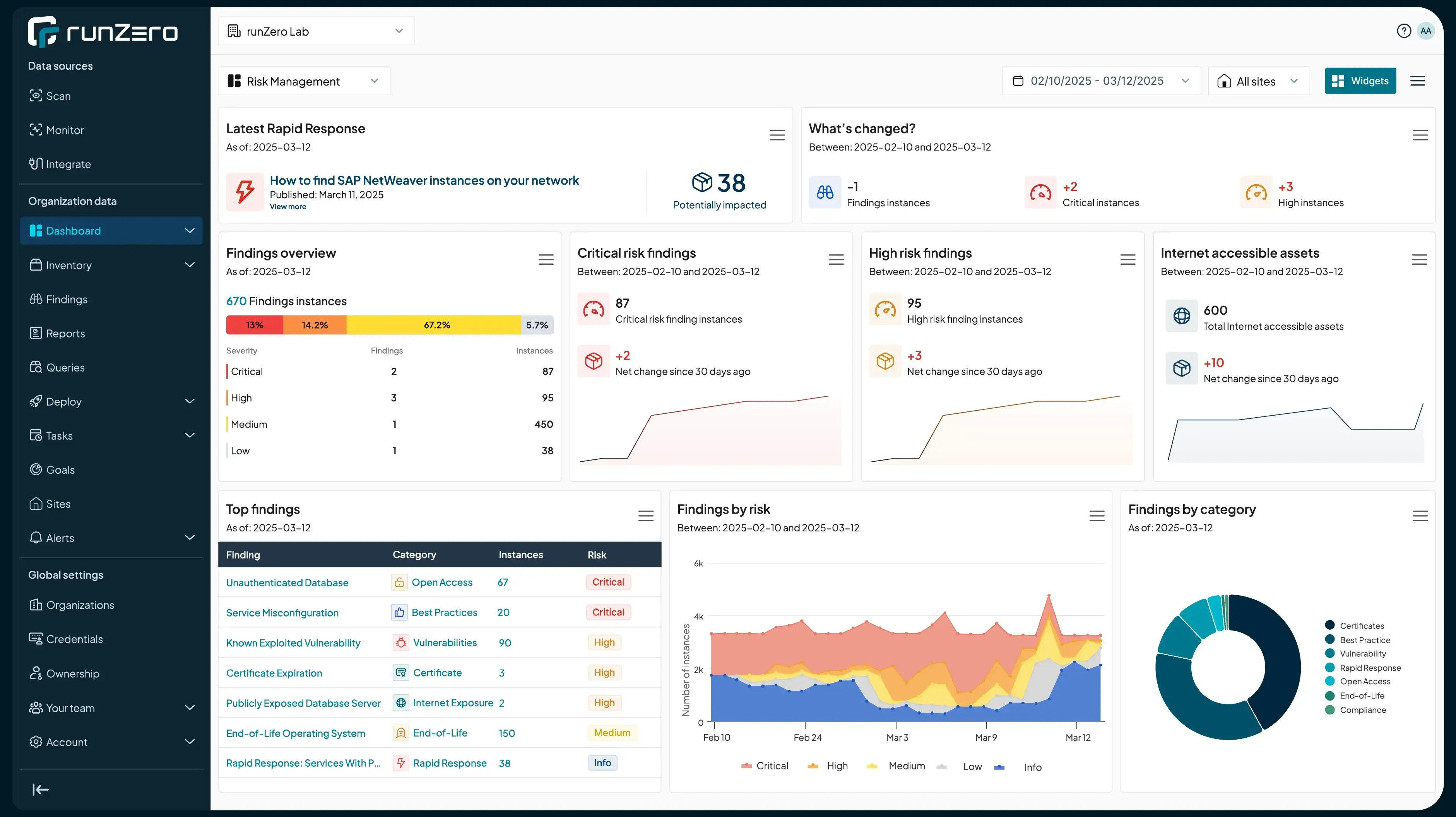
Risk Management Dashboard #
Your new command center for action. The Risk Management Dashboard is your centralized hub for taking action on risks, delivering actionable, data-driven insights with advanced findings widgets and customizable visualizations. As a cornerstone of runZero’s holistic exposure management, it provides comprehensive visibility and actionable context to help your team minimize exploitability windows, optimize resources, and reduce operational risks.
Key features include:
Latest rapid response alerts
Findings overviews with distributions
Critical findings and new alerts requiring action
Change tracking, including new assets
New finding categorizations with enhanced risk scoring
Customizable widgets for tailored visualizations and trend tracking
With these enhancements, the dashboard equips you to streamline exposure management with precision, effectiveness, and ease — all in one unified platform built for action.
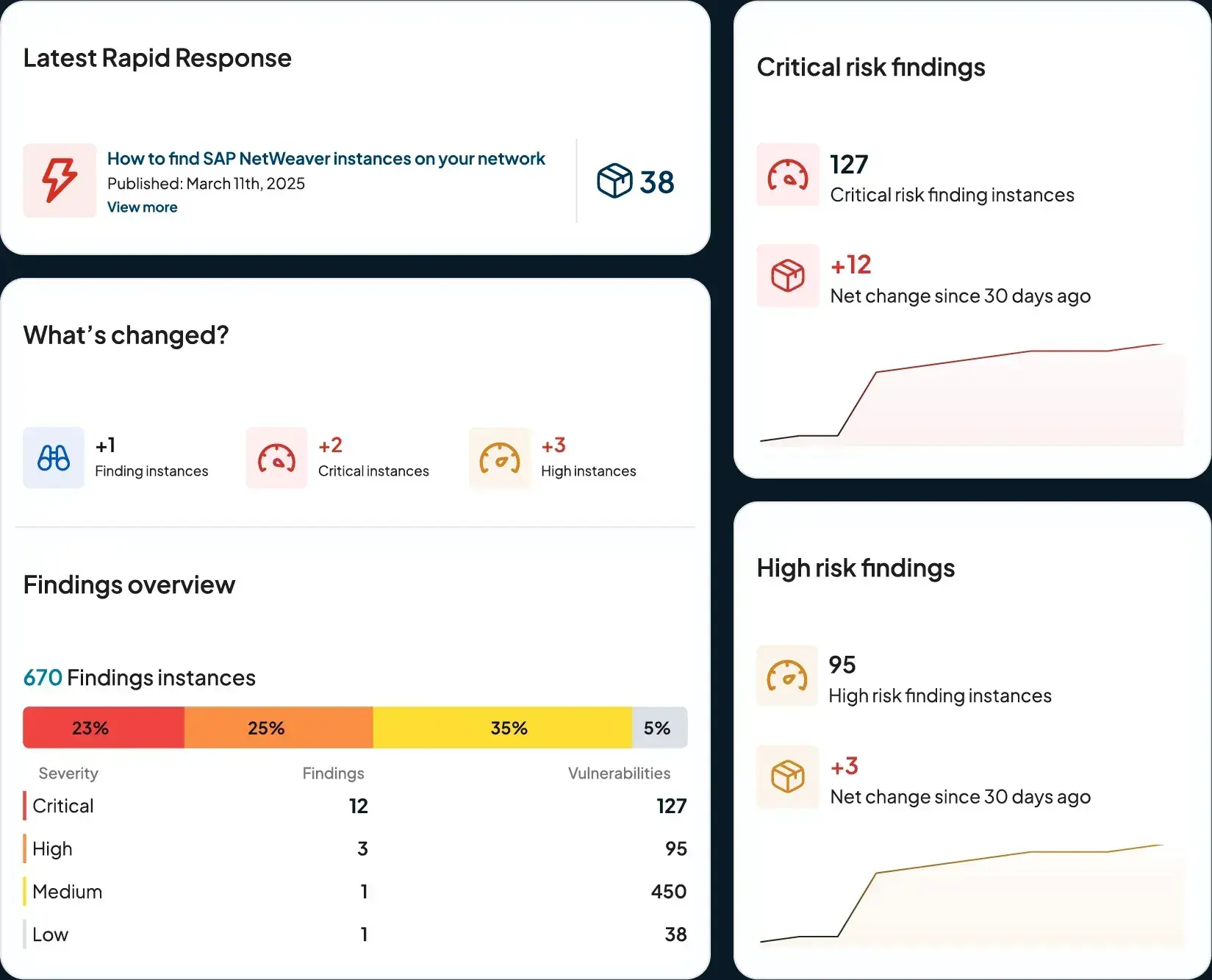
New Risk Findings #
Findings aren’t new to runZero, but how you interact with them is. #
While our powerful search capabilities have always made risk data accessible, the new Findings Section take it to the next level — aggregating all instances affected by exposure categories and surfacing them in one place for fast, informed action.
This release streamlines the entire risk management and remediation lifecycle by organizing exposures by type, mapping them to affected assets and services, applying context-driven criticality, and enabling tracking over time.
We’re launching with eight categories of findings covering 22 unique issues, with rapid expansion planned over the next 12–18 months.
Our mission with Findings is simple: highlight the risks attackers actually target — those with real operational impact — and present them in a way that drives action. As we uncover new exposures, we’ll continue refining the dashboards to ensure every insight is both actionable and impactful.
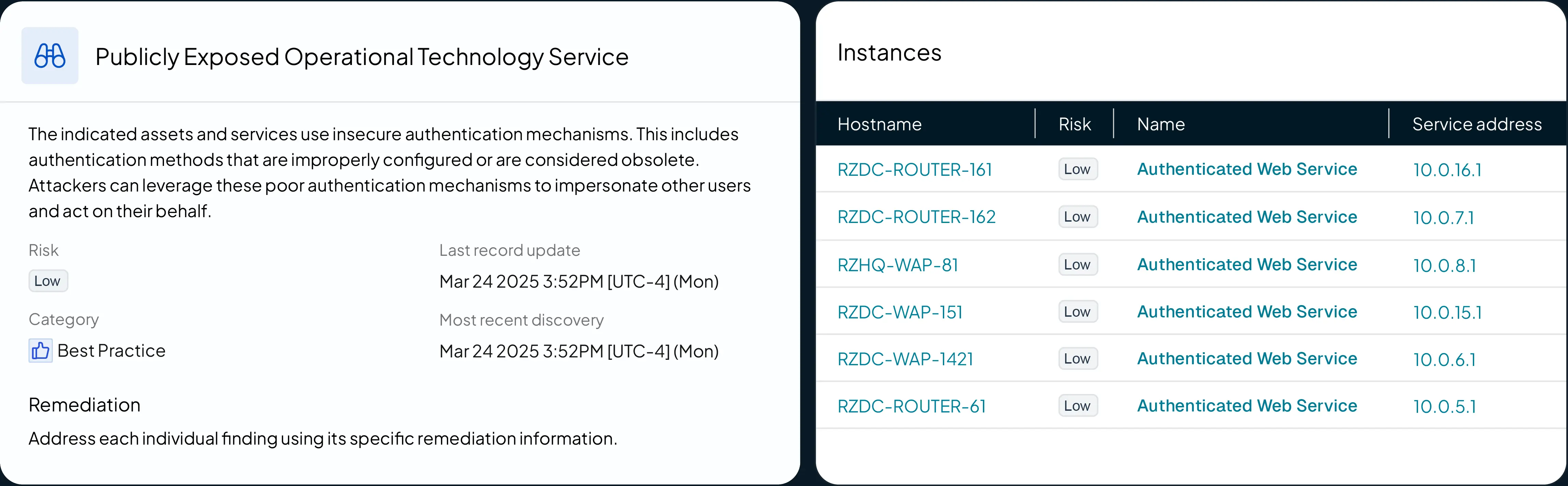
Risk Findings Details #
To delve deeper into risk findings, simply click on a higher-level categorization. For example, in the scenario below, you’ll find a category focused on publicly exposed operational technology (OT). Under "instances," you can easily search for data relevant to assets you want to prioritize or those with specific attributes. Each affected asset is clickable, allowing you to access detailed information about the device, including attributes uncovered through our advanced fingerprinting technology.
Risk Finding Categories #
Internet Exposure #
Identify internal assets that are unintentionally exposed to the public internet with runZero’s Inside-Out Attack Surface Management (IOASM) capabilities. This includes detecting systems that appear externally accessible based on indicators like MAC addresses, SSH banners, and TLS certificates. Sensitive services such as RDP, SSH with password authentication, SMB, VNC, and baseboard management controllers are also flagged.
Our initial release includes four key finding categories:
Potential external access to internal assets
Publicly exposed database servers
Publicly exposed operational technology services
Publicly exposed services
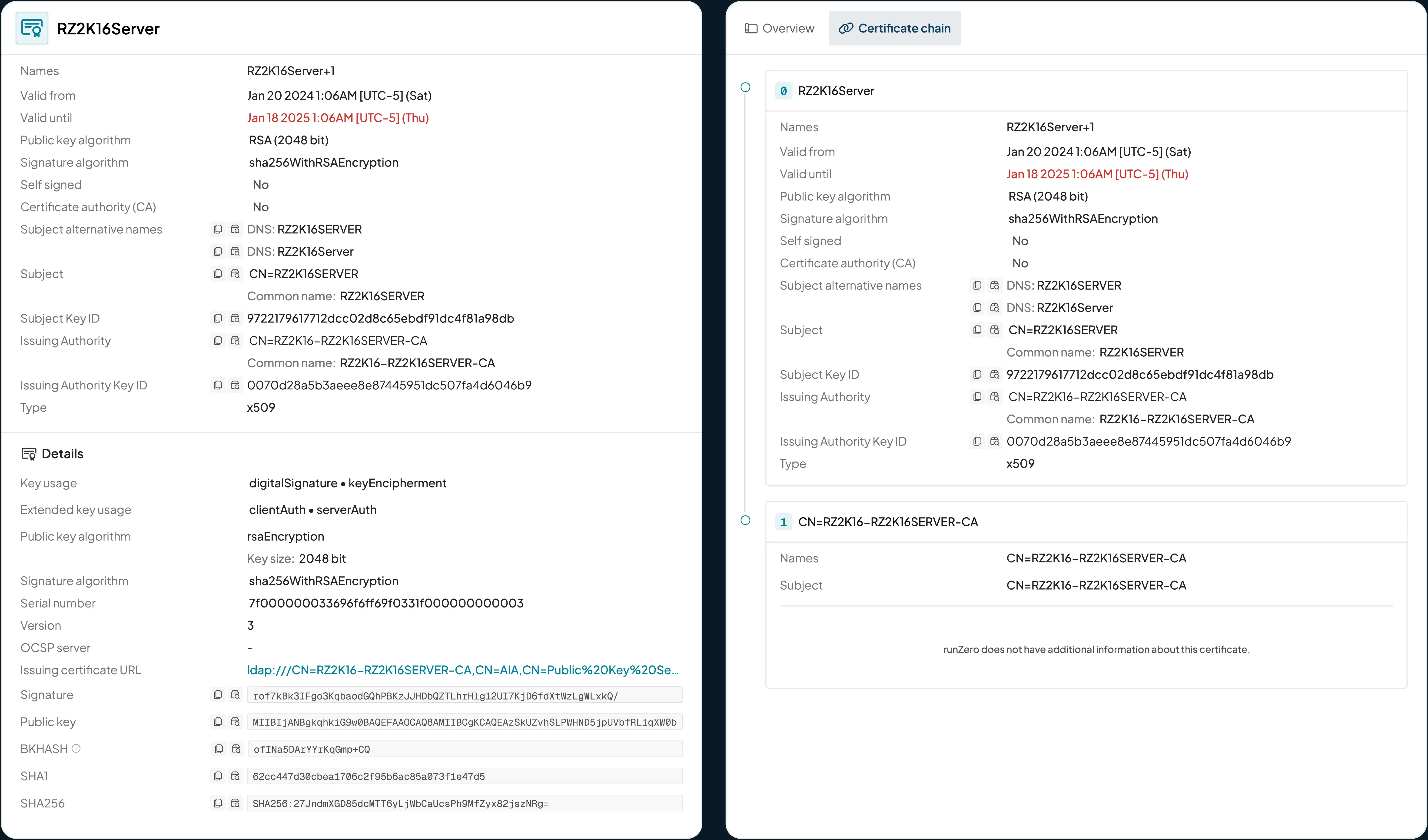
Certificates #
runZero uncovers a wide range of security issues related to TLS certificates and SSH host keys. For example, it detects services with expired TLS certificates that aren’t being automatically rotated, an ongoing challenge for many overburdened operations teams. runZero not only alerts you to upcoming certificate expirations but also maps each certificate to all associated assets and services, making it easier to prioritize and deploy updates.
Our initial release includes two finding categories:
Expired TLS certificates
Widely shared private keys
Vulnerabilities #
Identify assets affected by actively exploited CVEs using curated intelligence from the CISA Known Exploited Vulnerabilities (KEV) and VulnCheck catalogs. runZero helps you quickly pinpoint exposure to high-priority threats such as the HP iLO 4 authentication bypass, Microsoft OMI “OMIGOD” WSMAN exploit, OpenSSH 9.1p1 double-free, and VMware ESXi OpenSLP heap overflow.
Our initial release includes four key finding categories:
Known exploited vulnerabilities
Authentication bypass vulnerabilities
Denial of service vulnerabilities
Remote code execution vulnerabilities
End-of-life #
runZero detects assets running end-of-life (EoL) operating systems, hardware, and applications —critical gaps often missed in vulnerability management programs. With the wide variety of Linux distributions, Windows versions, and niche systems in IT, IoT, and OT environments, tracking EoL status can be a major challenge. runZero helps eliminate that blind spot by surfacing out-of-date assets, even in hard-to-reach corners of your environment. Examples include unsupported operating systems, legacy Accellion File Transfer Appliances, and Cisco Small Business Switches.
Our initial release includes two key finding categorizations:
End-of-life assets
End-of-life operating systems

Open Access #
runZero uncovers network services that expose data or management functionality without requiring authentication, leaving organizations vulnerable to data leakage or unauthorized access. These exposures are often overlooked and can exist across a wide range of systems. Examples include open databases like Redis, MongoDB, and Elasticsearch, as well as services such as Android Debug Bridge, Cisco Smart Install, Distributed Ruby, and Zabbix Agent.
Our initial release includes three key finding categorizations:
Unauthenticated database
Unauthenticated service
File service accessible without authentication
Compliance #
runZero flags assets that may put your organization out of compliance with common regulatory requirements. Whether mandated by government policy or industry standards, identifying prohibited software and hardware is essential for maintaining compliance and avoiding penalties. For example, runZero detects devices and services banned under the 2019 National Defense Authorization Act (NDAA) Section 889, as well as software from Kaspersky Lab, which is restricted for use in the United States and by U.S. persons.
Our initial release includes two key finding categorizations:
Prohibited software
NDAA 2019 Section 889 equipment
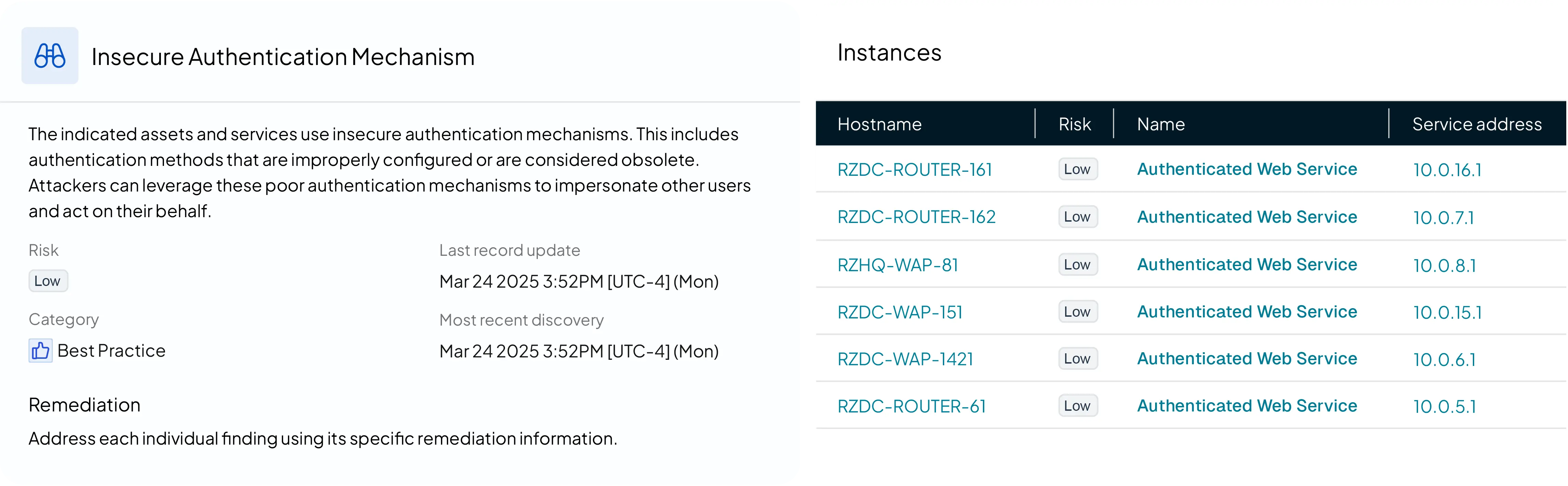
Best Practice Violations #
runZero identifies asset and service configurations that violate security best practices, many of which can lead to elevated risk if left unaddressed. These misconfigurations span a wide range of systems and services, from outdated protocols to weak authentication. Examples include SMBv1 enabled, SSL v2/v3 in use, and SNMP with default communities.
Our initial release includes three key finding categorizations:
Insecure authentication
Obsolete protocol
Service misconfiguration
Rapid Response #
Stay ahead of emerging threats with runZero’s Rapid Response findings. As new zero-days, high-risk misconfigurations, and actively exploited services are discovered, runZero continuously runs curated queries to surface relevant exposures in real time. You’ll get immediate visibility into whether your environment is at risk — no manual searches required or delayed alerts to worry about.
We’re thrilled to share this release with you. These features are all available now in both our licensed runZero Platform and free Community Edition. Give them a try and tell us what you think! We love your feedback.

















