Knowing what’s connected to a network is important for securing your organization. There are a fair amount of free and commercial options out there. We see security teams using a mix of runZero, Nmap (sometimes with Zenmap), Angry IP and Masscan.
In this article, we compare and contrast several free tools and provide our take on why we believe runZero is best suited for corporate security teams – particularly teams that are looking to gain continuous visibility into their asset inventory for risk management, incident response, and penetration testing purposes.
Free network scanner comparison #
| runZero (Recommended) |
Nmap & Zenmap | Angry IP | Masscan | |
|---|---|---|---|---|
| Best for | Continuous and scalable cyber asset management | Ad-hoc network discovery and security auditing | Scanning local network for active IPs | Research scans of the entire Internet |
| Graphical user interface |  |
 |
 |
 |
| Internal database |  |
 |
 |
 |
| Scalable deployment (distributed architecture) |  |
 |
 |
 |
| Scan by IP range (internal & external) |  |
 |
 |
 |
| Scan by domain |  |
 |
 |
 |
| Scan by ASN |  |
 |
 |
 |
| Identifies hardware platform |  |
 |
 |
 |
| Covers managed on-premise assets |  |
 |
 |
 |
| Covers unmanaged / IoT assets |  |
 |
 |
 |
| Safely scans OT assets |  |
 |
 |
 |
| Covers cloud assets |  |
 |
 |
 |
| Covers remote assets |  |
 |
 |
 |
| On-premise deployment |  |
 |
 |
 |
| SaaS deployment |  |
 |
 |
 |
| Free option available |  |
 |
 |
 |
| Paid option available |  |
 |
 |
 |
| Supported platforms | Windows, Linux, macOS, BSD |
Windows, Linux, macOS, BSD | JVM | Windows, Linux, macOS, BSD |
| Programming language | Go | C | Java | C |
runZero #
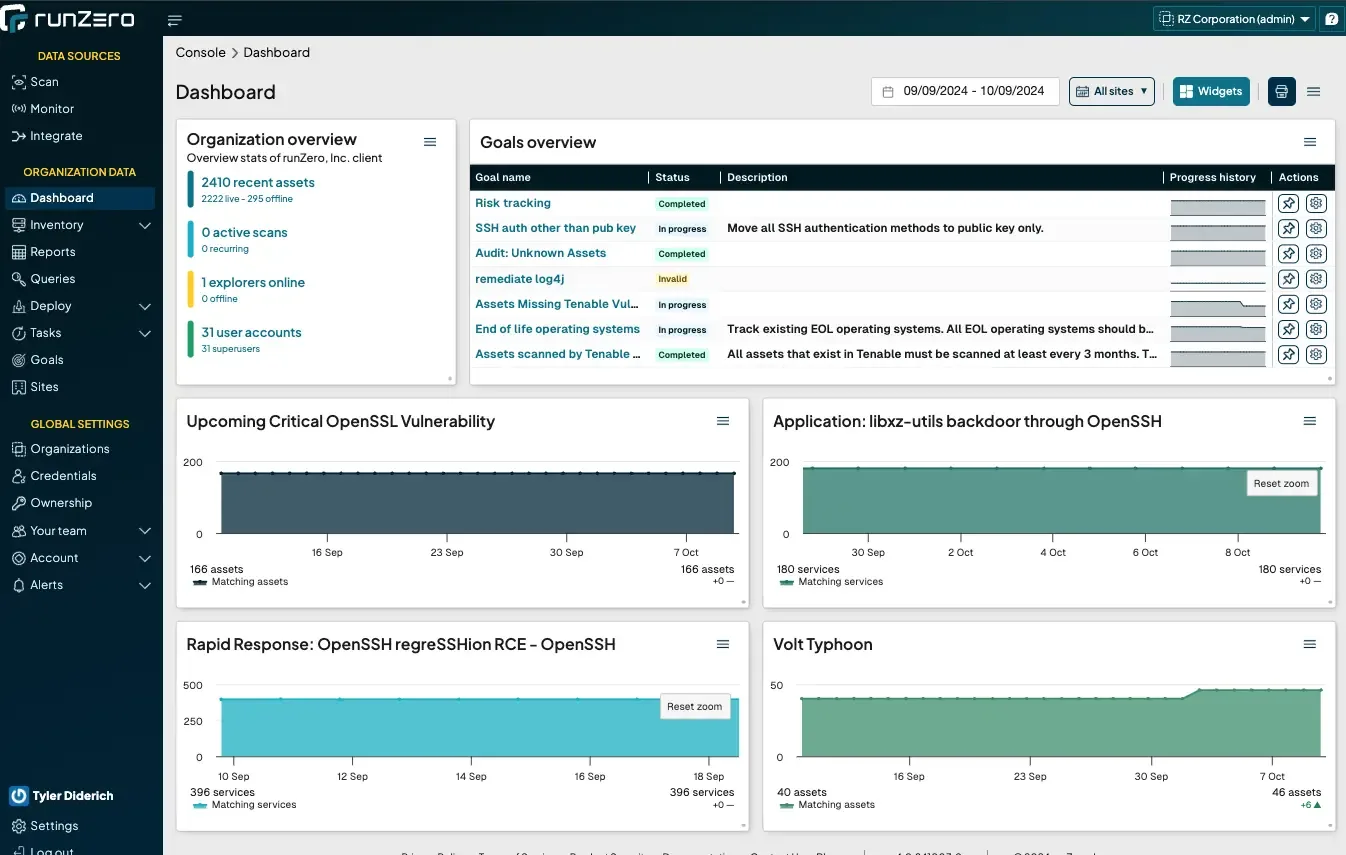
runZero was founded in 2018 by HD Moore, the creator of Metasploit, to help solve the problem of discovering both managed and unmanaged devices on the network. The product has grown to a full attack surface management solution that covers managed and unmanaged IT/IoT, OT environments, cloud assets, and remote devices. runZero offers a fully-featured 21 day trial that downgrades to a free Community Edition, which is used by more than 20,000 individuals and organizations.
runZero is enterprise grade in terms of its user interface, query language, and ability to collect an inventory even in highly distributed environments without having to write scripts or maintain a custom database. Like all of the other scanners in this article, its scans are unauthenticated but yield a surprising amount of depth of information, such as fully searchable attributes for all services, hardware and firmware details, as well as layer 2 and 3 network topologies. In addition, the solution can use SNMP credentials as well as integrations with vulnerability scanners, EDR, MDM, directories and other solutions to provide deeper insights into cyber assets and their security posture. runZero also provides integrations with CMDB and SIEM solutions to enrich asset inventory on other platforms.
runZero’s scanning technology is safe to use in many OT environments, making it an ideal passive discovery option for critical infrastructure OT environments.
| Best for |
|
| Advantages |
|
| Drawbacks |
|
Nmap and Zenmap #

Nmap has been around for 25 years and is the gold standard for ad-hoc network scanning. The free and open source utility is most often used for network discovery and security auditing. It integrates with many other security auditing tools, such as Metasploit.
Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
In addition to the classic command-line Nmap executable, the Nmap suite includes an advanced GUI and results viewer (Zenmap). The Nmap Scripting Engine (NSE) is one of Nmap's most powerful and flexible features. It allows users to write simple scripts for network discovery, more sophisticated version detection, and vulnerability detection. NSE can even be used for vulnerability exploitation.
| Best for |
|
| Advantages |
|
| Drawbacks |
|
Angry IP #

Angry IP Scanner is an open-source network scanner designed to be fast and simple to use. It scans IP addresses and ports. It is widely used by network administrators.
Angry IP is a good solution for teams that are looking for the fastest and easiest way to see which IPs are in use on a network. However the solution doesn’t provide a lot of information about each device, limited to IP, ping time, hostname, ports, TTL, MAC address, filtered ports, NetBIOS.
| Best for |
|
| Advantages |
|
| Drawbacks |
|
Masscan #

Masscan is a port scanner that can cover the entire Internet in under 5 minutes by using asynchronous transmission, sending 10 million packets per second from a single machine. It is purely a command-line tool and its usage is similar to Nmap. While Nmap is more often used to scan individual machines and smaller IP ranges, Masscan is primarily used for very large IP ranges.
| Best for |
|
| Advantages |
|
| Drawbacks |
|
Recommended network scanner for security teams: runZero #
Most free network scanners don’t scale easily out of the box, often requiring custom databases and scripts to make them suitable for continuous monitoring and collecting inventory from multiple segments or sites. Out of the mix of tools, only runZero comes with a central repository and a distributed system of Explorers to scan all parts of a network, from inside and outside the firewall.
While all of the scanners we looked at are robust and suitable for their specific use cases, runZero is the best option for corporate security teams. runZero wins on flexibility of deployment, ease of use, and scalability for larger organizations. If your security team consists of more than one person or your organization operates at more than one physical location, runZero is for you.















