Overcoming 25 Years of Vulnerability Mismanagement #
Common Vulnerabilities and Exposures (CVEs) are the lingua franca of cybersecurity, providing unique identifiers to track the full lifecycle of security issues. From discovery through remediation, CVEs have become synonymous with exposure — but not all vulnerabilities have CVEs. Even when they do, only a very small percentage (0.05% according to the CISA KEV) are actually exploited, and regardless of the source of exploitation data, that observation is always days, weeks, or months behind.
Worse still, the tools we rely on to identify exposures often cover only a small subset of vulnerabilities, with their own significant delays — and even then, only reliably report these vulnerabilities under optimal conditions. Security teams are flooded with thousands of irrelevant alerts while still missing the most serious issues under active exploitation, ranging from default credentials to known-bad misconfigurations, open-access databases, and end-of-life software — all of which fly under the vulnerability management radar.
Traditional tools also fail to discover and defend unknown and unmanageable assets, providing insurmountable gaps from the beginning of the exposure detection and prioritization cycle. Starting with just a fraction of the attack surface makes it impossible to detect the full scope of exposure and prioritize it accordingly. The gaps are especially glaring in OT and IoT environments where agent-based and credential-dependent solutions aren’t feasible, leaving entire classes of assets and exposures invisible to traditional exposure management solutions.
With an incomplete and outdated view of the attack surface, it should come as no surprise that legacy solutions fail from the outset, leaving organizations vulnerable to risks hiding in the gaps, buried under irrelevant alerts, and invisible to traditional asset discovery and exposure detection methods. The resulting blind spots are precisely where the vast majority of attacks occur – in fact, only about 15% of breach events reported in the 2024 Verizon Data Breach Incident Report involved an exploited, CVE-identified vulnerability.
Fixing what’s broken with legacy tools and overcoming persistent, decades-old problems requires a new approach — one that uncovers the exposures you’ve been missing, encompasses your entire attack surface, and focuses relentlessly on surfacing the most exploitable issues. This is the big challenge we’re tackling at runZero. Let’s dive into how we do it and the new features we’re launching today.
runZero: Built for the new era of exposure management #
Our goal is to empower security teams to fully manage the risk lifecycle: finding, prioritizing, and remediating all classes of exposures across internal and external attack surfaces, all in one place. As a single source of truth for exposure management, we believe runZero is the most effective and efficient way for organizations to proactively minimize risk across their entire attack surface. Let’s break down our approach.
Taking control of all assets across the total attack surface #
As mentioned above, traditional tools fail from the start because they assess only a fraction of your actual attack surface. They miss unknown, unmanaged, and unmanageable devices while leaving entire classes of assets like OT, IoT, and mobile devices out of scope. With runZero’s proprietary methodologies, organizations discover every asset across IT, OT, IoT, mobile, and cloud environments safely and comprehensively.
How do we do it?
runZero combines active scanning, passive discovery, and API integrations to discover both internal and external attack surfaces, including elusive unknowns and unmanageable devices. If an asset is connected to your network, our Explorers will find it.
Our active scanning is proven safe for even the most fragile OT and IoT environments. We never send malformed packets and use incremental probing and detailed throttling to ensure safe and controlled scanning while gathering actionable information.
Our advanced fingerprinting delivers unmatched depth to identify critical insights into services, ownership, hygiene, and more (even screenshots!) — building detailed, accurate profiles of each asset, leveraging a library of almost 1,000 attributes.
We don’t rely on agents or authentication, providing comprehensive coverage and visibility with results in literally minutes.
The end result is total attack surface visibility — ensuring you see every asset on your network, no matter how hidden or unconventional. On average, runZero enterprise customers report finding 25% more assets than they were previously aware of, with some environments yielding 10x more assets than security teams expected, radically expanding their view of their attack surfaces and the exposures within. And this visibility also enables runZero to find risks well beyond CVEs and the reach of traditional tools.
Uncovering all types of exposures, including the hidden ones #
Attackers don’t limit themselves to CVEs, and neither should your defenses. Our CAASM roots and industry-leading fingerprinting data give us an unfair advantage in being able to identify much broader classes of exposures, including those that evade traditional vulnerability and external attack surface management solutions.
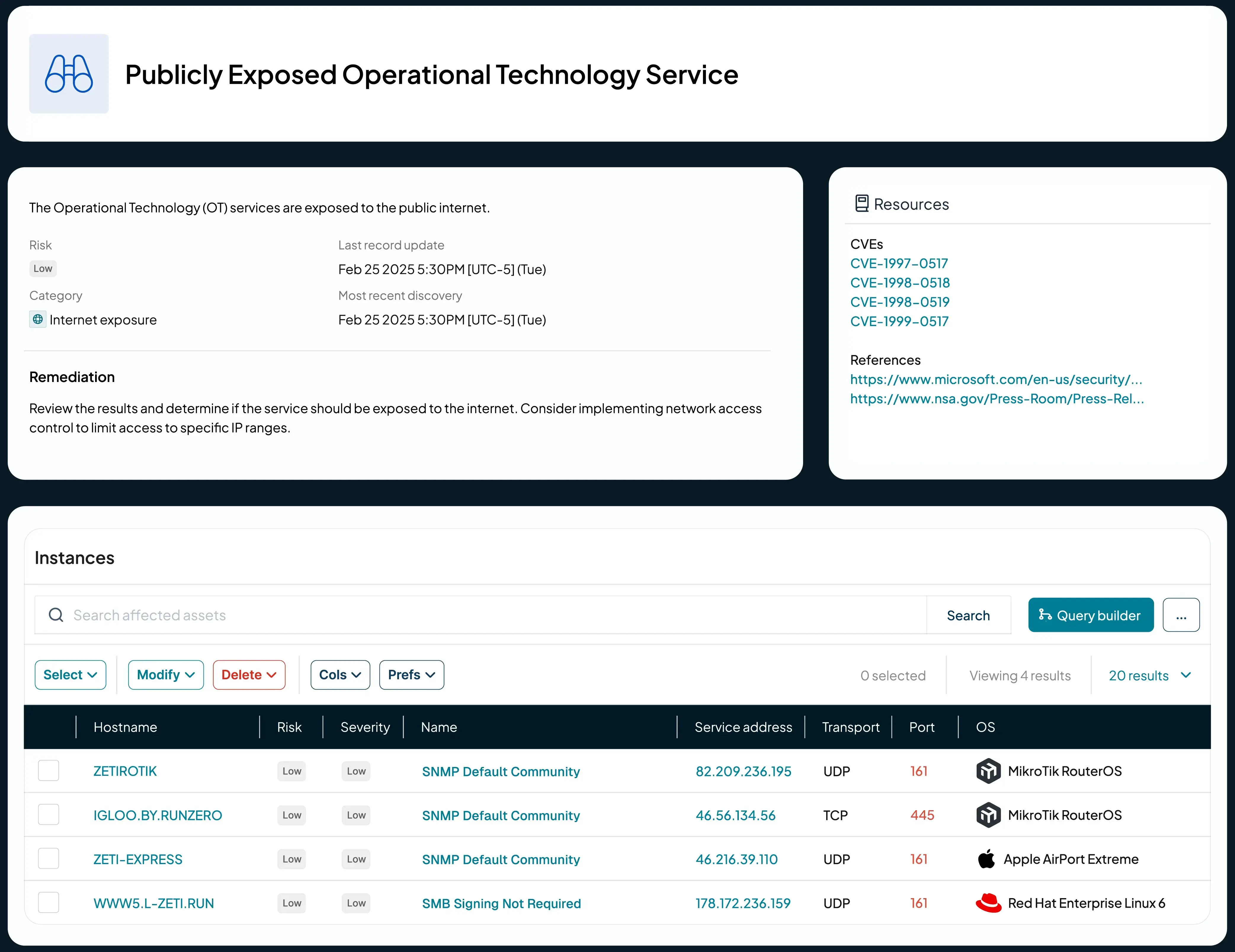
Through context-rich data and detailed insights into device connections, configurations, and services, runZero reveals exposures that might otherwise remain hidden, including issues like network segmentation failures, externally-exposed internal assets, missing security controls, shared keys, end-of-life software, prohibited devices, and misconfigured OT and IoT devices.
runZero also enables you to quickly respond to zero days without rescanning. Leveraging data already captured in the fingerprinting process, embedded Rapid Responses enable you to immediately surface at-risk assets, including unmanaged devices.
With runZero, you can zero in on the critical exposures that attackers love to exploit.
Bringing the real threats into focus #
Alert fatigue is a real thing, and today’s tools are responsible. Security teams are overwhelmed by irrelevant alerts, buried in noise that obscures true risks and delays remediation. Entire classes of tools have emerged simply to help teams prioritize the flood of alerts. And every delay gives attackers more opportunity for exploitation.
Our goal is to offer richer, more meaningful asset and exposure data that effectively prioritizes the risks that truly put your organization in danger. runZero performs this prioritization against a full-spectrum of exposure detection that includes your entire attack surface, not just a siloed swath.
runZero employs data-driven risk prioritization, highlighting the most urgent exposures by leveraging business context, device impact, and meaningful attributes. With highly intuitive risk findings, security teams can focus on critical threats while understanding their broader implications across the attack surface.
Armed with contextual data from runZero, security teams can accelerate remediation workflows and shrink exploitation windows, acting quickly and strategically while gaining operational efficiency.
Meet runZero Risk Findings: A new way to detect exposures and track risk
runZero’s new Risk Findings (and beautiful new dashboards) change the game by introducing a new paradigm for organizing and addressing exposures. They provide the focus and comprehensive coverage where traditional tools falter.
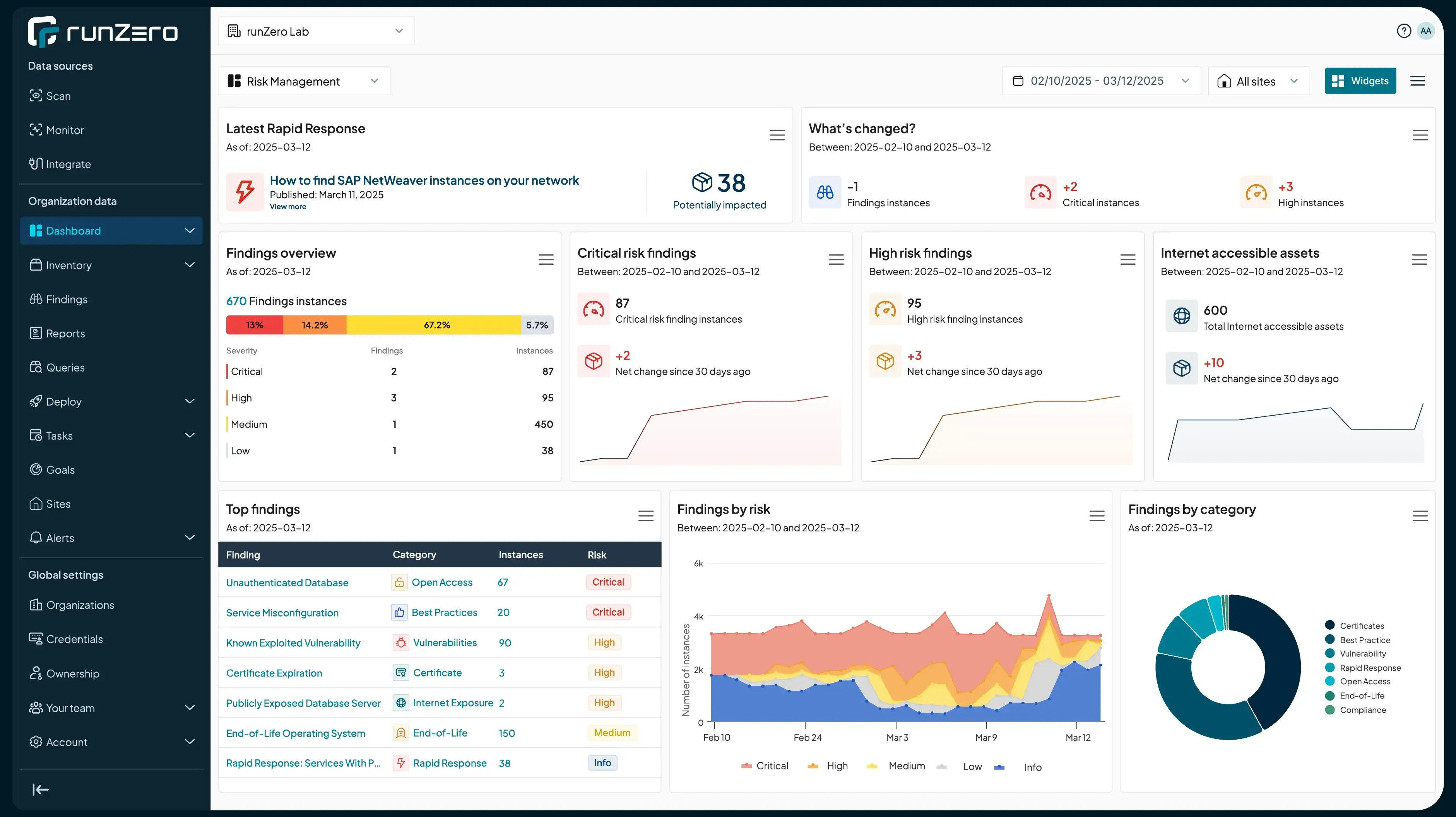
runZero Risk Findings identify classes of risk across your attack surfaces, aggregating all associated inventory assets, services, or other entities under each risk category. For example, a finding like “End-of-Life: Operating System” would automatically link all assets running unsupported operating systems, giving teams an actionable and organized way to target their remediation efforts.
But the enhancements go further. Findings don’t just present a current view of risk—they also provide a way to track trends over time. In this initial release, teams can monitor aggregate counts of associated findings historically. Over time, we plan to expand this capability, providing detailed snapshots of findings during critical status transitions that enable teams to track progress more effectively and stay ahead of evolving risks.
Today’s release includes a diverse range of findings to address the most critical risk areas and elusive exposures, including:
Internet Exposures: Identifies internal assets unintentionally exposed to the internet, such as Remote Desktop services or sensitive OT devices.
End-of-Life Systems: Pinpoints all assets running unsupported hardware or software, like aging Cisco Small Business Switches or obsolete Windows versions.
Open Access Services: Detects misconfigurations like unauthenticated databases (e.g., MongoDB, Redis) or exposed management interfaces.
Known Exploited Vulnerabilities: Highlights assets targeted by active threats, leveraging insights from CISA KEV and VulnCheck KEV catalogs.
Compliance Challenges: Flags instances of prohibited equipment or configuration issues that violate specific acquisition regulations, such as NDAA Section 889 violations.
Certificates: Identifies a wide range of security issues with TLS certificates and SSH host keys, including expired (and nearly expired) certificates, as well as widely shared private keys.
Best Practices: Highlights asset and service configurations that violate security best practices such as SMBv1 enabled, SSL v2/v3 in use, and SNMP with default communities.
Vulnerabilities: Identifies multiple issues based on both natively discovered and externally imported vulnerabilities.
Rapid Responses: Automatically runs queries for emerging threats, and tracks the results in the Rapid Response findings category.
Our aim is to uncover the kinds of risks attackers routinely exploit that other solutions often miss. Leveraging the depth of runZero’s discovery and fingerprinting data in novel ways offers unprecedented clarity into the exposures that truly matter most, eliminating irrelevant noise and blind spots.
What’s next? #
This is just the beginning. runZero’s Risk Findings and exposure management capabilities are evolving on a daily basis, delivering powerful insights to help organizations stay ahead of exploitable threats. With every enhancement, our goal is to provide you with the tools you need to protect your total attack surface and take action where it matters most.
Learn more #
Not yet a runZero user? Try it free →
Tune in to April’s runZero Hour for a deep dive on all the new platform capabilities. Register →
Now on demand: Omdia analyst webcast "Vulnerability management is broken: what's the fix?" Watch now →
















