Unmanaged assets are connected to the network, but lack an identified owner and may exist outside the visibility of those responsible for the network. These devices can pose real security risks to a company or organization for numerous reasons, such as running older vulnerable operating systems or software, using insecure protocols, or having nefarious intent. Plus, they can be difficult to discover or locate, sometimes using unmanaged subnets within a network.
Unmanaged devices challenge both IT and security programs #
Arising from both intentional and inadvertent situations, unmanaged assets can be classified into several categories, including:
- Orphaned assets that lost their original owner but are still present on the network. These devices were once managed but have fallen off the radar, for example an open-source web app run by a department that has since been superseded by a SaaS application but is now continuing its zombie life without patching or oversight.
- Shadow IT devices/systems that are connected to the network without permission. Imagine a developer’s test box set up with permission of the engineering team but without central governance: The machine is not on the Active Directory, not getting group policies, maintenance updates, or security controls. Because it doesn’t allow access via domain admin passwords, it’s off the radar for most CMDBs
- Transient devices, such as portable, mobile, or IoT devices that “come and go” on the internal network, including bring your own device (BYOD), might be better categorized as “unmanageable” rather than “unmanaged” and can also be easily discovered via runZero scanning.
Let's take a look at how runZero is able to locate unmanaged devices on your networks.
A peek under the hood of our scan engine #
At runZero, we intentionally built our offering around unauthenticated, active scanning, while complementing our technology through integrations with cloud, virtualization, and security infrastructure to provide full visibility into IT, OT, cloud, and remote devices. To start, let's dig into our scanning capabilities. Our built-from-the-ground-up scanning logic in runZero Explorers and scanners will reach out to elicit a response from devices connected to the network. Replies received from our scan traffic are then captured for processing.
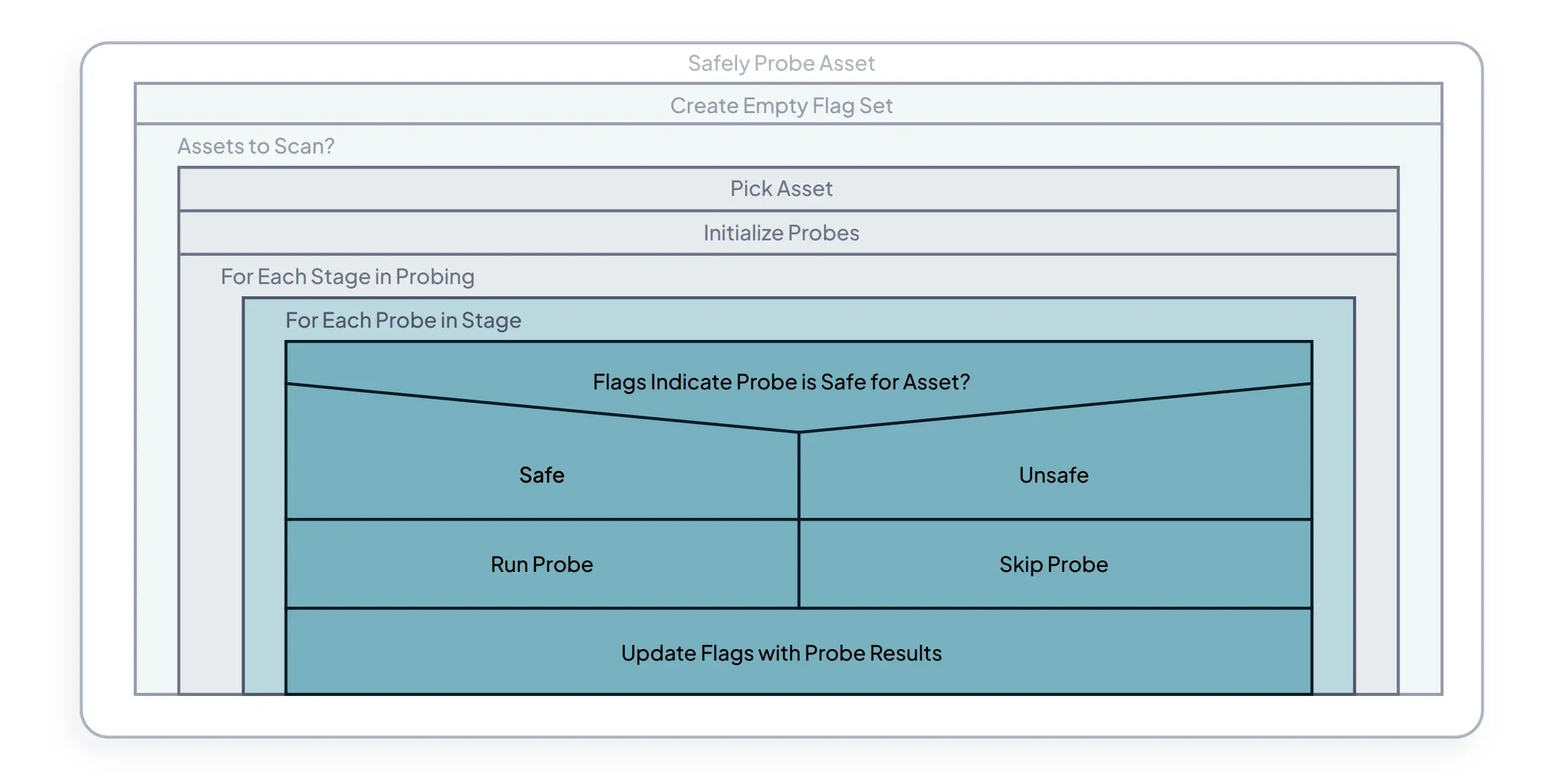
Benefits to our approach #
No prior knowledge required: Our active, unauthenticated scanning approach doesn’t assume any “prior knowledge” of network-connected devices (e.g., credentials to authenticate into devices, deployed agents on managed devices, etc.), rather our network discovery capabilities are research-driven to find-and-surface every network-connected asset, whether managed or unmanaged.
Highly configurable: Our scans allow you to go beyond basic subnet and speed settings. You can tune scans for specific ports or protocols that you want to know about, which can help quickly locate unmanaged devices that are running unsafe or company-prohibited protocols.
Standard packets: All of our scanning packets, including probes and port/service querying, is done using standard packets to keep things safe. We never send malformed or otherwise unusual packets.
Research driven: We use applied research to maximize scan result discoveries while still utilizing a “safe approach” for interacting with devices. This helps avoid any unexpected or unwanted side effects that are sometimes seen with other active scanning solutions, particularly when scanning ICS/OT and other traditionally sensitive devices/endpoints.
Building a comprehensive internal asset inventory #
A comprehensive asset inventory is not complete unless you know about the assets that aren't managed by your organization. Here are some ways that runZero can help you zero in on assets you may not know about.
See your RFC 1918 coverage #
runZero’s scans can help surface unmanaged subnets in your internal network, which may harbor a bunch of unmanaged devices. Our RFC 1918 scan capability can cover the entire IPv4 internal network address space (more than 21 million addresses), checking all potential places unmanaged devices could be hiding in your network. We’ve also developed a “subnet sampling” option as an informed approach to focus on statistically-likely-to-have-devices subnets so that the RFC 1918 scan runs in shorter time while still providing good coverage.
The interactive RFC 1918 coverage report presents discovered data in an easy-to-consume layout to show which subnets have been scanned, and includes additional data for unscanned subnets which might be active based on devices leaking secondary network interface information. This report allows you to “drill down” into subnets by clicking them to view discovered asset details within an address block.

Find unmapped assets #
Unmanaged devices on your network can also surface in runZero as an unmapped asset. An unmapped asset is a MAC address connected to a switch, but not found in an ARP cache or through any of the other techniques runZero uses for remote MAC address discovery. Unmapped assets could be unmanaged assets, but could also be managed assets that were not included in the scope of a particular scan. You can get a visual overview of where unmapped assets appear on your network via the switch topology report, with each switch showing the number of assets (including unmapped assets) attached to it. A single click on a switch with unmapped assets will bring up a “View unmapped assets” link to the associated unmapped MACs report, which provides MAC details and the switch port the asset is connected to. This is potentially helpful for further investigation.
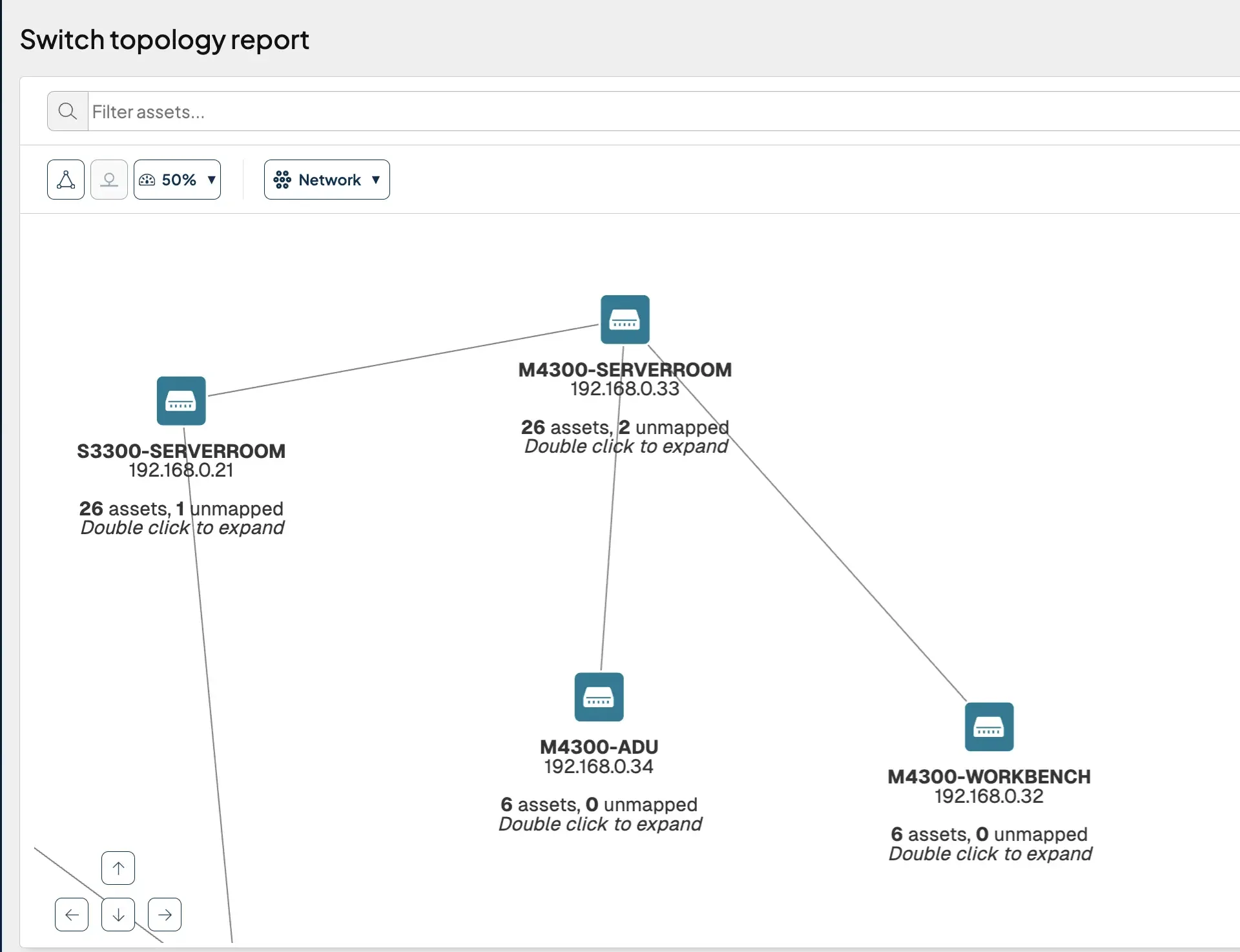
Search for devices missing agents in runZero #
Identifying assets that lack security or management agents is critical for maintaining a robust cybersecurity posture. These gaps in coverage can create significant blind spots, making it difficult for security teams to detect and respond to threats effectively. Without these protective measures, assets are more susceptible to attacks, which can go undetected, leading to potential data breaches and extensive damage.
Furthermore, missing these critical tools compromises compliance with regulatory standards and internal security policies, exposing the organization to legal and financial penalties. Ensuring all assets are equipped with necessary security and management agents not only reduces the risk of attack but also strengthens incident response capabilities and ensures a consistent and proactive security stance across the entire network.
runZero uses a combination of approaches to identify assets missing the security agents. Using 3rd party API integrations with security tools, runZero can import assets that have agents installed on them. As well as an applied research approach that identifies agent technologies that may be required on assets managed by your company or regulatory requirements.
You can find assets that are missing these agents via runZero inventory queries. The following are some examples of queries in the runZero console:
Endpoint Detection and Response (EDR):
The following query example will surface any Windows assets that are missing a CrowdStrike EDR agent:
os:windows and not source:CrowdStrikeFrom the runZero console the results of the query shows you the list of assets that match:
Mobile Device Management (MDM):
The following query example will surface any iOS assets that are not enrolled devices under Microsoft Intune Mobile Device Management:
not source:intune and os:"apple ios"From the runZero console the results of the query shows you the list of assets that match:
Vulnerability Management:
The following query example will surface any assets, that are not within the scope of Nessus professional scanning:
not source:nessusFrom the runZero console the results of the query shows you the list of assets that match:
You can also search for unauthorized operating systems or applications on your network, which can be indicative of an unmanaged asset. For example, if all or your Windows systems are only allowed to be running Windows 11 or Windows Server 2022, you can create a query to surface any potentially unmanaged Windows assets not running these recent versions:
os:Windows and not (os:"Windows 11" or os:"Windows Server 2022")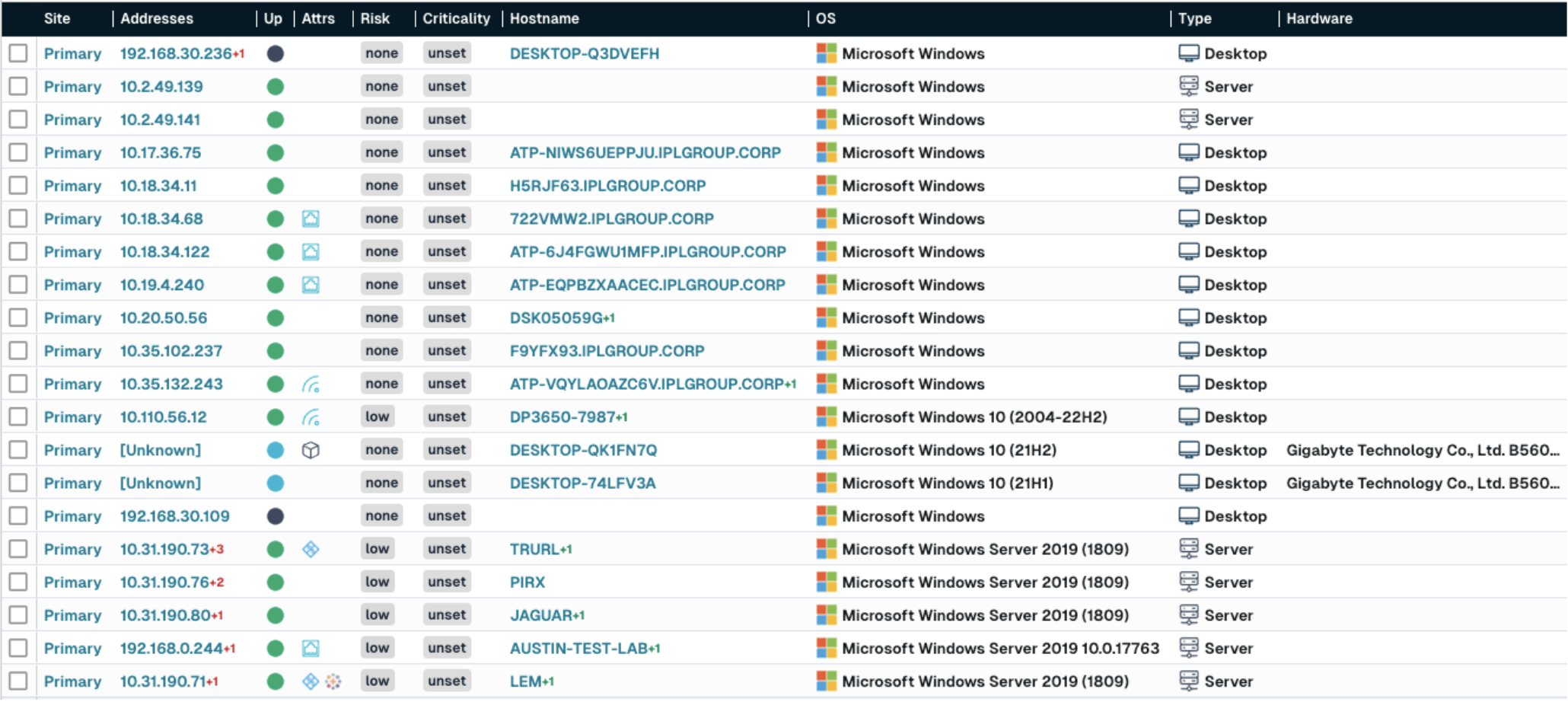
Track unmanaged assets with tags #
Tags are another runZero mechanism that can be used to surface unmanaged assets and also help “keep on top of” current asset ownership. This requires a bit of work up front to tag all managed assets, but requires little maintenance once in place.
Stay on top of unmanaged assets with alerts #
Alerts are a powerful way to leverage queries into timely notifications in-app or via email or webhook. For example, we can build alerts for any of the queries used in this article. Rules are checked when a scan completes, and for any rule that evaluates as “true”, an alert can be generated. Check out our “Tracking asset ownership with tags” article to learn how to set up an alert rule.
Network Bridges #
Network bridges are critical in cybersecurity because they connect different parts of a network, enabling data to flow between them. If a bridge goes unnoticed or isn't properly managed, it can allow attackers to slip through security barriers and move from one network segment to another. This could give them access to sensitive systems or data that were meant to be protected by network segmentation.
Unmanaged assets add to this risk. If these assets are connected through an undiscovered bridge, they become easy targets for attackers. Once compromised, attackers can use these assets to move across the network undetected, bypassing security controls.
Consider a scenario where a company has a multi-homed server connected to both the main office network and the R&D network. This server isn't actively monitored or regularly updated, making it a weak point. An attacker breaches the main office network, identifies the multi-homed server using network scanning tools, and leverages it to pivot directly into the R&D network. This bypasses the segmentation controls meant to isolate sensitive systems, allowing the attacker to exfiltrate R&D data or escalate their attack—all due to the lack of proper management and security on the multi-homed asset.
The goal of network segmentation is to prevent such scenarios by isolating different parts of the network to limit access and potential damage in the event of an intrusion. If bridges or unmanaged assets aren't properly discovered and secured, segmentation fails, allowing attackers to move freely between segments and putting the entire network at risk.
This is where the runZero Platform comes in. It provides a detailed visualization of multi-homed assets within an organization. Unlike a traditional network map, this report illustrates what assets are bridging different networks together, whether those are private networks (private IP ranges) or public networks (public IP range). To maintain clarity, assets detected with only a single IP address are excluded from the graph. runZero identifies these network bridges by detecting additional IP addresses in responses to common network probes, such as NetBIOS, SNMP, MDNS, and UPnP, and only reports bridges when at least one asset has multiple IP addresses.
The bridge report shows external networks in red, internal networks in green, and the multi-homed assets that bridge these networks. Zooming in will show asset and subnet details, while clicking a node will take you to the asset page for bridge nodes and to a CIDR-based inventory search for network nodes. This view is not a typical network map, but instead shows possible paths that can be taken through the network by traversing multi-homed assets. Assets where Rumble only detected a single IP address are not shown in order to keep the graph readable.
With this view of network bridges, security professionals can assess whether a low-trust asset, like a device on a wireless guest network, could potentially reach a high-value target, such as a database server in a cardholder data environment (CDE). This feature helps identify possible network segmentation violations and opportunities for an attacker to move laterally across the network.
Building a comprehensive external asset inventory #
Internal networks aren’t the only places unmanaged devices may exist. A public-facing web server could become orphaned, or a bad actor could DNS spoof/hijack a lesser-used company domain to redirect traffic to a phishing site they control. With just a domain name or ASN number set in the scan configuration, runZero can resolve the associated external-facing URLs and IP addresses to scan. And our hosted zone scanners can seamlessly run the scan, removing the step of installing an external-facing Explorer.
The runZero platform discovers externally facing assets through a combination of active network scanning, data integration, and continuous monitoring.
The platform actively probes networks to identify devices, services, and open ports exposed to the internet, using techniques like port scanning and service fingerprinting. By scanning public IP address ranges and integrating with external DNS, runZero identifies publicly accessible services, revealing potential external threats.
runZero also profiles web applications and analyzes SSL/TLS certificates to uncover web-facing assets and associated vulnerabilities. Additionally, it collects data from cloud platforms and DNS enumeration to detect publicly hosted resources and subdomains that might extend the attack surface.
Regular scans ensure that new or altered exposures are quickly identified and addressed. This approach allows runZero to effectively map and assess the external attack surface, aiding organizations in identifying known and unknown assets that are publicly accessible and potentially at risk to emerging attacks.
The following query example highlights externally facing assets including detailed information, sources for discovery, and associated confidence factors associated with a network zone named “US - New York”:
hosted_zone:"US - New York"Uncovering unmanaged assets with integrations #
At runZero, we understand the power of “better together”, and our development teams have been busy adding support for many product and service integrations. Some of these integrations can be leveraged to surface unmanaged assets in your network.
For example, let’s say your organization uses SentinelOne on all managed macOS assets. One day an employee connects their personal MacBook to the corporate network without authorization: a macOS device without SentinelOne installed. You can create a runZero inventory query to surface this asset (and any others like it):
os:macOS and not source:SentinelOne
As another example, let’s say your company uses Microsoft Intune on all managed Windows 10 and Windows 11 assets. You can create a runZero inventory query to surface any Windows 10 or Windows 11 assets connected to your network that are not known by your Intune integration:
(os:"Windows 10" or os:"Windows 11") and not source:Intune
Prefer to surface your runZero-discovered assets, managed and unmanaged, via another tool? We offer integrations for several popular services, including ServiceNow and Splunk, allowing you to leverage the power of runZero’s best-in-class discovery and asset fingerprinting with other applications.
Zero unmanaged assets #
Getting a handle on unmanaged assets is important, but it can feel like “one more thing” to do in an already-lengthy list of responsibilities. At runZero, we’ve done our homework through research and development to make finding your unmanaged network assets quick and easy. If you're interested in finding out what's on your network, start a free trial today.
















