Make new friends, but keep the old: one is silver, the other gold.
Despite enormous advances within information technology, security practitioners are still plagued by common problems. Advances in cybersecurity defenses and overall security awareness are helpful, but organizations still struggle with end-of-life (EOL) assets scattered across the attack surface. This can be a surprisingly difficult problem to solve and, most importantly, from the attacker’s perspective, EOL assets still provide easy footholds into an environment.
End-of-life is not the end #
All of the system hardening and security patches in the world cannot protect a system that is not updated to use those features. System vendors generally provide patches and updates for a limited timespan. After that point, end users must invest in an upgrade to a newer version of the system or fend for themselves and hope for the best with an EOL, outdated asset lurking on the attack surface.
EOLed systems often stick around for years, mostly forgotten but still part of an organization’s infrastructure and, therefore, its attack surface. New vulnerabilities are still discovered and exploited in these outdated systems as the April 2024 D-Link NAS issue illustrated. Despite the known exposure, being EOL means that fixes will not be forthcoming.
While this may seem like an academic exercise, EOLed systems are surprisingly common. Our findings show many still-active EOLed operating systems in various environments.
Operating system end-of-life #
Operating systems typically have multiple phases of vendor support, referred to as a support lifecycle. The duration of the lifecycle and services provided in various stages vary from vendor to vendor, usually tapering off with fewer updates and patches in later stages.
The two phases we are most concerned with are:
Mainstream support during which vendors release patches that may add new features, fix bugs, or mitigate security vulnerabilities.
Extended support during which only critical bugs and vulnerabilities are addressed.
While some vendors’ terminology and phases may slightly differ, generally speaking, most support lifecycles can be broadly mapped to these two phases.
When a vendor stops providing upgrades for non-critical issues, the product is considered in an “End-of- Life” (EOL) status. There may be an additional period known as “Extended-End-of-Life” (EEOL) during which the vendor continues to provide updates for critical issues. EOL and EEOL can happen concurrently or separately depending on the system and the vendor. Most importantly, after EOL, systems no longer receive critical updates or security patches, and thus become much greater risks to keep around.
But around they are! Systems have a long tail: if they still work, replacing them with a supported alternative may be more trouble than it’s worth. In some cases, the responsible staff can’t or won’t; in others, the system may host critical functions that are not supported on newer systems. Uptime guarantees and financial considerations may also play a role.
When we look at our sample data for operating systems that are past their extended EOL dates, we see that chart toppers are a pretty even split between Windows and various Linux distributions:

FIGURE 1 - Top OS past extended EOL.
The presence of Ubuntu 18.04 isn't surprising as it only reached Extended EOL just over a year ago in June of 2023. Ubuntu is often a go-to Linux distribution for businesses and home users alike as well as very popular in cloud environments. Windows Server 2012 R2 is also unsurprising; it reached extended EOL only very recently, in October of 2023. While running an OS a year past extended EOL is unfortunate, it’s not unusual for server migrations to drag on past EOL dates due to logistical and compatibility concerns.
The next major group is composed of various Windows 10 releases that, were they combined, would dominate the chart at 21.55%. Most of these are running the Windows 10 21H2 which reached extended EOL very recently in June 2024. Windows 10 was originally released in July of 2015. Microsoft has generally released two major updates for it every year since. Typically, updates released in the first half of the year are supported for 18 months and those released in the second half are supported for 30 months. There are some variations on this theme, with Long-Term Servicing Channel (LTSC) editions, for example, having longer lifespans. Windows 10 22H2 is the final version of Windows 10 and will reach extended EOL in October 2025.

FIGURE 2 - Windows 10 past extended EOL.
Exposed systems past extended EOL #
While operating systems outside of their extended lifespans are always worth looking into, those with exposure to an external attack surface are particularly worrisome. Of all systems exposed to an external attack surface and for which EOL data was available, 15.99% were past their extended EOL dates. That means that roughly 16% of all devices exposed to external attackers are probably not receiving security updates.
For server operating systems specifically, when we group them by family, we see that the largest block are Windows hosts. The percentage may be higher than expected based on Figure 1 above. This is due the long tail of various Windows Server versions going back to Server 2008 R2.
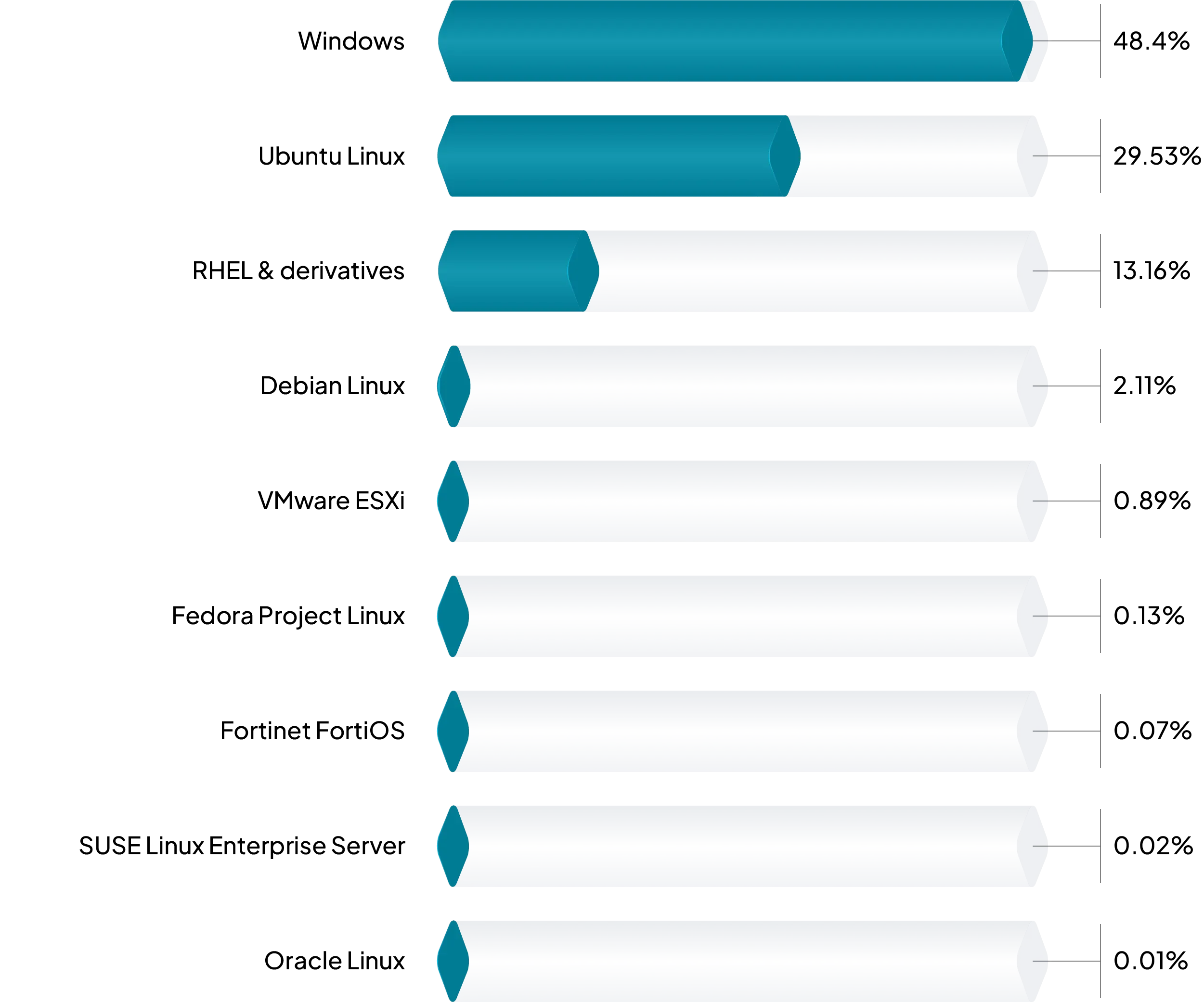
FIGURE 3 - Server operating systems with external attack surface exposure, past extended EOL.
Case study: the Boa web server #
The Boa webserver is an open source web server designed to have low resource requirements for users and to be compatible with embedded applications. The last official release of the Boa webserver, version 0.94.14rc21, was in February of 2005. For comparison, the Colts have won a Super Bowl more recently than the latest release of the Boa web server, and the Colts haven’t won a Super Bowl since 2007!
There are known vulnerabilities in Boa that have been exploited in critical infrastructure in the past. For example, in November 2022, Microsoft disclosed that Boa web servers in Internet-of-Things (IoT) devices were a common attack vector against power grids in India.
While it is relatively easy for an administrator to determine if a server is running Boa, it is much harder to detect in an embedded device. Boa is common in embedded devices like security cameras and IP phones that are widely deployed in enterprise networks. Therefore, curating an accurate inventory of an organization’s embedded devices, not just servers, that are running Boa is critical for protecting these networks.

FIGURE 4 - Boa web server version distribution in runZero data.
Embedded devices running Boa | |
|---|---|
Network-attached camera | 92.3% |
| Media & telephony devices | 5.5% |
| Environmental control devices | 0.9% |
| Network devices | 0.9% |
| Industrial control devices | 0.3% |
FIGURE 5 - Device types still running Boa in sample runZero data.
New-Old Friends #
We'd be remiss if we didn't mention common operating systems that will reach extended EOL soon. If any of these operating systems are running in your environment, we strongly recommend that you start planning for replacement or mitigation sooner rather than later.
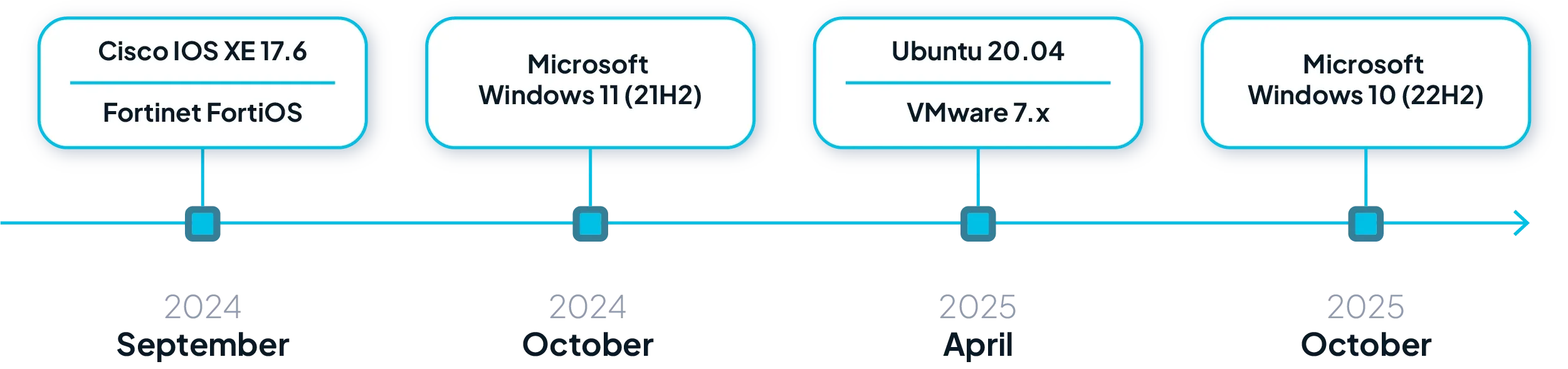
FIGURE 6 - Common OS approaching extended EOL.
Final Thought #
The prevalence of EOL systems within organizational networks remains a significant security concern. Despite advancements in security technology and practices, these outdated assets continue to provide attackers with easy entry points. Addressing this issue requires a proactive approach to asset discovery, exposure mitigation, and vigilant attack surface management to ensure that all components of your network, regardless of age, are secure and up-to-date.
runZero customers can find assets that are past their extended EOL by using the Policy: Extended End-of-Life operating systems canned query. You may need to add the OS EOL Ext. column in the Asset inventory in order to view the value.
Don’t forget to download the runZero Research Report to learn more about the state of asset security.
Not a runZero customer? Start a free trial and gain complete asset inventory and attack surface visibility in minutes.

















