runZero tracks vulnerabilities on assets discovered by runZero queries and numerous third-party integrations. We're pleased to announce that the Platform now enriches these vulnerability records with information from the CISA Known Exploited Vulnerabilities (KEV) catalog, the VulnCheck KEV list, and the Exploit Prediction Scoring System (EPSS).
The CISA Known Exploited Vulnerabilities Catalog #
The United States Cybersecurity and Infrastructure Agency (CISA) is a federal agency tasked with informing other government agencies about cybersecurity threats, information security best practices, mediation recommendations, and so on. It is also responsible for coordinating defense of critical infrastructure, such as electrical grids, water treatment systems, pipelines, and air traffic control systems.
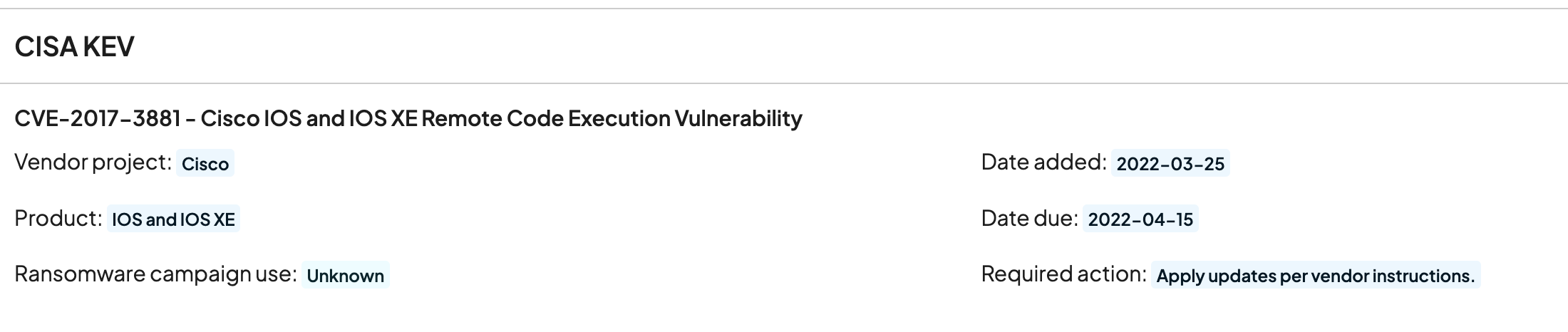
CISA publishes a regularly-updated list of cybersecurity vulnerabilities that are known to be exploited in the wild: the Known Exploited Vulnerabilities (KEV) list. The CISA KEV list currently catalogs 1,127 vulnerabilities in hardware and software that CISA has evidence of being actively exploited.
In this case "active exploitation" means that CISA has reason to believe that threat actors are currently exploiting these vulnerabilities for malicious purposes. If a vulnerability appears on this list, it should be considered a high priority; it represents not just a vulnerability, but one that is known to be under active attack.
If a vulnerability has an associated CISA KEV record, runZero will display it on the vulnerability's information page. Here's an example from the runZero Platform:
The VulnCheck KEV List #
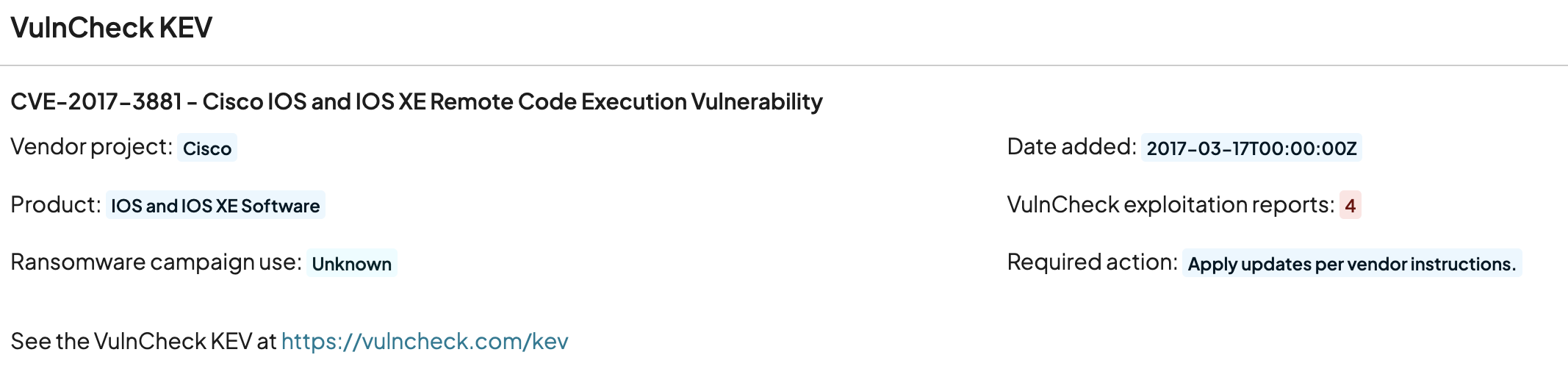
VulnCheck, a leading cybersecurity intelligence vendor, also publishes their own Known Exploited Vulnerabilities list (the VulnCheck KEV) that is timely, accurate, and frequently updated. runZero can now enrich vulnerability information with input from the VulnCheck KEV. Here's an example:
Searching KEV Lists #
It's easy to locate vulnerabilities that appear on the KEV list by visiting the Vulnerability Inventory in runZero and using the kev: search keyword. Search for membership in a specific KEV list simply by providing its name:
kev:cisa kev:vulncheck
Or look for vulnerabilities that appear on any KEV list (including any other KEV lists that may be added in the future):
kev:any
These query terms also work in the Asset Inventory to find assets with vulnerabilities that appear on the relevant list(s) and on individual assets, as well.
The Exploit Prediction Scoring System #
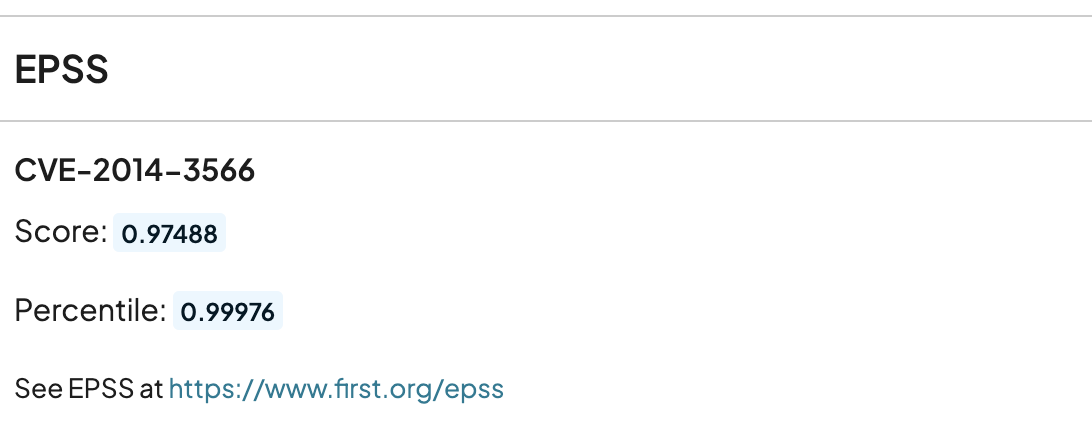
Additionally, runZero now integrates with the Exploit Prediction Scoring System (EPSS), a scoring system that predicts the likelihood that a given vulnerability will be exploited in the wild. EPSS provides a score between 0.0 (extremely unlikely to be exploited) and 1.0 (is definitely being exploited). You can search for vulnerabilities by their EPSS scores using the epss_score search term in the Vulnerability Inventory and for assets with EPSS-scored vulnerabilities in the Asset Inventory. The conventional runZero numeric search operators can be used, for example:
epss_score:>0.9 epss_score:<=0.8
In general, vulnerabilities with scores higher than around 0.9 should be looked at very closely.
Like the KEV lists above, vulnerabilities with EPSS scores will have that information displayed in the vulnerability view:
A Bonus: Faster CVE Searches! #
The work to integrate with the CISA and VulnCheck KEV lists and the EPSS resulted in a nice little bonus: searches by CVE should now be considerably faster!
















