While runZero is mostly used for asset inventory behind the firewall, you can also use its scanner to discover your external attack surface.
External scans are beneficial for a number of use cases, such as:
- Getting visibility into external hosts and exposed services
- Assessing infrastructure of corporate acquisition targets
- Performing vendor security screening
- Reconnaissance for penetration testing
Differences between runZero and EASMs #
New users sometimes wonder about the differences between runZero and solutions for external attack surface management (EASM), such as Censys and ShodanHQ. Many of these solutions scan the whole world so you can query their host database. However, network owners can ask to exclude their IP ranges for all users (i.e., not all hosts show up in your search). Some vendors will have tools or services that discover all of your externally-facing assets.
By contrast, runZero:
- Has the ability to discover public-facing hosts.
- Collects data through a combination of active scanning and integrations.
- Takes inputs in the form of ASNs, domains, IPs, and FQDNs (as well as public IPs discovered in internal scans).
- Can integrate with Shodan & Censys to identify hosts and augment data.
- Augments scans with other sources through integrations (e.g., cloud hosting providers, vulnerability scanners, and EDR platforms).
- Offers a much richer data set per asset.
How to scan your public-facing hosts #
If you don’t have access to runZero Enterprise Edition, you can sign up for a free 21-day trial to follow this walkthrough. The free Starter Edition doesn’t contain some of the features described in this blog post.
Step 1: Determining domains and ASNs to scan #
The easiest way to get started with external scans is through:
- Domains - There are several options for finding the domains associated with your organization. Best to check with the person who’s managing your domain registrations and renewals. Doing a reverse WhoIs lookup hasn’t been a good option for a couple of years now, but if you lack alternatives, use Whoxy to find all domains registered to the same company.
- ASNs - If you don’t know the ASN for your company, you can use a lookup service, such as ASNLookup to identify the ASNs for your organization.
For this example, let's scan the external attack surface of a real organization and its properties, but blur any identifying data to ensure that the organization doesn’t become a target as a result of this post.
Step 2: Adding Censys or Shodan integrations #
You can also discover your external hosts via Shodan or Censys integration. The integration can pull in additional machines that may not be in your ASN or domain scope. To use the integration, go to Inventory > Assets in your navigation menu and select Censys search or Shodan search from the Connect dropdown menu. You’ll have to set up credentials with an API key to build the query.
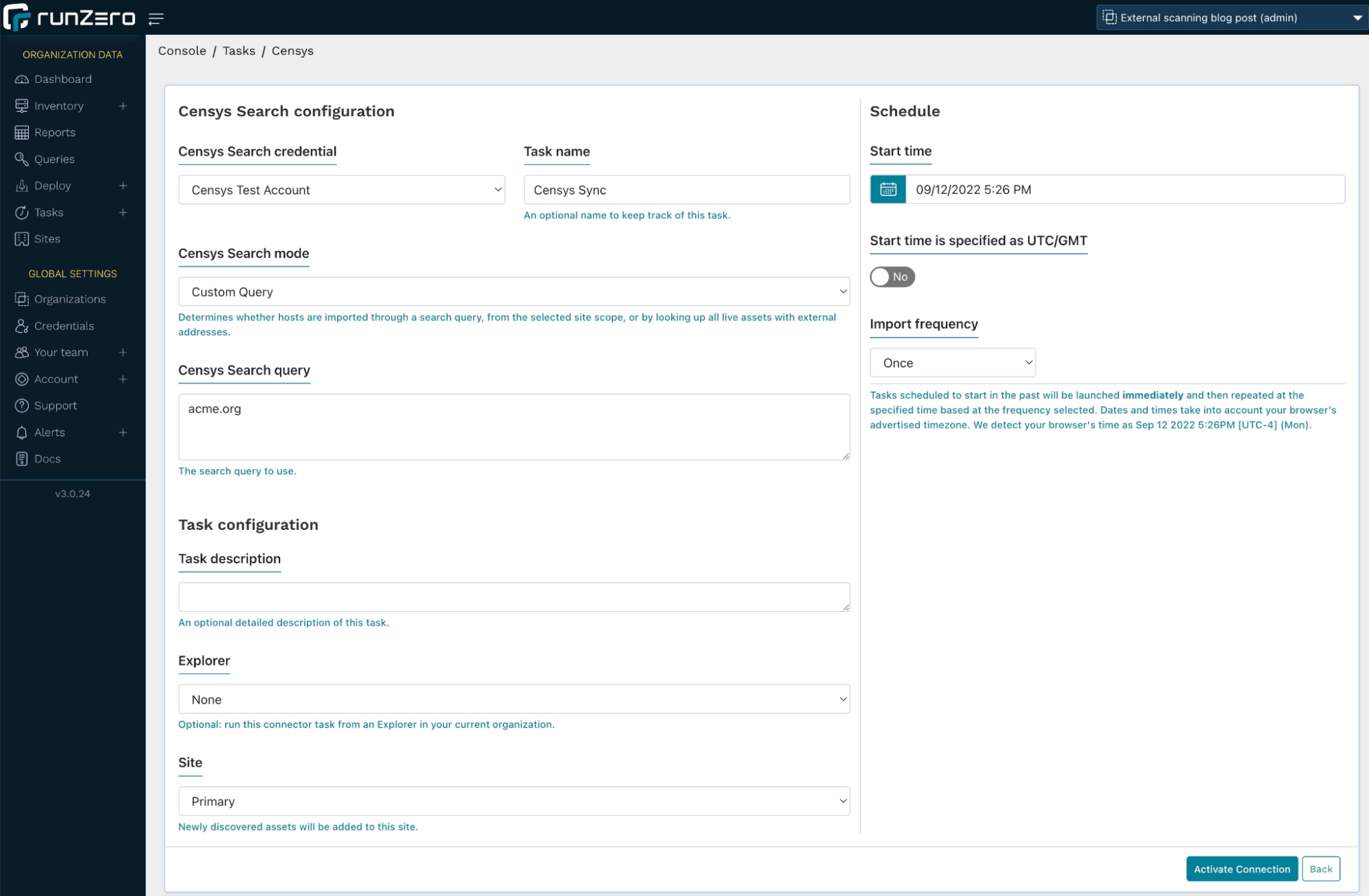
In the Censys configuration, we query acme.org in our search. This will also find any hosts that use the string acme.org in the common name of a TLS certificate. You can run this import either once or on a schedule.
Alternatively, you can set the Censys search mode to All external assets, which will not discover new assets, but enrich the assets already captured in runZero with Censys data. However, for this use case, we'll go with the former setting.
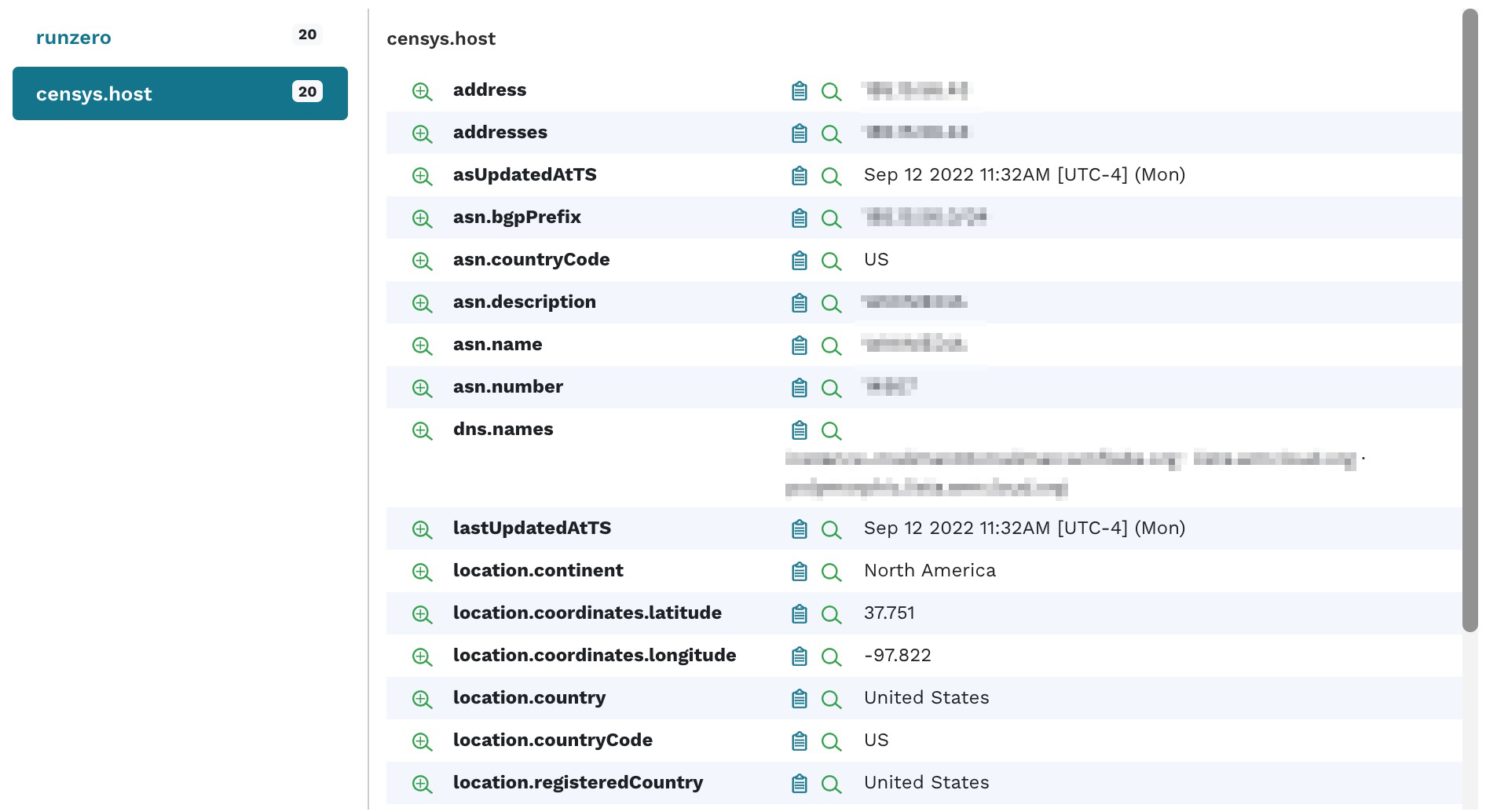
The import will pull any information about the matching hosts, including services and attributes, into your inventory. You should now see some assets with limited data being populated in your runZero inventory. You can view the details for one of the imported hosts and see the following information:
Step 3: Starting an external scan using hosted zones #
In runZero, set up a new organization or project, then go to the inventory, click the Scan button and select Standard scan.
From the scan configuration page:
- Choose US - New York as the Hosted zone (this is a runZero-hosted Explorer in the cloud).
- Increase the scan rate from 1,000 to 5,000 (to accelerate the scan).
- In the Discovery scope, enter the following data:
- public:all: This will scan all the public IPs that were pulled in via Shodan or Censys in the previous step. If you are scanning your internal network with runZero, this will also add all public IPs discovered by any other means into the scope.
- asn4:12345: Enter all ASNs in this format to target all IP addresses registered to this ASN. Note the digit 4 after ASN in the notation.
- domain:acme.org: Add all domains that you are targeting. runZero will add all subdomains connected to these domains.
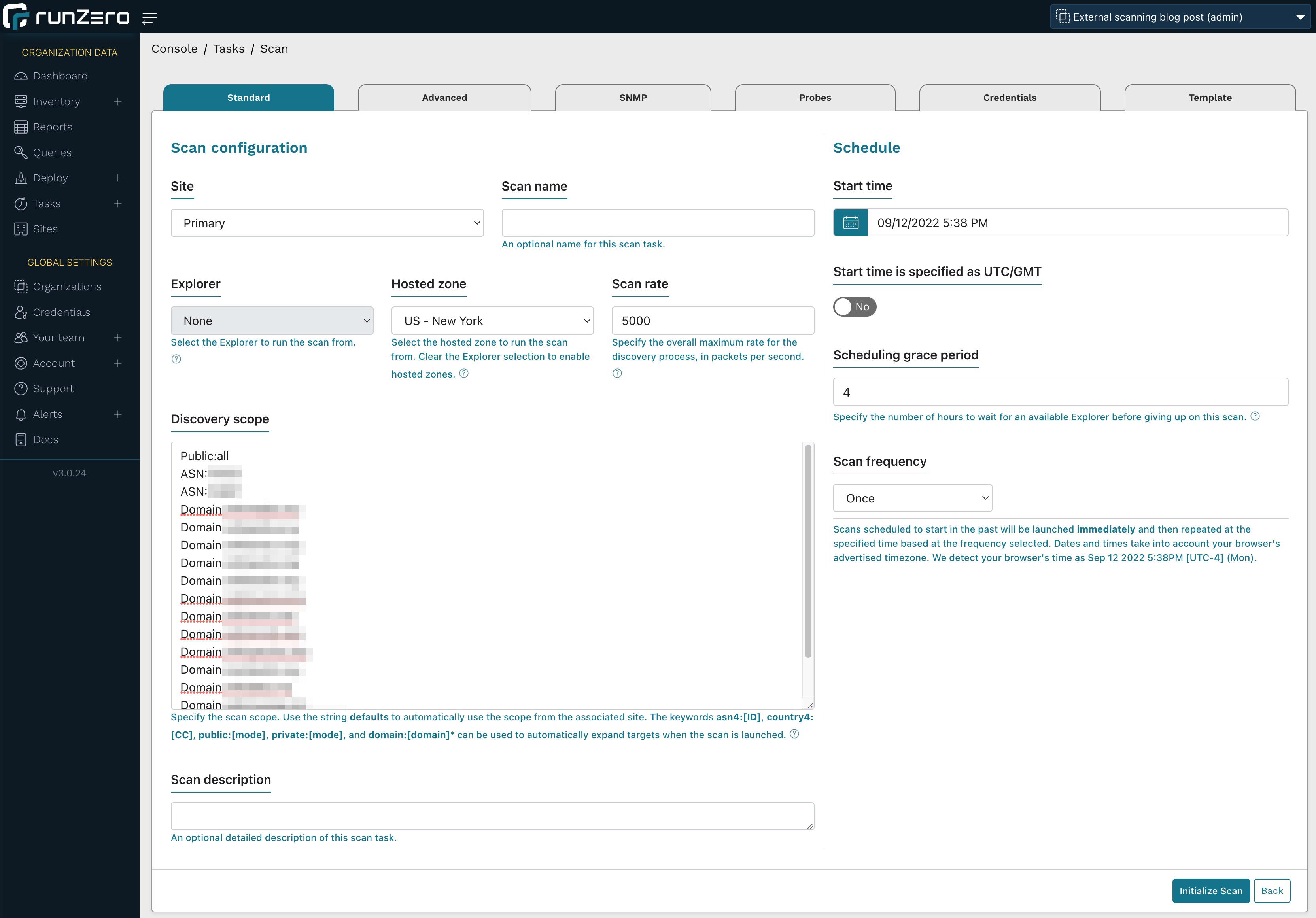
Click Initialize scan. runZero now looks up both the IPs registered under the ASNs as well as all subdomains associated with the domains you are looking to scan and displays a sample for confirmation. Confirm your scan settings.
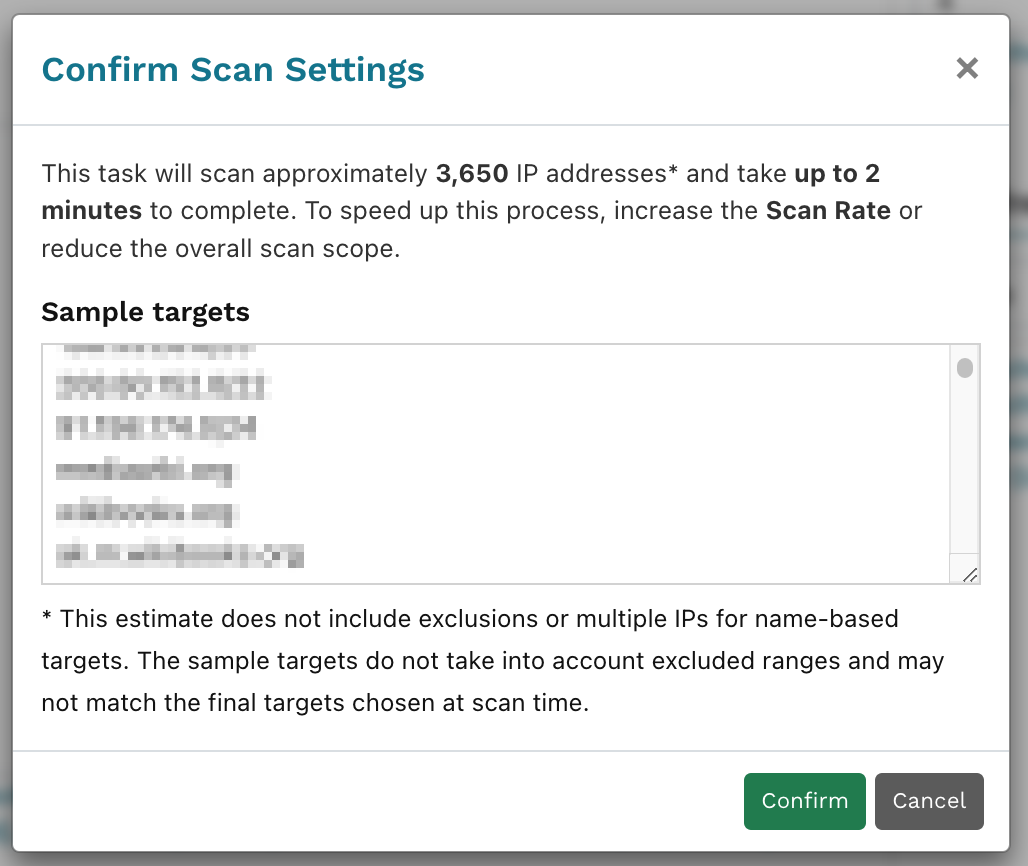
Once the scan task has completed, go view your populated inventory.
runZero hosted zones are deployed with Digital Ocean. If you prefer to host your own Explorer, we recommend Digital Ocean because AWS, Azure, and GCP all rate-limit or filter outbound scan traffic in a way that impacts the quality of scan results. The runZero hosted zones performed much better than running a scan from an ISP as well, regardless of whether a VPN was used or not.
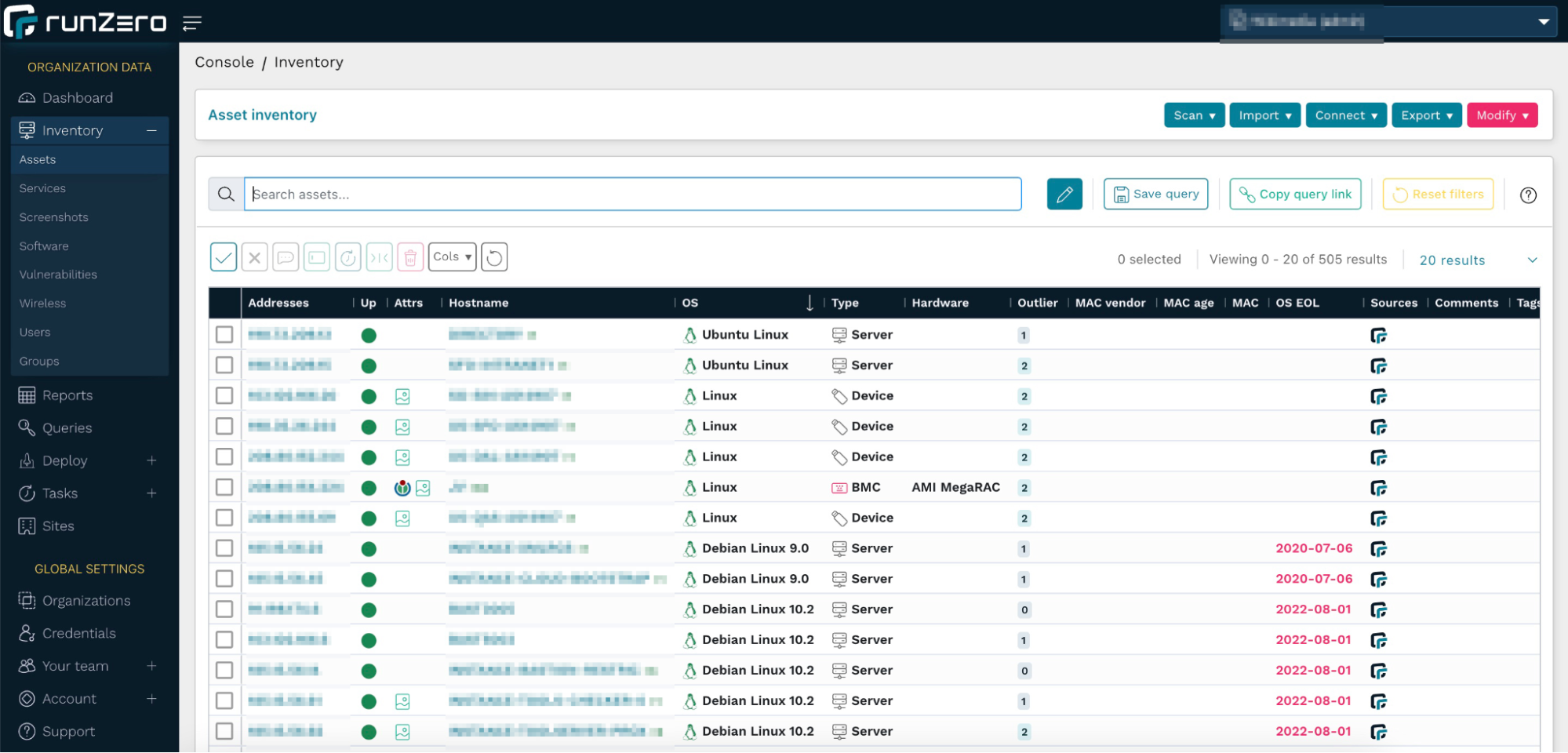
Step 4: Digging into your inventory #
Looking at this data set, there are quite a few hosts with EOL operating systems. You can use the following query to find these:
os_eol:<now
Some operating system vendors will enable you to purchase extended support services. To only view systems that are outside the extended support period, use the following query:
os_eol_extended:<now
Assets can often leak secondary IP addresses, often within the RFC 1918 range. These machines are potential pivot points into private network spaces. To find those quickly, use the query:
has_private:t
Best practices are to have as few services on a single host as possible, especially when they are public-facing, to avoid the risk of one vulnerable service compromising another one. Sorting the column with the number of services per host reveals one host with eight services. After opening the Asset Details page, we can see these in the Services section.
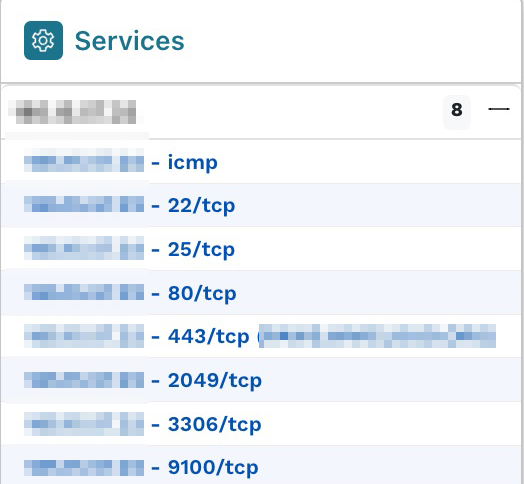
Each one of these services has an extensive list of attributes that provide more information.
Step 5: Finding problematic SSH services #
Looking at the SSH service on port 22, we see that it supports the authentication method of both password and public key. Allowing a simple password authentication may indicate elevated risk to your infrastructure.
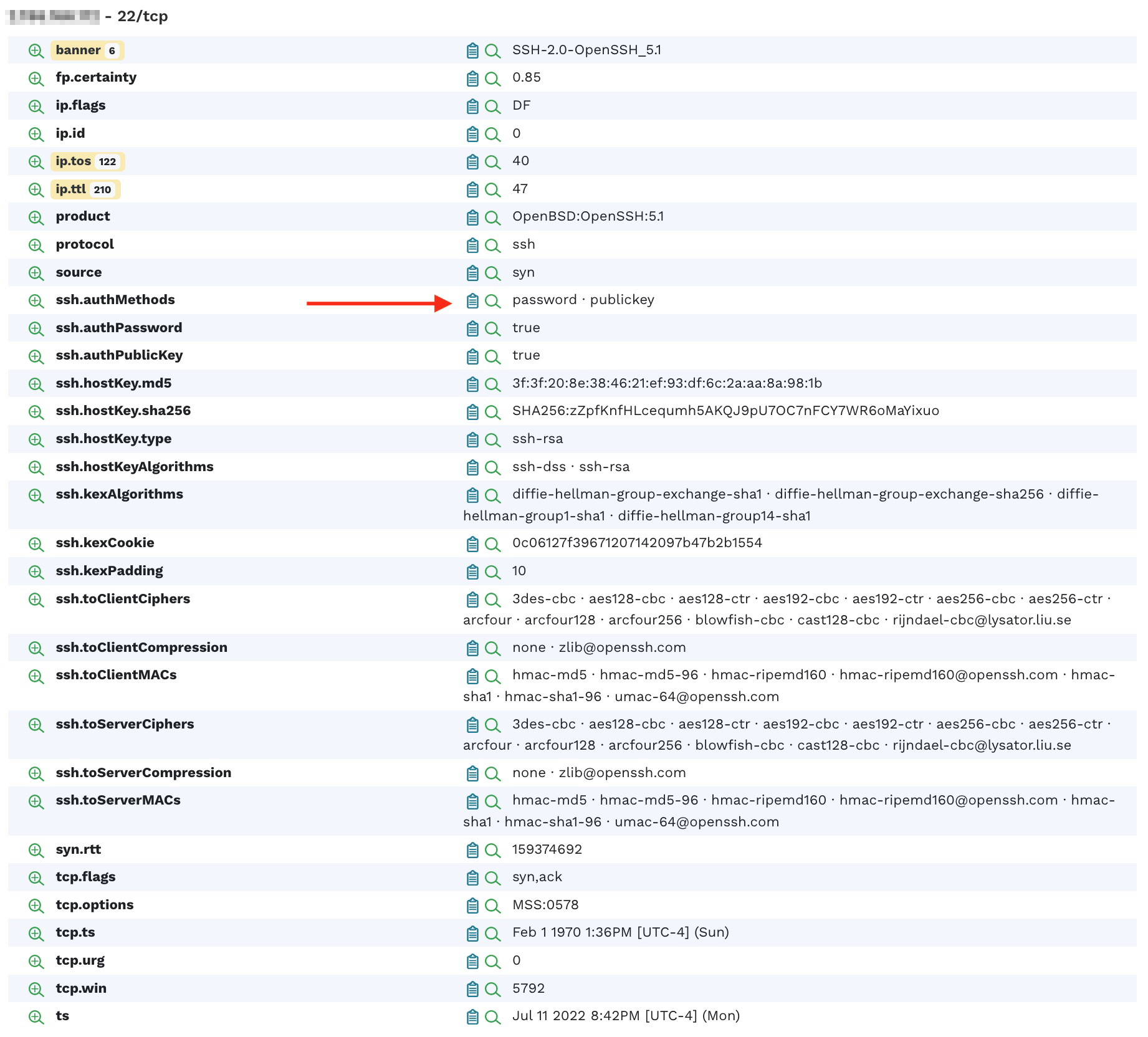
Clicking on the magnifying glass with the + sign next to the attribute name reveals that there are a total of 24 hosts that allow this kind of authentication.
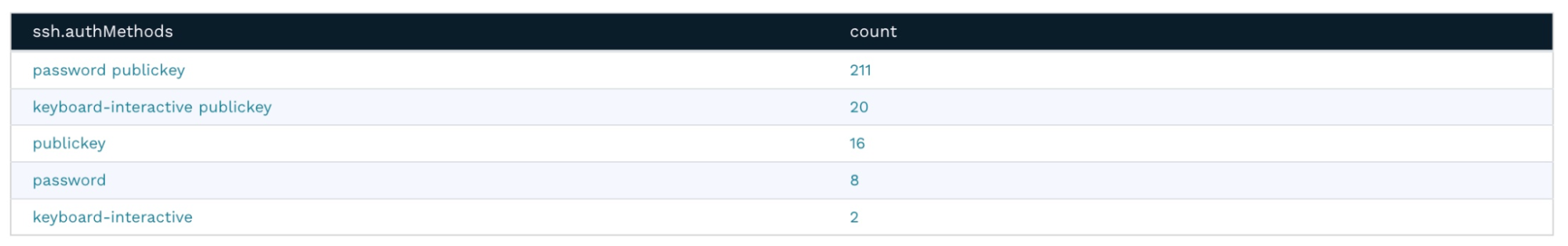
Clicking on the attribute value or the count will display a list of hosts that match the query.
Back on the Asset Details page, clicking the magnifying glass next to the banner shows an overview of all the different SSH versions deployed in the infrastructure.
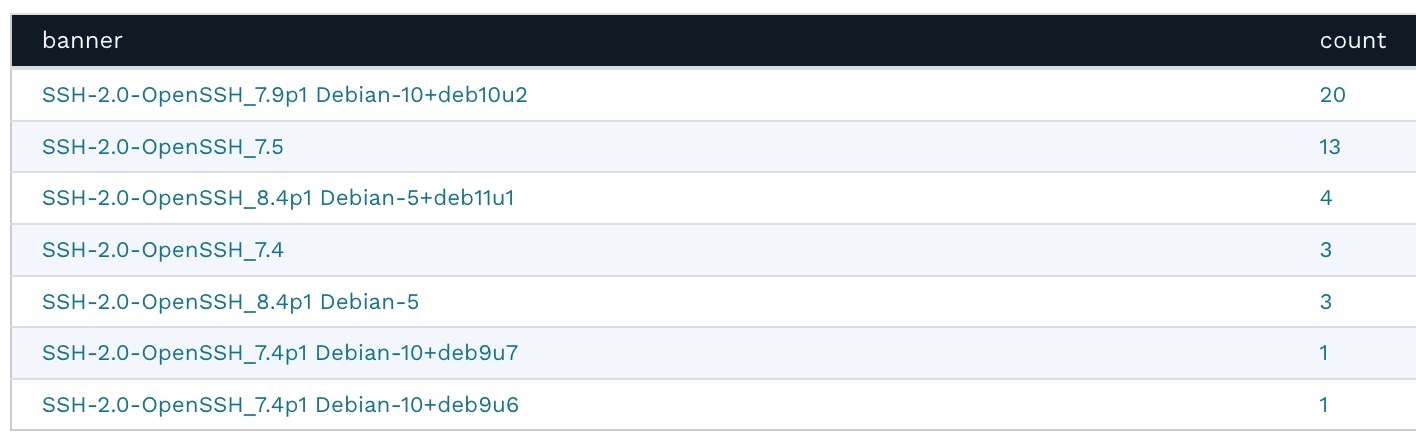
This works for all of the banner versions for other protocols as well. For example, you can very quickly and easily get a list of all of the Microsoft SQL Servers deployed in the environment, sorted by version number.
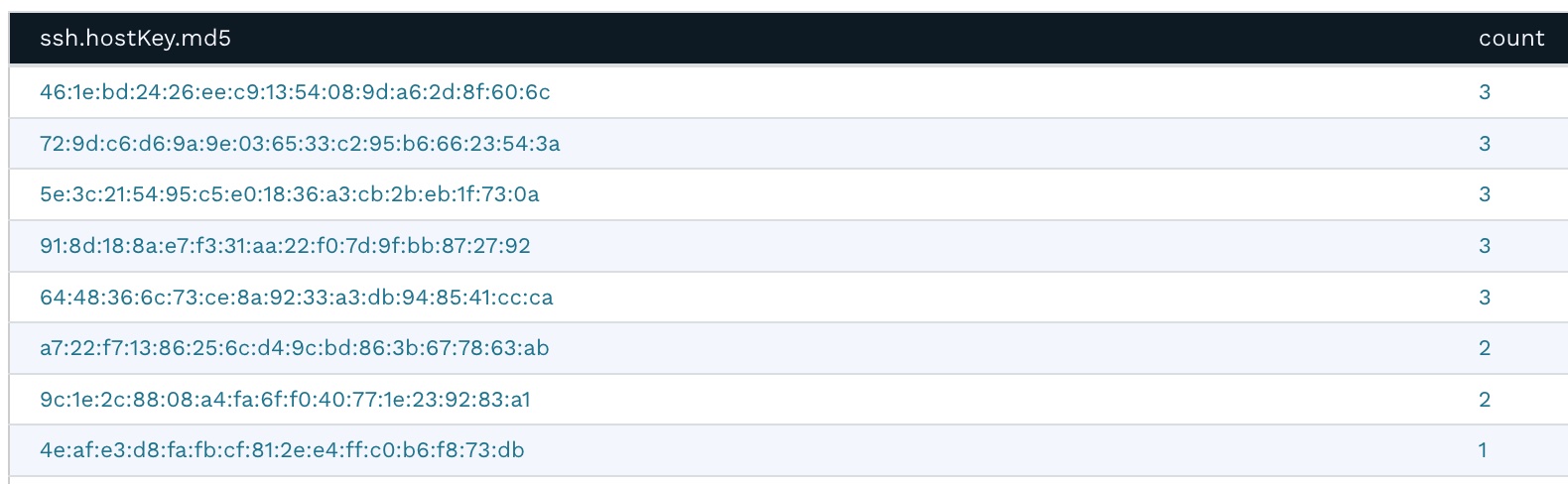
Going back to the Asset Details page, clicking the magnifying glass next to ssh.hostKey.md5 displays the frequency report for this attribute. It shows that several machines share the same SSH private key. This presents a security risk because if one of the hosts is compromised, it would also compromise other hosts sharing the same SSH private key. This typically happens when virtual machines are cloned without regenerating the SSH keys.
Step 6: Identifying databases exposed to the Internet #
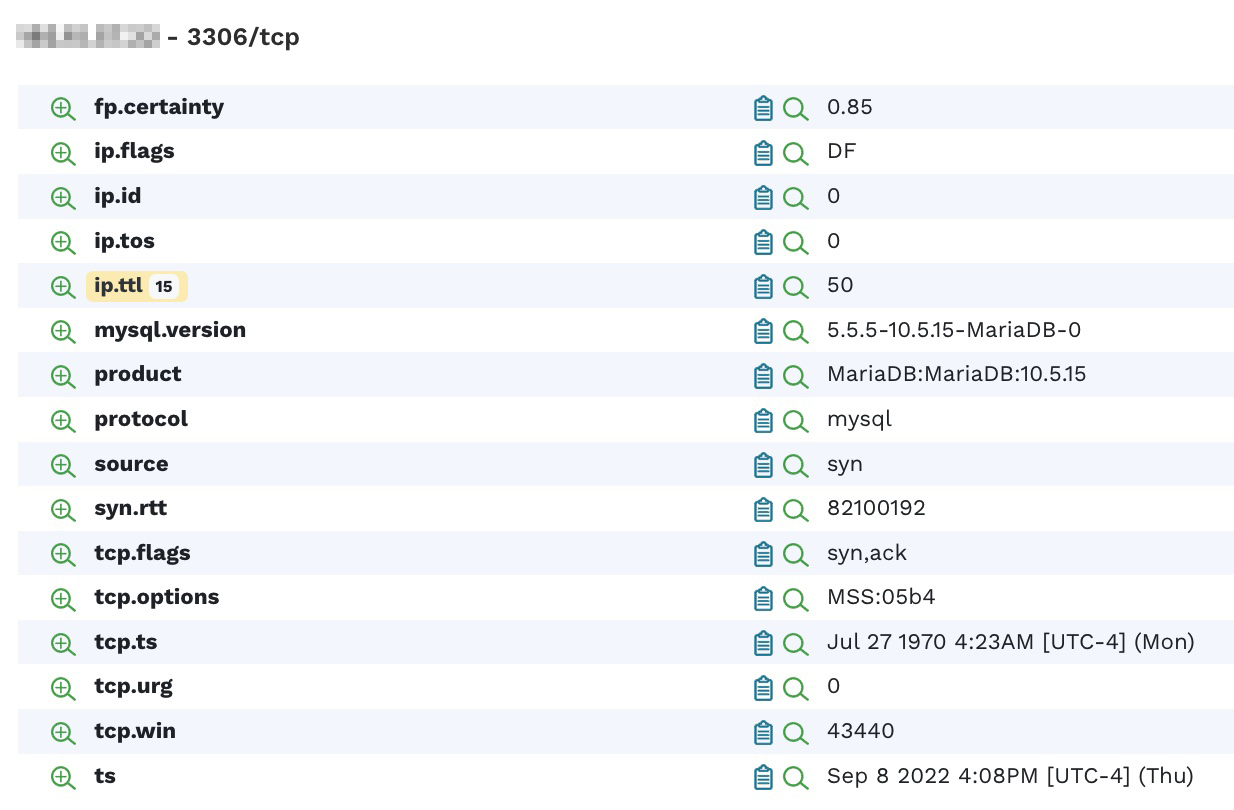
Generally, databases should be accessible only to the applications that require access. They should never be accessible on a public IP. The same host exposes MariaDB version 10.5.15 on port 3306, which has several associated security vulnerabilities.
Step 7: Looking at exposed services #
Let's move on to the Services Inventory now. A great way to find unusual services exposed on an external IP is to sort the ports by high numbers first.
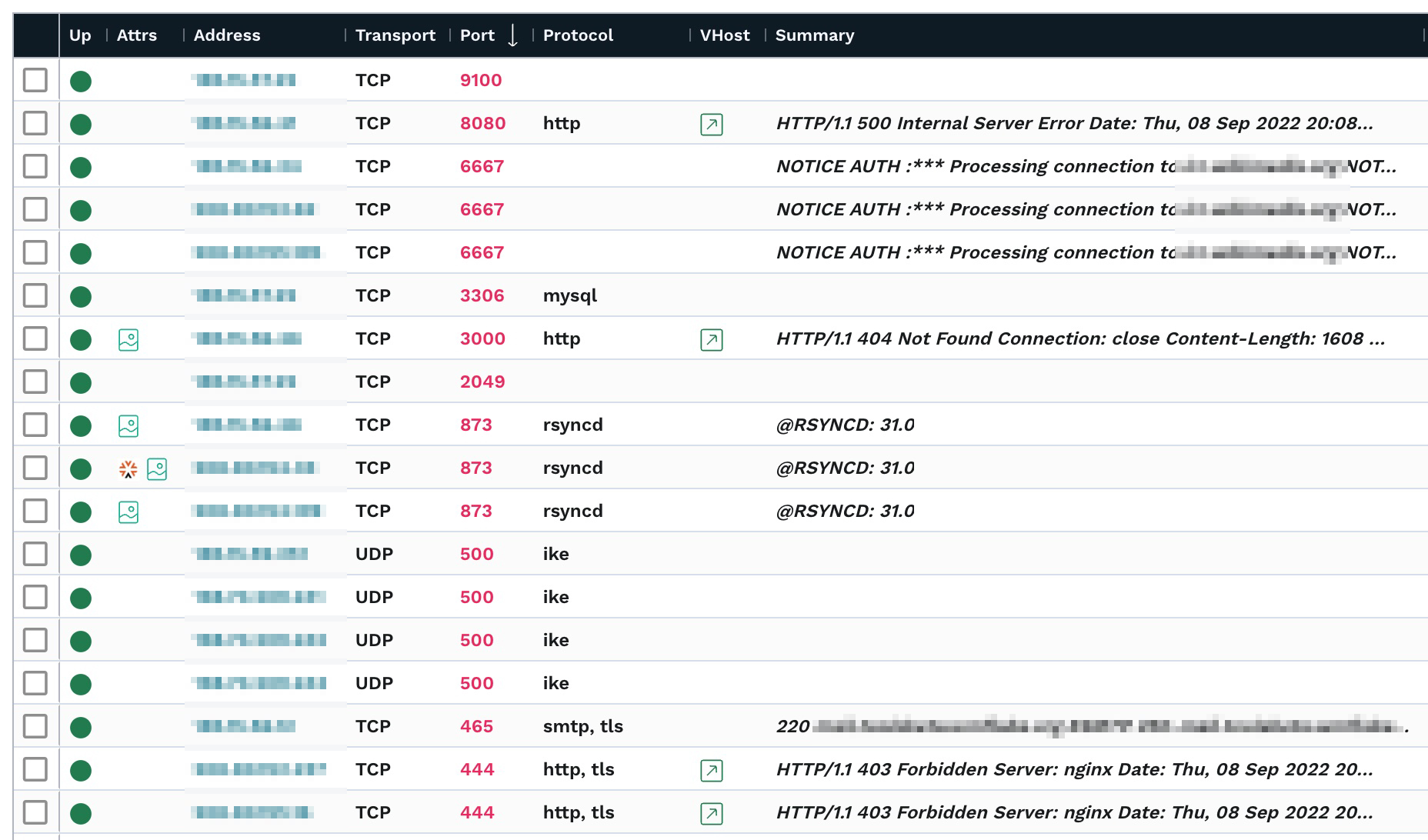
In this environment, we’re seeing a Prometheus Node Exporter metrics server on port 9100, three IRC services, a mySQL/MariaDB service, NFS on port 2049, and RSYNC on three different machines. These may all provide options to an attacker. For example, insecurely configured Rsync servers are found during network penetration tests about a third of the time.
Step 8: Browsing web service screenshots #
The Screenshots Inventory lists all screenshots taken from Web services. runZero uses the Google Chrome browser to render and screenshot any web pages. If you are using the cloud-hosted explorer as described above, you’re all set. If you are hosting your own explorer, please ensure that you have Chrome installed on the same machine to enable this feature.
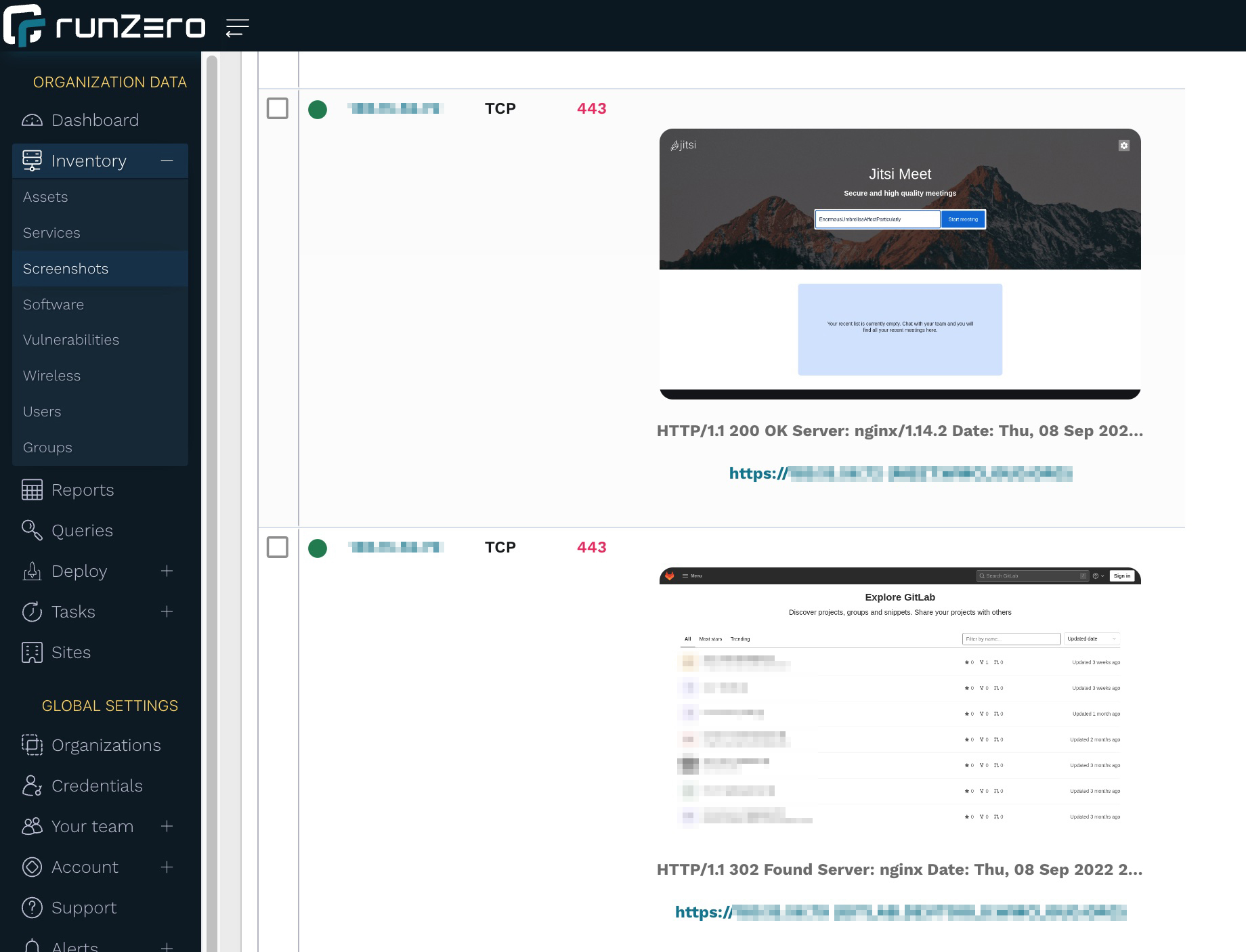
Browsing through the screenshots is a great, visual way to inspect exposed websites. In our example, we’re seeing Jitsi Meet and GitLab sites, which may be OK to host externally as long as they’re updated and use strong authentication.
Step 9: Looking at software inventory #
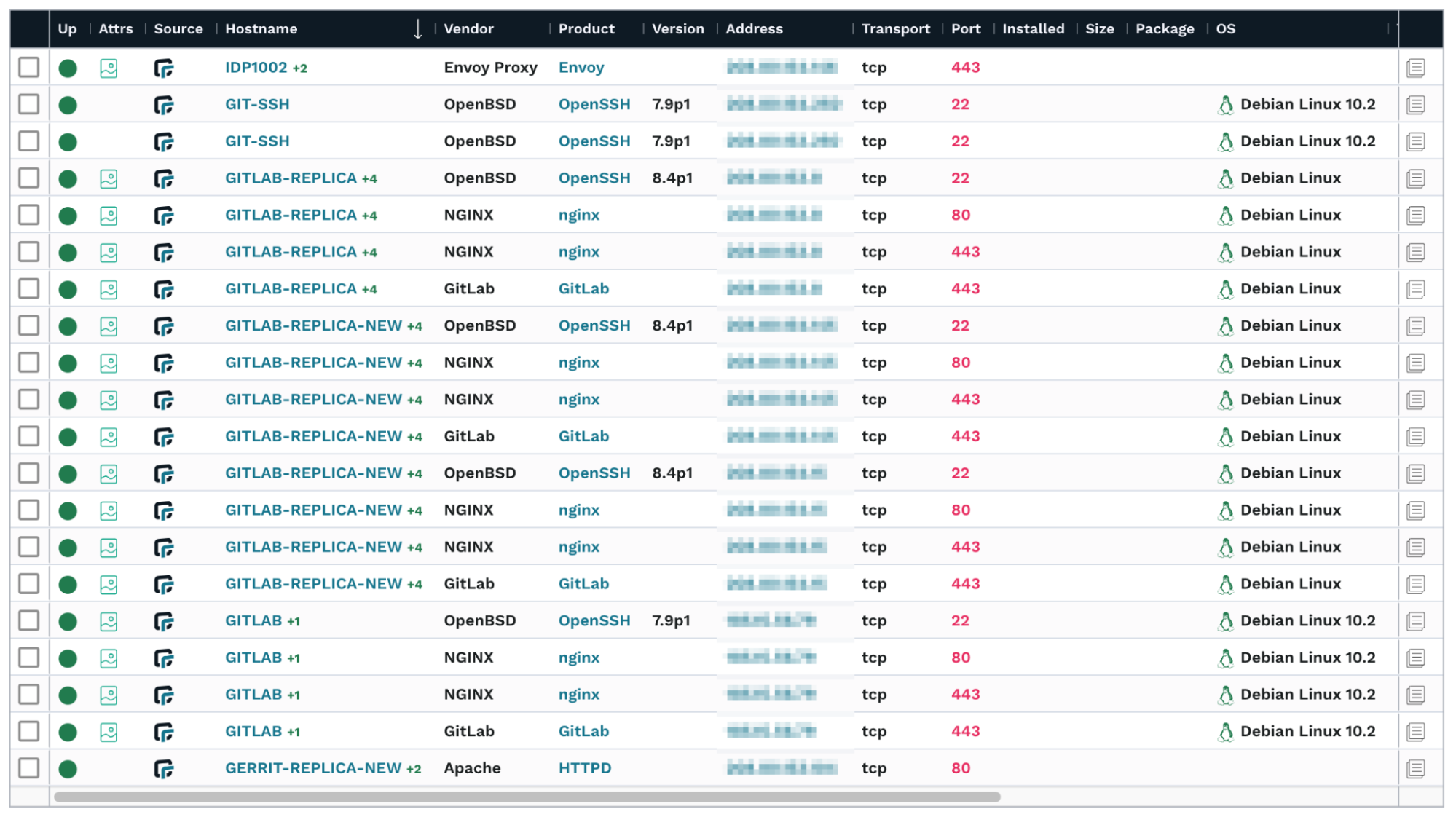
runZero can also infer installed software if it can be deduced either from a network scan or an integration. runZero's Software Inventory provides a great way to get insight into software installed on hosts that are reachable over the Internet.
A view that may be even better in understanding your product exposure is the Most seen products report on the dashboard. To access the report, go to the Dashboard and look for the Most seen products card. After you find it, click View more.
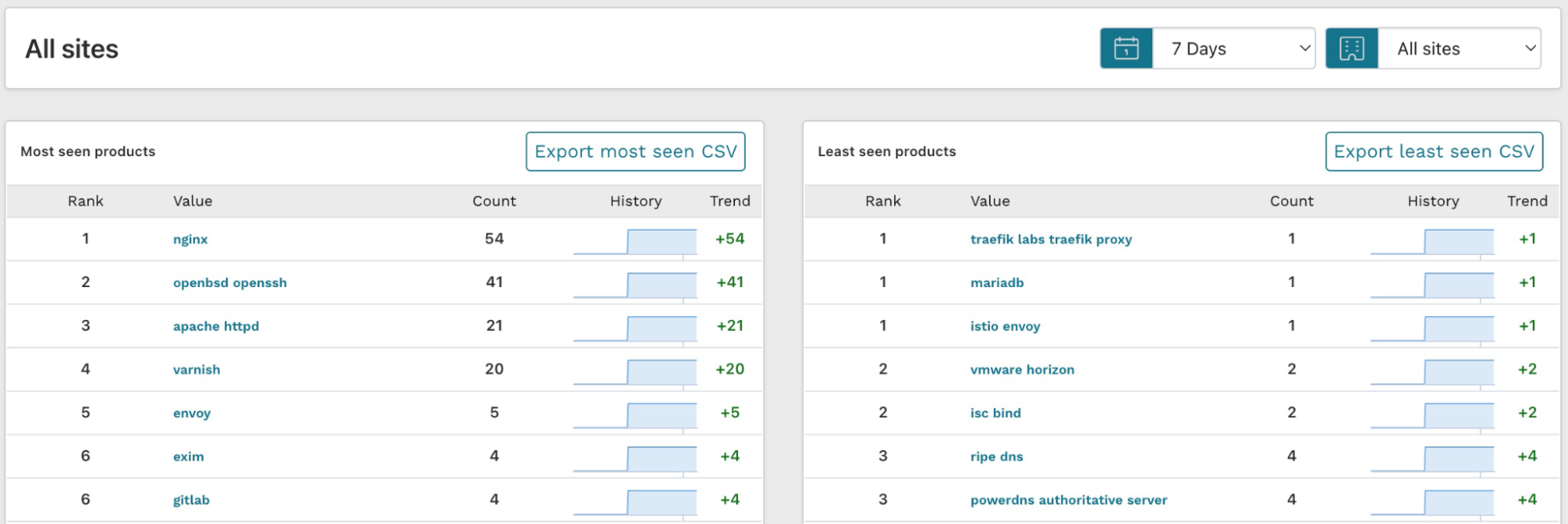
The results for least seen products are actually more interesting than the most seen ones because these show the long tail of the software inventory. If a piece of software is only installed once in your environment, it is less likely to be well configured and patched.
Step 10: Create a report for your external assets #
Now that you have discovered and analyzed all of your externally-facing assets, you can also generate a report for others to review. Go to Reports, find the External Assets Report, and launch it.
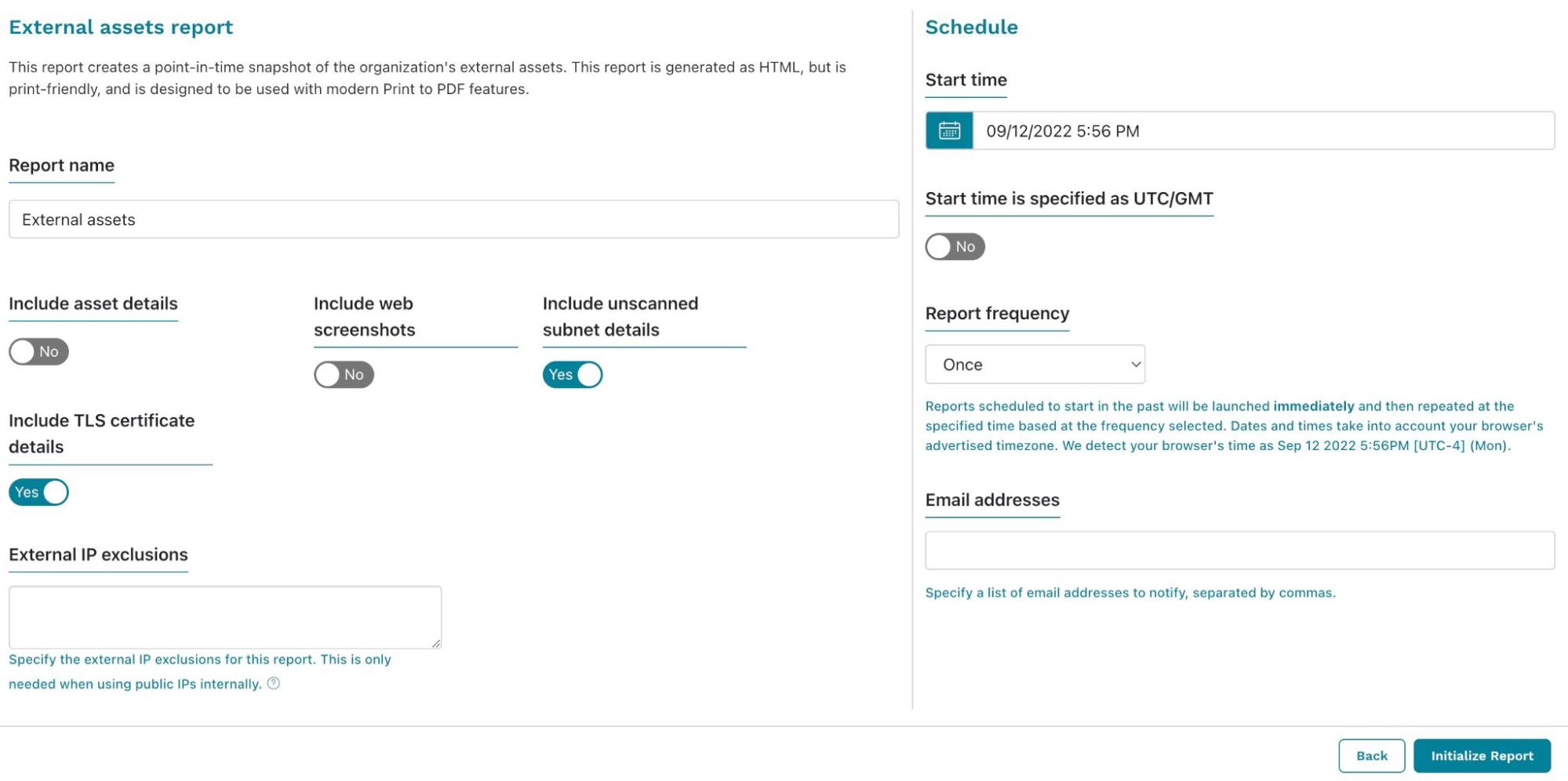
From the External Assets Report configuration screen, you can choose what you'd like to include in the results. Additionally, if you need to view it regularly, you can set up a schedule and email it to yourself (and any other runZero user who wants a copy). Initialize the report when you've finished configuring the settings. The generated report will display and show you the results. You can save the report as a PDF to easily share with others.
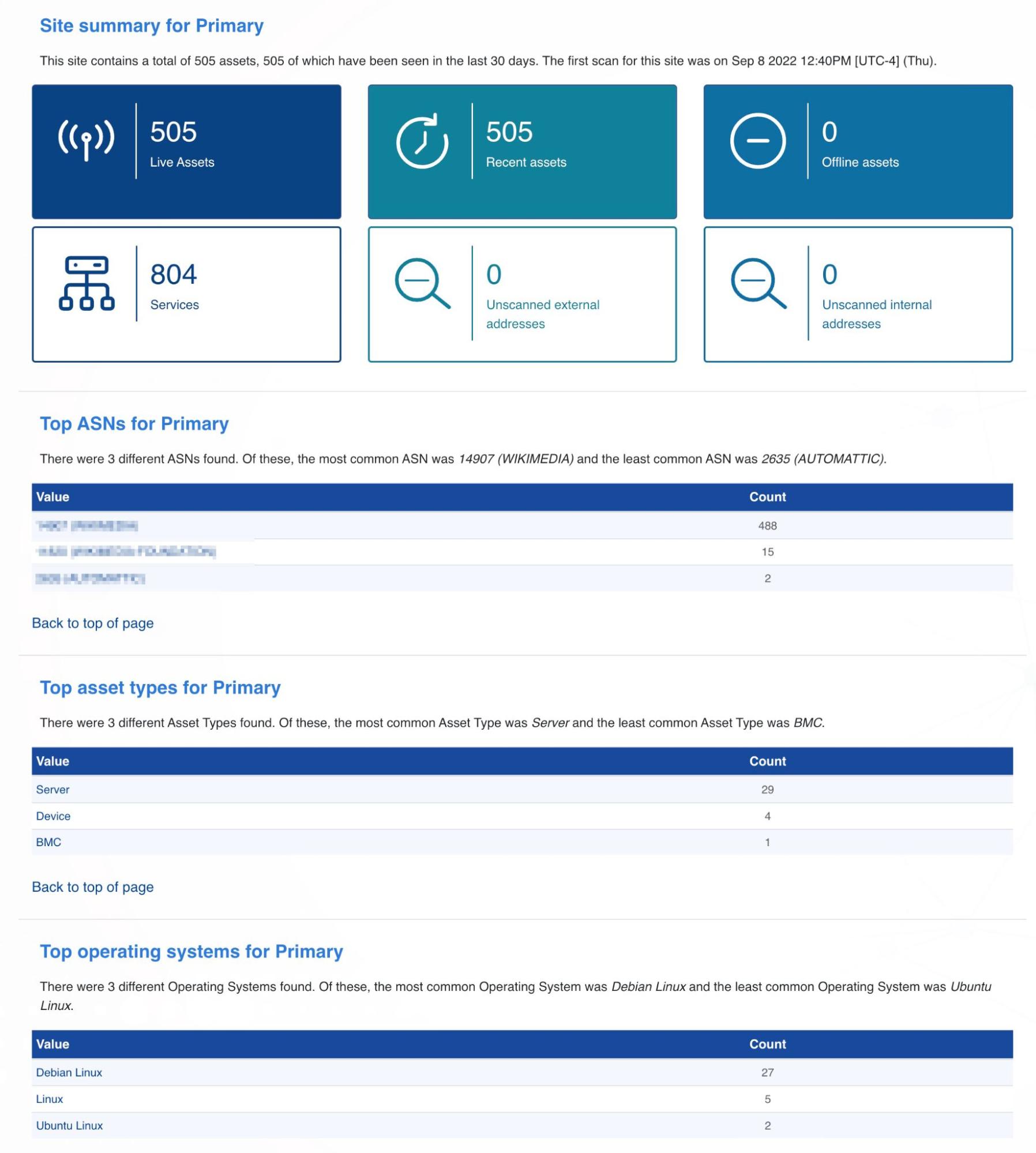
Step 11: Get alerted on changes to your external asset inventory #
If you work in enterprise security, you probably want to know about any changes to your external asset inventory. In this case, you should set up a Censys or Shodan import and run the hosted scan on a schedule. Then, you can set up alerts to trigger post-scan, so you know everything that has changed in your environment.
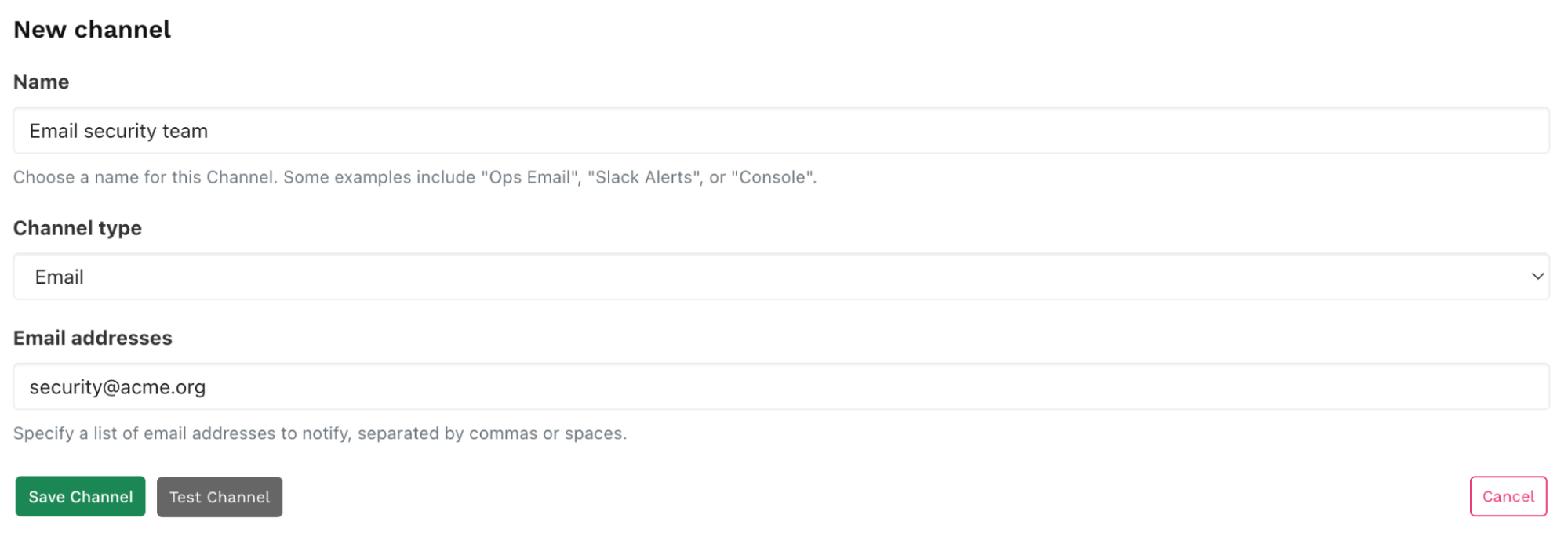
In this example we'll use email as the method of communication. To set up an alert, go to Alerts > Channels and click Create channel. Pick a name for your channel, select Email as Channel type and enter the email address you want to notify. Then click Save channel.
Go Alerts > Rules, and click Create rule. Select new-assets-found and click Configure rule.
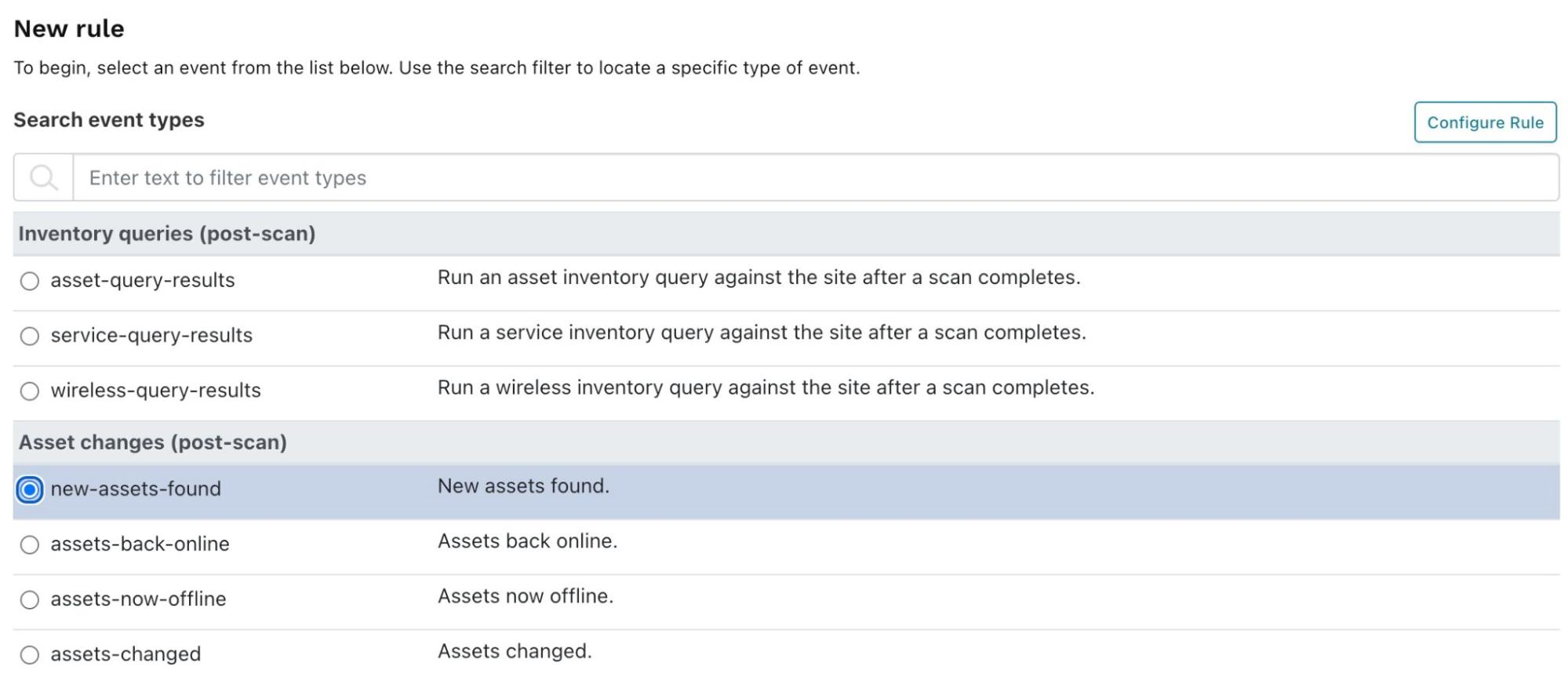
When the New rule configuration page appears, enter the following:
- Name:
- A name for your rule.
- Conditions:
- Enter 0 to the right of is greater than. This will trigger the rule if there are any changes to assets.
- In Limit to organization, select an organization if you have several in your account. You may choose a different organization (or site) for your external point of view rather than your internal assets.
- Action:
- Choose the notification channel you just created.
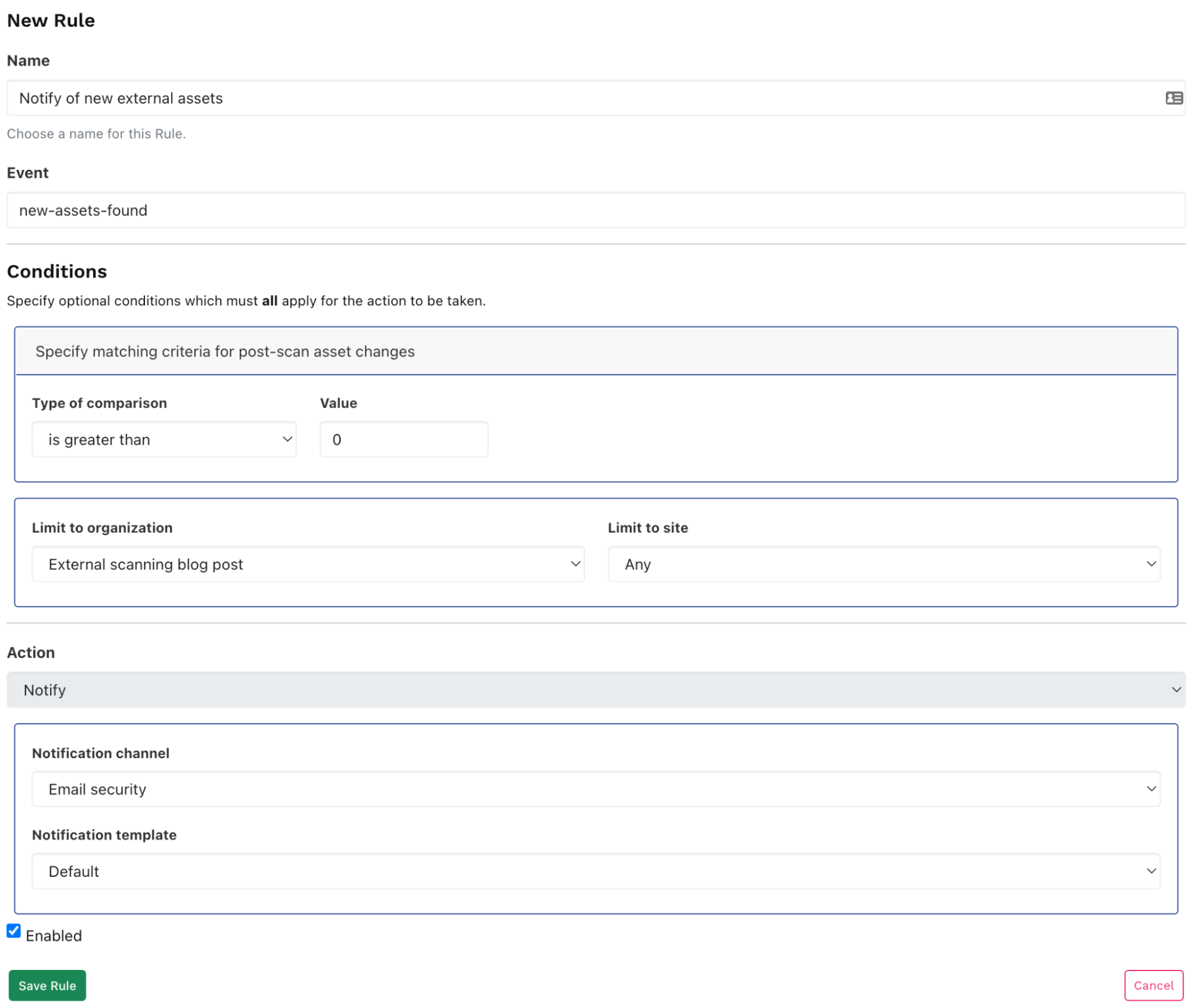
You’ll now be notified after each import or scan if the assets have changed.
Getting started with runZero #
As a next step, you should set up another organization and to scan your internal network to get a better understanding of your asset inventory. You can sign up for the free 21-day trial. If you are a private user or work for a company with less than 100 assets, you can use runZero for free.
















