Latest lighttpd vulnerability #
On April 11th, 2024 Binarly published research showing that Baseboard Management Controllers (BMC) derived from the AMI MegaRAC product include older versions of the open source lighttpd web server. Specifically, their research noted that lighttpd versions prior to 1.4.51 are susceptible to an information leak due to a string comparison against a stale pointer. This issue affects AMI MegaRAC BMCs, but also BMCs produced by Intel and Lenovo. This vulnerability was patched in version 1.4.51 and no CVE was assigned. Binarly calculated the CVSS v3.1 score as 5.3 Medium AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N.
runZero provided guidance on detection and mitigation of these issues on the same day, but also started a deeper investigation into the real-world impact of this issue, resulting in the following notes:
- Hundreds of devices from dozens of manufacturers appear to ship the same vulnerable versions of lighttpd. We've included examples of these at the end of this post.
- The lighttpd project did not assign a CVE to this issue, but they did flag it as a security fix in their change log.
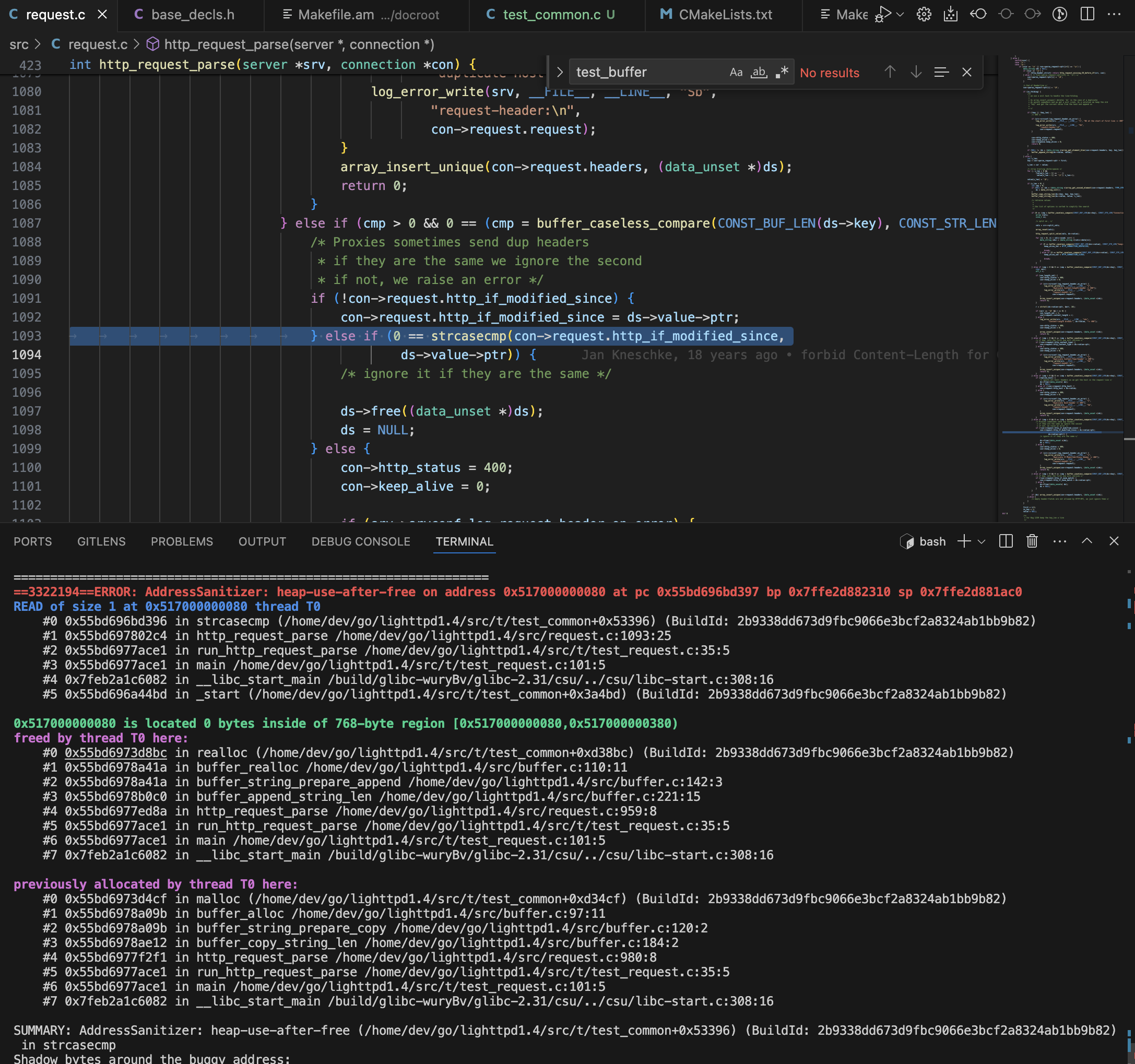
- The folded header issue highlighted by Binarly may be tricky to exploit. The bug allows for a remote attacker to confirm whether a string referred to by previously-used pointer is equal to a separate string provided by the attacker. In effect, the attacker can only confirm something they can guess, and at worse can use this to do a case-insensitive compare against the reused pointer. An attacker could brute force string values and hope to confirm an address or value in memory, but practically this doesn't seem feasible, as the case-insensitive comparison and the character restrictions (especially in strict header mode) will result in false positive matches and unguessable values.
- The lighttpd project is part of Google's OSS-Fuzz scope, but the test cases only cover the "burl" implementation and not the HTTP request parser.
- runZero was able to reproduce this issue using the AFL++ fuzzing engine, but did not identify any additional issues during an overnight fuzzing run.
- In addition to the information leak with folded headers, lighttpd noted additional security issues in the same range of versions:
- 1.4.51 - 2018-10-14 * [core,security] process headers after combining folded headers * [mod_userdir] security: skip username "." and ".." - 1.4.50 - 2018-08-13 * [mod_alias] security: potential path traversal with specific configs * [core] security: use-after-free invalid Range req * [mod_alias] security: path traversal in mod_alias (in some use cases) (fixes #2898) * [core] security: use-after-free after invalid Range request (fixes #2899)
What is the impact? #
In the case of the folded header issue, AMI MegaRAC BMCs on servers running lighttpd before version 1.4.51 are susceptible to a limited information leak. This leak does not provide the contents of the stale pointer, but it does allow the attacker to confirm if the reused pointer has a specific string value. As a result, it doesn't appear to be significant, as the attacker can only confirm a value that they are already aware of.
The additional security issues outlined in the lighttpd changelog may be more serious. The mod_userdir issue can allow a directory traversal attack when the URL `/~../` is requested, but this module may not be commonly enabled. The mod_alias issue seems similar in that it could allow traversal from the web root, but is unlikely to apply to most installations as it requires a missing trailing slash in the alias configuration.
This brings us to the use-after-free fixes for invalid Range requests. It's not clear yet how significant these are yet, but we plan to continue this investigation given how many devices are impacted.
Are updates or workarounds available? #
Although AMI has released updated firmware, Intel and Lenovo have both indicated that their affected products are end-of-life (EOL) and will not receive updates. runZero recommends using network segmentation to prevent access to these outdated lighttpd services from untrusted networks. For BMCs specifically, best practices include isolating these interfaces to a dedicated management network, and leveraging VPNs to provide remote access as needed.
How do I find potentially vulnerable systems with runZero? #
From the Services Inventory, use the following query to locate systems running potentially vulnerable software:
product:lighttpd (_service.product:=lighttpd:lighttpd:1.4.0% OR _service.product:=lighttpd:lighttpd:1.4.1% OR _service.product:=lighttpd:lighttpd:1.4.2% OR _service.product:=lighttpd:lighttpd:1.4.3% OR _service.product:=lighttpd:lighttpd:1.4.4% OR _service.product:=lighttpd:1.4.50)Known devices with outdated lighttpd installations #
In addition to the AMI MegaRAC BMCs, runZero has observed outdated installations of lighttpd on the following devices:
- AAM-Router
- AE-200/AE-50/EW-50
- AMAG M4000 Physical Access Control System
- AMI MegaRAC
- ARRIS Device Management
- ARRIS Media Server
- ASUSTeK Asuswrt
- AWiND WePresent WiCS-2100
- Aiphone Intercom
- Alcatel-Lucent Enterprise OmniView Switch
- Aruba Switch
- Askey Computer Corp. Rt4230w-D187 Router
- Asus RT-AX88U
- Asus WAP
- Avaya CU360
- Axis Camera
- BASRouterLX
- BASgatewayLX
- BCM96750
- Barco ClickShare
- Belkin AC1900 WIRELESS RANGE EXTENDER
- Belkin Dual Band Wireless Range Extender
- Broadcom Corporation X1
- Buffalo NAS
- CBC Co.,Ltd. Network Camera
- Calient Photonic Switch
- Cambium Networks WLAN AP
- Canon ScanFront
- Chromebook
- Cisco Catalyst 2960S-48LPS-L
- Cisco IP Camera
- Cisco Meraki MR18
- Cisco Meraki MR32
- Cisco Meraki MR34
- Cisco Meraki MR72
- Cisco Router
- Cisco SX20
- Cisco TelePresence TANDBERG/257
- Cisco TelePresence TANDBERG/516
- Cisco TelePresence TANDBERG/518
- Cisco UCS Manager
- Cisco Video Surveillance 5010
- Cisco Video Surveillance 5011
- Cisco VoIP
- Cisco Wireless Access Point
- Cisco Wireless LAN Controller
- Contemporary Control Systems BASRTLX-B
- Crestron AM-100
- Crestron AirMedia
- DWC-MPTZ30X
- DWC-MPTZ336XW
- Dahua IPC-HDW4433C-A
- Dell iDRAC
- Digital Devices GmbH OctopusNet
- EDIMAX IC-7113W Network Camera
- Eaton Corporation Power Xpert 2000 Series Meter
- Eaton Power Xpert
- ecobee4
- EnGenius Technologies EAP1300
- EnGenius Technologies ENH500
- EnGenius Technologies ENH500v3
- EnGenius Technologies EWS300AP
- EnGenius Technologies EWS310AP
- EnGenius Technologies EWS360AP
- EnGenius Technologies WAP
- EtherWAN Switch
- Extron DTP System Display Controller
- Extron Scaling Presentation Switcher Display Controller
- FLIR IP Camera
- Fortinet FON-480
- Fortinet FON-580
- Foscam IP Camera
- GOLD Ver. E
- GW-5492
- Google Chromecast
- Grandstream GXP2130
- Grandstream GXP2135
- Grandstream GXP2160
- Grandstream GXP2170
- Grandstream UCM6202 1.7A
- Grandstream VoIP 1.10
- Green Electronics RainMachine
- HARMON International AMX N-Series Decoder
- HARMON International AMX N-Series Encoder
- HP 280 G3 SFF Business PC
- HP LaserJet 400 Color M451dn
- HPE OfficeConnect 1920S-48G
- HPE StoreEver MSL3040
- Haivision Makito X Decoder
- Hanwha Techwin IP Camera
- Honeywell H3W1F
- Honeywell Industrial Printer PD43
- Honeywell Intermec PC23d
- Honeywell Intermec PC42d
- Honeywell Intermec PC43d
- Honeywell Intermec PC43t
- Honeywell Intermec PM42
- Honeywell Intermec PM43
- Honeywell Intermec PM43c
- HoneywellACS 0.01
- I3 International IP Camera
- IBM FlashSystem 900
- IBM IMM2
- Intermec PC23d
- Intermec PC43d
- Intermec PC43t
- Intermec PD43
- Intermec PM42
- Intermec PM43
- Intermec PM43c
- HP J9147A
- LIP-ME204C
- LOYTEC Electronics GmbH BACnet
- LVIS-3ME7-G2
- Lantronix X5
- Lifesize TelePresence
- Linear EMerge
- Linksys MR5500
- Linksys Velop
- Linksys WAP300N
- Linksys, LLC Simultaneous Dual-Band Wireless-AC Gigabit Router
- MiOS, Ltd. MiOS Z-Wave Home Gateway
- MikroTik RB750r2
- Motorola AP650
- Motorola AP7522
- Motorola AP7532
- Moxa Terminal Server
- NAS4Free
- NEC 800
- NEC Smart TV
- NETGEAR EX6250
- NETGEAR Switch
- Nuuo DVR
- Omron Corporation NJ101 2.5
- Omron Corporation NJ301-1100 2.2
- Omron Corporation NJ501-1300 2.3
- Omron Corporation NJ501-1400 2.4
- Omron Corporation NJ501-1500 2.4
- Omron Corporation NX102-1000 2.6
- Omron Corporation NX102-1020 2.6
- Omron Corporation NX102-1220 2.6
- Omron Corporation NX102-9020 2.6
- Omron Corporation NX701 2.5
- Panasonic WJ-NX400
- Pelco IDS0DN
- Pelco IME219
- Pelco IME319
- Pelco IMS0DN10-1V
- Pelco IP Camera - Endura Enabled
- Pelco IX30DN
- Pelco IXE31
- Pelco MCE H264 - Endura Enabled
- Pelco Sarix D5118
- Pelco Sarix Pro Camera
- Pelco TXB-N
- Quanta Network Appliance
- Quantum Scalar I40
- Quantum Scalar I80
- Rittal PDU (7955.211)
- Roku 3
- SATO CL4NX
- SATO Printer
- SONY UBP-X700
- Samsung DVR
- Samsung IPolis IP Camera
- Samsung SND-6084R Network Camera
- Samsung SNV-6013 Network Camera
- Samsung SmartCam
- Sato CL4NX
- Schneider Electric Network Management Card 2 08
- Schneider Electric Trio QB450
- Schneider Electric Trio QR450
- ScreenBeam Conference
- Seagate BlackArmor NAS 4D
- Seagate Central NAS 1D
- Sierra Wireless AirLink
- Sonos ZonePlayer S3
- Sony BDP-2017
- Sony STR-2017
- Sony STR-DN1080
- Sony Smart TV
- Sony UBP-X700
- Sony XR-77A80K
- Spectra Logic Stack
- Super Micro IPMI
- Synology NAS
- TP-Link NC260
- TempAlert Router
- Toshiba Canvio Home
- Tyco IPS02D2ICWIT
- Tyco IPS02D2ICWTT
- Tyco IPS02D2OCWIT
- Tyco IPS02D2OCWTT
- Tyco IPS05D2ICWIY
- Tyco Illustra
- UPS Manufacturing NetMan Plus
- Ubiquiti AirCam
- Ubiquiti AirFiber 24G
- Ubiquiti AirFiber 24G HD
- Ubiquiti AirFiber 5
- Ubiquiti AirFiber 5X
- Ubiquiti AirFiber 5XHD
- Ubiquiti AirGrid M5 HP
- Ubiquiti AirMax
- Ubiquiti Bullet AC
- Ubiquiti Bullet M2
- Ubiquiti Camera G3
- Ubiquiti Camera G4 Pro
- Ubiquiti EdgePower-54V-150W
- Ubiquiti EdgeSwitch 5XP
- Ubiquiti ISO Station 5AC
- Ubiquiti ISO Station M5
- Ubiquiti LM5 NanoStation Loco M5
- Ubiquiti LTU-LR
- Ubiquiti LTU-Rocket
- Ubiquiti LiteAP AC
- Ubiquiti LiteBeam 5AC 23
- Ubiquiti LiteBeam 5AC Gen2
- Ubiquiti MFi MOutlet
- Ubiquiti MFi MPower Pro
- Ubiquiti N2B-400
- Ubiquiti NanoBeam 5AC 16
- Ubiquiti NanoBeam 5AC 19
- Ubiquiti NanoBeam 5AC Gen2
- Ubiquiti NanoBeam M2 13
- Ubiquiti NanoBeam M5 16
- Ubiquiti NanoBeam M5 400
- Ubiquiti NanoBridge M5
- Ubiquiti NanoStation 5AC
- Ubiquiti NanoStation 5AC Loco
- Ubiquiti NanoStation Loco M2
- Ubiquiti NanoStation Loco M5
- Ubiquiti NanoStation Loco M900
- Ubiquiti NanoStation M2
- Ubiquiti NanoStation M3
- Ubiquiti NanoStation M365
- Ubiquiti NanoStation M5
- Ubiquiti NanoStation M5 NanoStation Loco M5
- Ubiquiti PicoStation M2
- Ubiquiti PicoStation M2 UVC G3 Flex
- Ubiquiti PowerBeam 5AC 300
- Ubiquiti PowerBeam 5AC 400
- Ubiquiti PowerBeam 5AC 500
- Ubiquiti PowerBeam 5AC Gen2
- Ubiquiti PowerBeam 5AC ISO Gen2
- Ubiquiti PowerBeam M5 400
- Ubiquiti PowerBridge M5
- Ubiquiti PrismStation 5AC
- Ubiquiti Rocket 5AC Lite
- Ubiquiti Rocket 5AC PTMP
- Ubiquiti Rocket 5AC Prism
- Ubiquiti Rocket M2
- Ubiquiti Rocket M3
- Ubiquiti Rocket M365
- Ubiquiti Rocket M5
- Ubiquiti Rocket M5 GPS
- Ubiquiti Rocket M5 Titanium GPS
- Ubiquiti Rocket M900
- Ubiquiti Rocket Prism 5AC Gen2
- Ubiquiti TOUGHSwitch PoE
- Ubiquiti TOUGHSwitch PoE PRO
- Ubiquiti UniFi Router
- VIAVI ONT-600
- VIAVI ONT-601
- VIAVI ONT-602
- VICON SN663V-A-H.264 Network PTZ Camera
- VICON SN673V-B-H.264 Network PTZ Camera
- VMware Site Recovery Manager
- Verifone Payment Devices
- Video Storm LLC Gmediarender 0.0.7
- Vizio E65-E0
- Vizio E70u-D3
- Vizio Smart TV
- Vizio SmartCast Sound Bar
- Wansview NCM-631GA
- WonderMedia Technologies, Inc. 1.0
- ZebraNet Barcode Scanner

















