As of release 1.15.3, Rumble Network Discovery now detects the TeamViewer protocol on your network in addition to the existing coverage for RDP, VNC, SPICE, and PC Anywhere. This rounds off Rumble's broad support for monitoring remote access solutions.
AD-Controlled RDP is Great, but Unmanaged RDP is a Risk Factor #
Remote Desktop Protocol (RDP) is a useful tool when enabled on a machine that's properly managed on the domain (that is if you're properly managing local accounts). However, RDP can also put you at risk if active on a machine that's not in your domain. It's typically tough to find those, but with Rumble you can.
In your Rumble Console, go to Explore, then scroll down to the Domain Membership Report and select Report Only RDP:
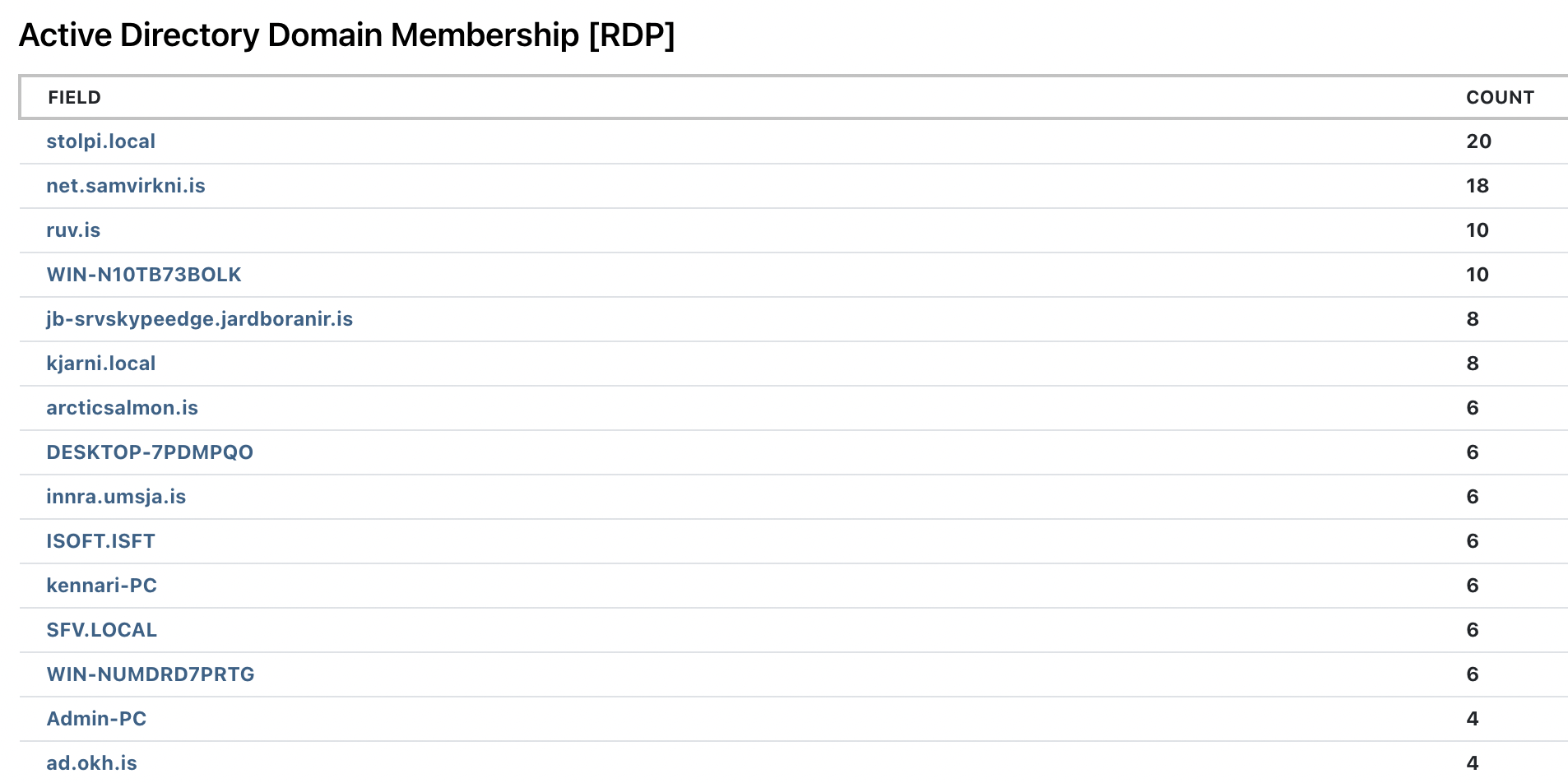
What you should be seeing is a lot of machines that are on your domain and then a long tail of machines that are not part of your domain:
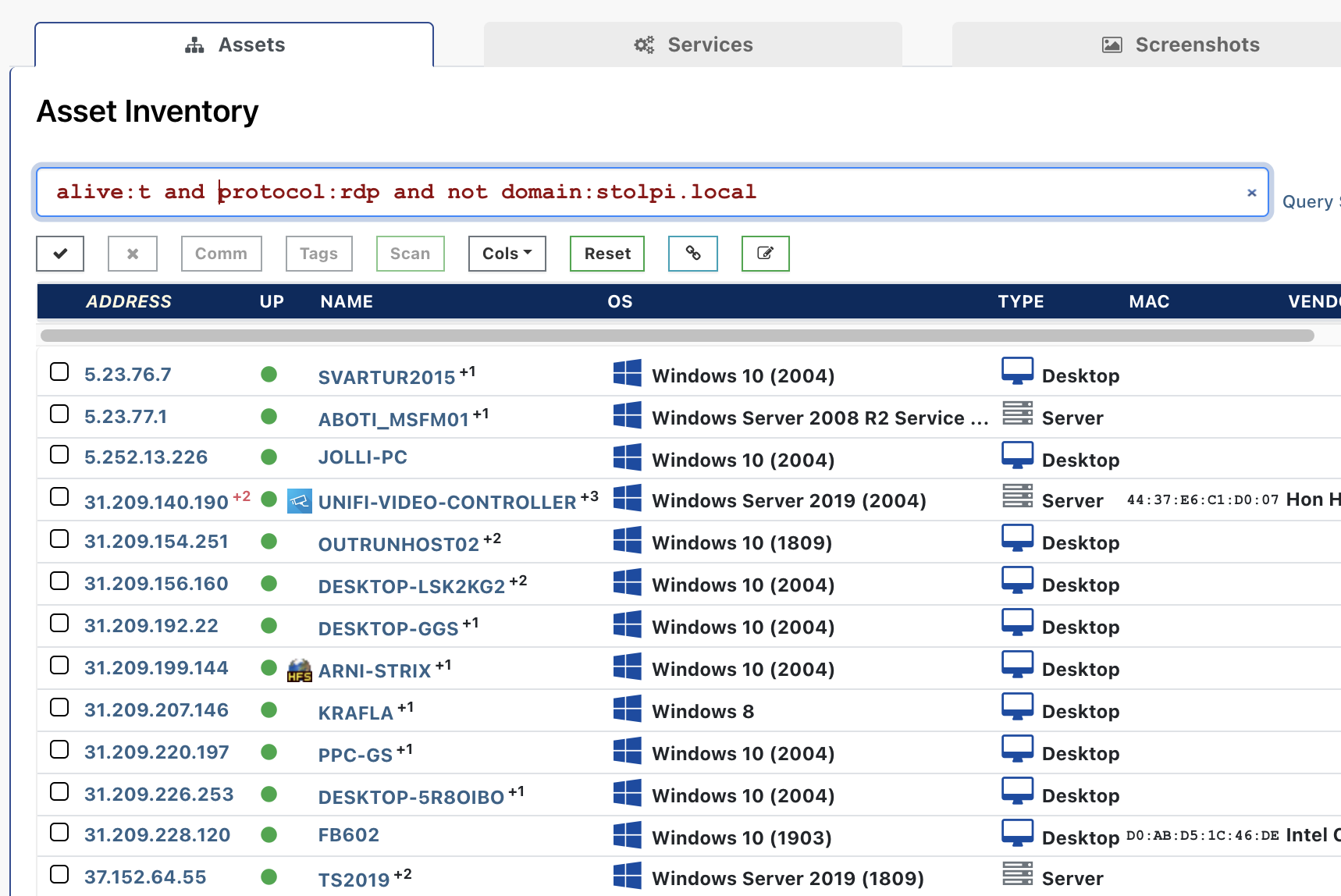
Let's assume that your local domain is "stolpi.local", you can set up a query for all devices that run RDP but are not on your domain as follows:
alive:t and protocol:rdp and not domain:stolpi.local
How to Find Other Rogue Remote Access Solutions on Your Network #
While remote access solutions are not bad per se, you'll want to keep a close eye on the network to ensure that you don't have any rogue remote access solutions running. Let's say your corporate standard is VNC, you'll probably want to find and alert on any RDP and TeamViewer protocols showing up on your network, and getting alerts on new VNC hosts on your network.
Here's how you use Rumble to find remote protocols being used on your network, even if they are running on non-standard ports:
In your Rumble Console, click on Inventory in the left navigation and use the following search queries to find these remote desktop solutions:
- Microsoft Remote Desktop Protocol:
protocol:rdp - VNC Viewer:
protocol:vnc - TeamViewer:
protocol:teamviewer - SPICE:
protocol:spice - PC Anywhere:
protocol:pca
To find all of these at the same time in Rumble, you can use this query:
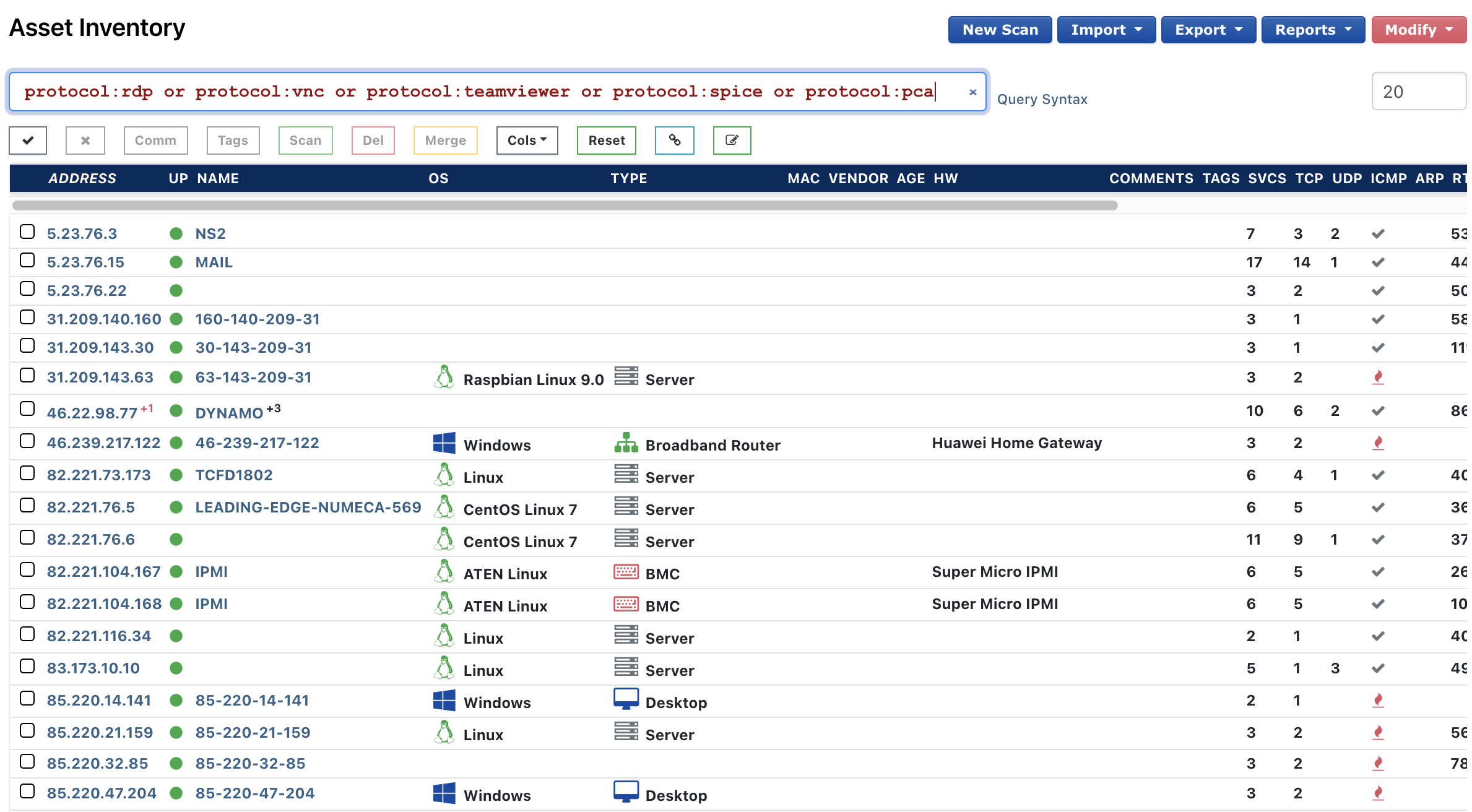
protocol:rdp or protocol:vnc or protocol:teamviewer or protocol:spice or protocol:pca
You should be seeing something like this:
Clicking on a random host in this list and scrolling down to the Protocol section, we see that VNC is active on this machine:
Try Finding Remote Access Solutions on Your Network with Rumble #
If you haven't had a chance to try runZero, or would like to find remote access solutions on your internal network, sign up for a free trial and let us know what you think!
















