What's new with Rumble 2.6? #
- Synchronize your Azure VM inventory with Rumble
- Identify assets running end-of-life OS versions
- Support for NFS, PPTP, and "r" services
- Updates to the CrowdStrike integration
- Install and update self-hosted Rumble in offline mode
- See new icons throughout the UI
- Fingerprint updates
Sync your Azure virtual machine inventory to Rumble #
Rumble integrates with Microsoft Azure Cloud to deliver greater visibility into your cloud assets. Like our other integrations, you will need to add credentials that will be used to authenticate to Azure Active Directory and set up a connector in Rumble. Rumble will connect to the Azure VM API to collect and add information about the virtual machines to your inventory, including its location, size, OS, storage information, resource group, and more.

Rumble uses a client secret for an app registration to authenticate to Azure Active Directory. To add Azure VM data to Rumble, set up and activate a connection to the Azure VM API. You will need to provide the client ID, client secret, tenant ID, and subscription ID. Make sure to assign the reader role to the application to give it access to your subscription resources.

You can search by Azure VM attributes and leverage them to generate attribute reports for your inventory.

Identify assets running end-of-life OS versions in your inventory #
Running end-of-life (EOL) operating systems can add security, compliance, and business risks to your environment, so it's critical to identify and upgrade these systems as soon as possible. Rumble helps you easily and quickly identify assets that are close to or have reached EOL in your asset inventory.
The asset inventory view has been extended with two new columns, OS EOL and OS EOL EXT, that reflect the support end-of-life and extended support end-of-life date for the detected operating system. Rumble's initial OS EOL coverage includes Windows, macOS, Ubuntu, Debian, and HP iLO firmware.
Rumble color codes the EOL dates based on whether the date is in the past or in the immediate future (90 days). Use the following colors to identify assets that need immediate action:
- Red - The asset is running an OS version whose EOL date has passed.
- Yellow - The asset is running an OS version whose EOL date is within the next 90 days.
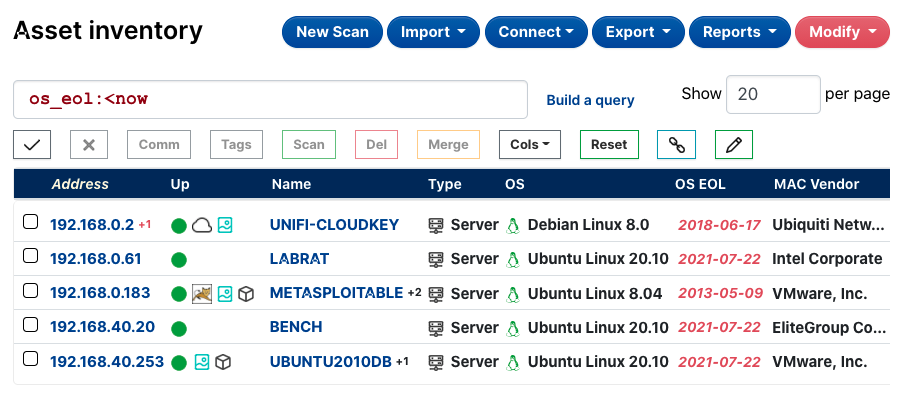
You can filter your asset inventory by EOL date using the keyword, os_eol, with a comparison operator. For example, you can run the following queries:
-
os_eol:<nowshows assets that are beyond their EOL date. -
os_eol:>nowshows assets that are running OS versions still within the official supported period.
Rumble has also added details for assets with EOL extended support. Use the keyword, os_eol_extended, with a comparison operator to filter assets. For example, you can run the following queries:
-
os_eol_extended:<nowshows assets that are beyond their EOL for extended support. -
os_eol:>nowshows assets that are running OS versions still within the official supported period for extended support.
Please note that EOL dates for Windows 10 and Server 2019 builds are not yet available, as Rumble needs more accurate build detection to implement these properly (newer systems often claim to be running older builds via SMB/RDP).
Find open NFS file shares and allowed clients #
Rumble now provides additional information and visibility for assets running mountd, a service that is part of the Network File System (NFS), NFS servers export a list of defined directories along with their access controls, if any. Visibility into systems that have exposed NFS exports can help you proactively assess and determine if there are security risks or misconfigurations.
Rumble captures the following information for NFS exports:
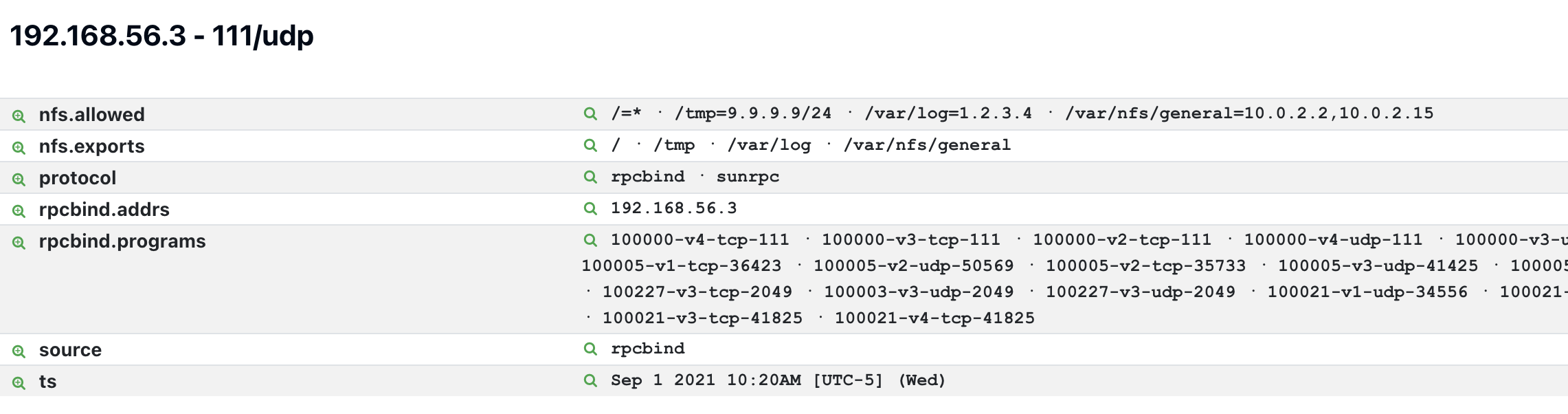
Rumble captures the following information for NFS:
-
All NFS exports - Use the attribute
nfs.exportsto view the filesystem paths available for mounting by other NFS client systems over the network. -
NFS client systems for each NFS export discovered - Use the service attribute
nfs.allowedto view the list of sources allowed to mount to the NFS export. Rumble lists these systems as they are provided by the NFS server, which can include hostnames, IP addresses, CIDR ranges, and netgroups.
Get more service details for PPTP #
The Point-to-Point Tunneling Protocol (PPTP) is one of the oldest network protocols used to create VPNs and tunnel traffic through the internet. Rumble now captures expanded information for assets running VPN software that utilizes PPTP, such as the software version, vendor, and firmware revision. Access to this information lets you search and identify unexpected or unapproved VPN server software running on assets in the network.

Here are all the attributes that Rumble captures for PPTP:
- pptp.bearerCapabilities
- pptp.errorCode
- pptp.framingCapabilities
- pptp.fwRevision
- pptp.maxChannels
- pptp.resultCode
- pptp.vendor
Updates to the CrowdStrike integration #
Rumble 2.5 introduced our integration with CrowdStrike. Our customers quickly adopted the integration and provided us with a ton of great feedback, which will help us continuously improve Rumble's capabilities.
Thanks to that feedback, Rumble 2.6 includes changes to the CrowdStrike integration that will allow us to maintain the most accurate asset inventory possible–especially when we're bringing new data sources into our ecosystem.
Here's what's changed:
- Rumble will import the entire CrowdStrike host inventory each time a CrowdStrike task is run, ensuring that you have full visibility of these assets from your inventory.
- Rumble will update the primary IP address for an asset imported from CrowdStrike only if it's corroborated by a Rumble scan or additional integration source. This will prevent IP addresses from secondary interfaces that are not associated with a specific network or site from displaying in the inventory. The CrowdStrike-reported address will be stored as a secondary address. You'll be able to view it in the asset details and it is searchable from your inventory.
- Rumble will automatically merge CrowdStrike assets with existing assets when they share a hostname or MAC address. Merged assets will show both Rumble and CrowdStrike in the
Sourcescolumn in your inventory. CrowdStrike-sourced assets can still be manually merged with Rumble assets in cases where a hostname or MAC is not available. - Rumble will only show the online or offline status for assets scanned by Rumble. CrowdStrike-sourced assets that have not been scanned will still track the first seen and last seen timestamps and will age out appropriately.
We are excited about these improvements and all of our new integrations. We are committed to providing the most accurate and comprehensive asset inventory possible.
Install and update self-hosted Rumble offline #
Enterprise customers who need to run Rumble in physically isolated environments now have the option to run the self-hosted version of Rumble in offline mode. Running offline mode ensures that Rumble does not make any connections to the internet, which allows teams in air-gapped environments to control their data and update their systems via offline update packages.
Our self-hosted documentation provides step-by-step guidance to deploy our self-hosted version of Rumble and turn on offline mode.
Rumble icon refresh #
Humans can process visuals 60,000x faster than plain text, which is why we've refreshed our product experience with new, custom icons. These visual and design improvements will help you easily navigate the Rumble Console to find tasks and analyze data. Look for our new icons in buttons, tabs, and throughout your inventory.
Which icon is your favorite? Here are ours:
Release notes #
This release includes a rollup of all the 2.5.x updates. Read the changelog to see all the improvements and updates in this release.
Try Rumble #
Don't have access to Rumble yet? Sign up for a free trial to try out these capabilities for 21 days.















