runZero recently had the privilege of participating in the National Renewable Energy Lab’s (NREL) Clean Energy Cybersecurity Accelerator™ (CECA) program from the United States Department of Energy. CECA's goal is to help defend the nation's renewable energy infrastructure from cyberattacks.
CECA's Cohort 2 report featuring runZero #
They recently released their report for Cohort 2, which describes how runZero rose to the task of safely discovering devices in a large, complex Operational Technology/Industrial Control System (OT/ICS) environment.
The report describes in detail the experimental setup and comprehensive protocol used by CECA to test the runZero platform. A lab was set up with a variety of OT, ICS, and IT devices interconnected in a fashion designed to mimic how these devices are deployed in the real world. runZero explorers were then placed at strategic points around this network and scans were run using various configurations. The tests were documented in detail and constructed automatically, allowing for excellent reproducibility and documentation.
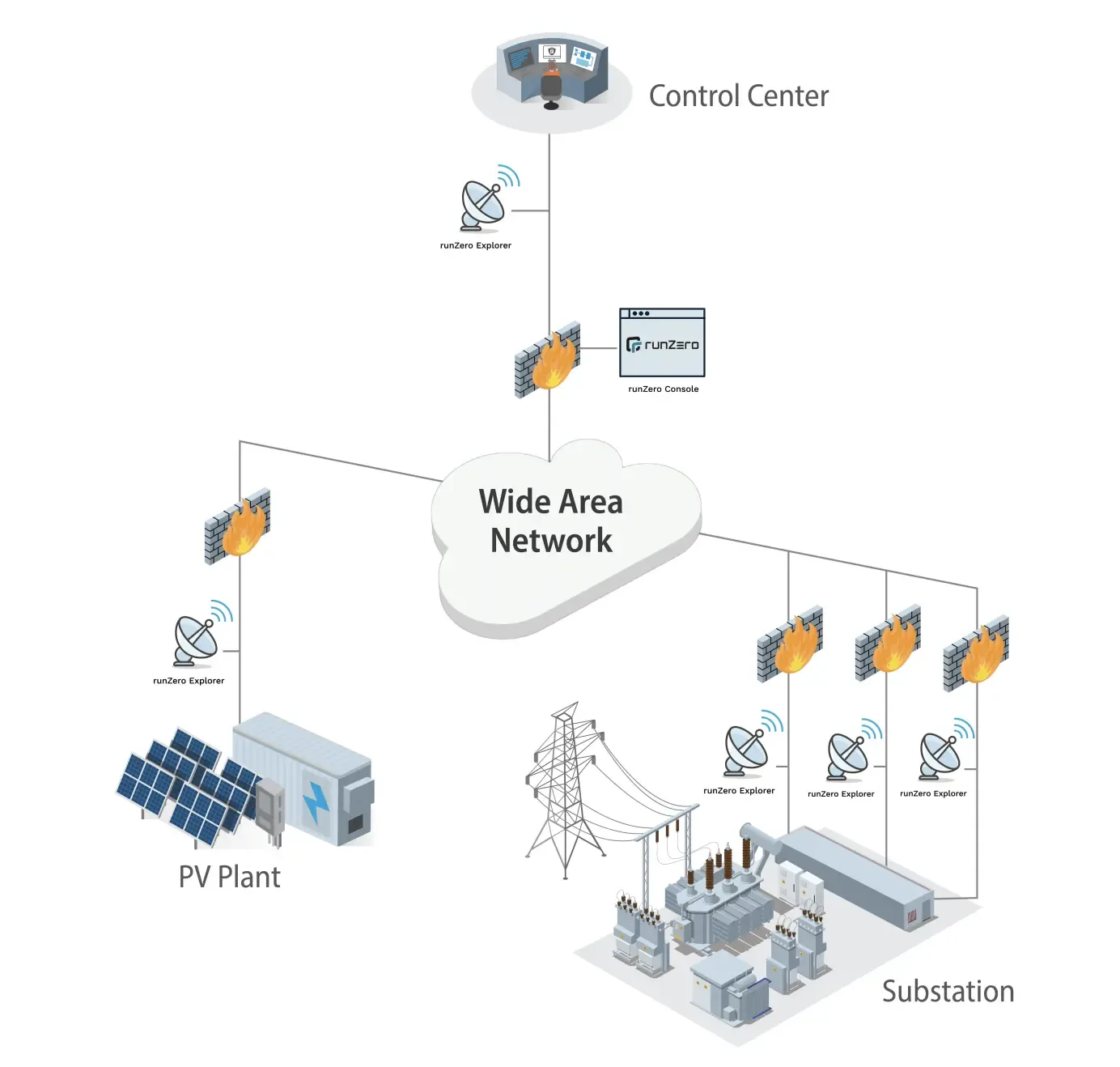
High-level overview of the PV plant and substation environment integrated with runZero
Acknowledging comprehensive asset discovery #
The report goes into great detail on the experimental setup and results, but I would like to take the opportunity to highlight a few quotes from the executive summary:
The CECA evaluations of the runZero product showed that it identified detailed information about all devices in the environment except for those which were not Internet Protocol (IP)-addressable...
runZero dedicates a huge amount of time and effort to ensure that we have the best asset discovery in the world, and it's always gratifying to see that hard work pay off. The report notes that this cohort
...sought to address the long-standing challenge of OT asset management. Industrial control system (ICS) networks often “grow organically” and so contain a rich mix of devices developed by multiple vendors over a substantial range of time. This wide variation often impedes asset owners’ ability to accurately appraise all devices (known and unknown) connected to their system at any time.
runZero makes it a point of identifying every single device we can (I consider a misidentified or unidentified asset a personal challenge). To know that we were able to identify these devices, including some that we had not personally worked with prior, was a great demonstration of our strategy to leverage multiple device identification strategies simultaneously.
OT/ICS active scanning is safe with runZero #
These strategies include support for a wide variety of network protocols, including strong support for popular (and unpopular!) OT/ICS management and monitoring protocols.
The report also goes on to say
This limited visibility inherently prevents system owners from understanding the risks in their system.
Which is like I always say: "you can't secure something you don't know you have." (The report's version sounds better.)
However, the part of the report that really made my day was this:
The evaluations also verified that runZero’s active scanning methods had no impact on the performance of the ICS assets or ongoing supervisory control and data acquisition (SCADA) processes and communications.
OT/ICS devices have a reputation for being very sensitive to unexpected or excessive network traffic. This is not unexpected: these devices are designed to dedicate most of their resources to their primary task, to be installed in a controlled environment, and to last a long time (potentially decades). Not dedicating resources to handle traffic they should never encounter doesn't seem like a bad design choice.
This sensitivity has meant that, for years, conventional wisdom has been that you should not use active scanning on OT/ICS networks. This is a shame, because active scanning really does provide a far more complete picture of a network and its assets.
runZero strongly prioritizes safety and "being a good citizen" when actively scanning networks. It allows for extremely fine-grained tuning of scanning parameters, including excluded hosts, packet rates, and protocol options. In addition to this tuning, runZero also makes it a point of only sending standards-conformant traffic to devices.
Perhaps most interestingly, as we described in our recent runZero Research Report, runZero dynamically tunes the traffic and probes that it sends as more information is learned about a given device. Only generally safe probes are sent at first, and the information returned is used to determine what further probes would be (un)safe to use.
This all led to my absolute favorite passage in the entire report:
Although the testing results are not universally generalizable, CECA’s conclusions challenge concerns with active scanning in today’s energy systems... In this CECA test environment, active scanning proved "safe," which opens the door for the use of these methods to identify substantially more information than methods that exclusively rely on passive scanning.
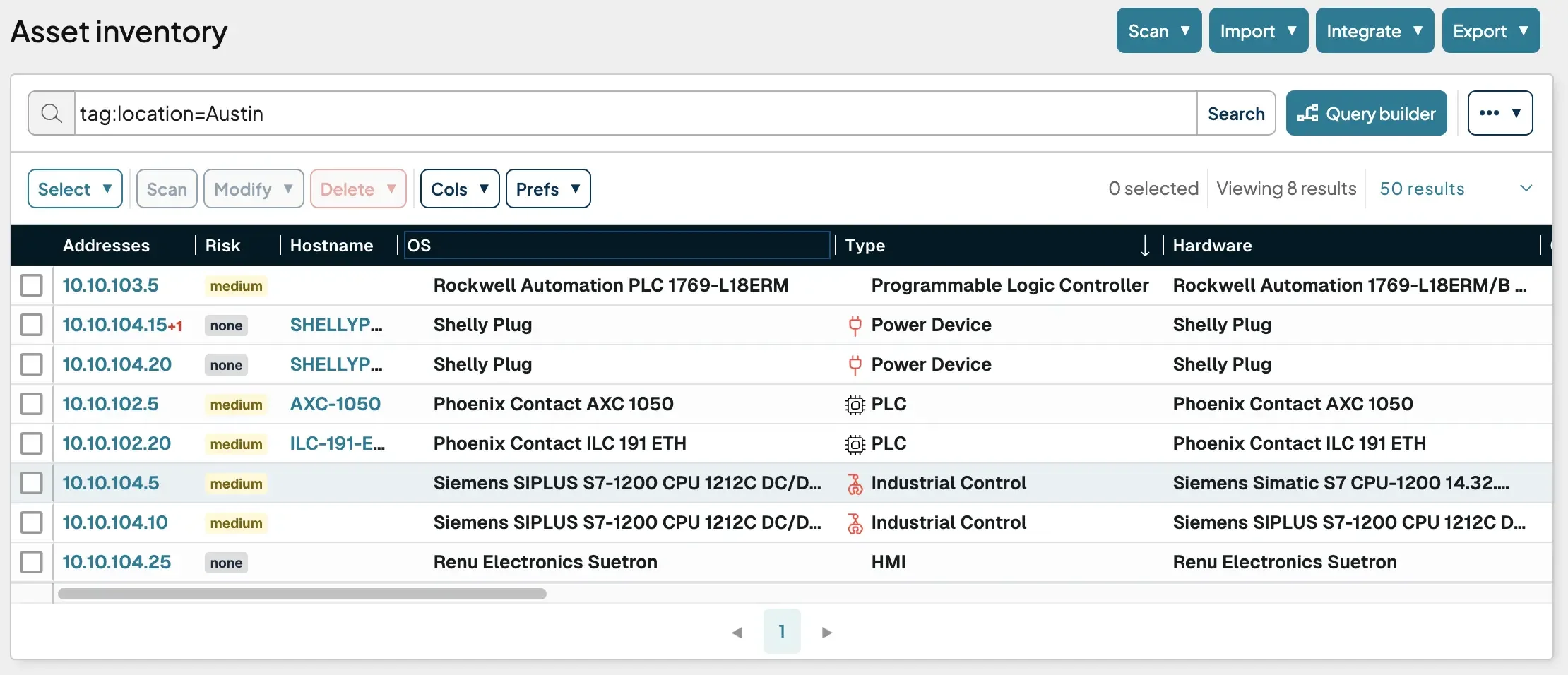
runZero asset inventory from passive collection
Our goal at runZero is to make asset discovery and attack surface management be as accurate as possible. While runZero has excellent passive discovery functionality, the fact that active discovery is proving to be safe in these environments (when done properly and with care), means that users may feel more comfortable using the full set of runZero discovery methods in their environments in the future.
For more information about scanning OT/ICS networks using runZero, please see the Scanning OT networks playbook. While runZero prioritizes stability, always be sure to test any new technology in your environment in a safe way and only use features that you're comfortable with. If you'd like to know more about runZero's passive traffic sampling for asset discovery, please see the Traffic Sampling for Passive Discovery playbook.
















